據聞今年六月八日,首度俄羅斯有一個命名為『尤金‧古斯特曼』Eugene Goostman 的『人工智慧聊天機器人』通過了圖靈測試。那麼是否一台機器通過了『圖靈測試』就能宣稱它真是具有『智慧』的呢?
二零零二年美國卡內基梅隆大學的 Luis von Ahn、Manuel Blum、Nicholas J.Hopper以及 IBM 的 John Langford 聯合提出了『CAPTCHA』── Completely Automated Public Turing test to tell Computers and Humans Apart ──。一般又叫做『驗證碼』,常常用於『□□下載』網頁,想要確認來下載的『真的是人』。它有著多種形式的設計,常見的是要使用者輸入『扭曲變形』的『文字』或是『數字』,這將使得大多數『OCR』這類圖像文字辨識軟體,無法自動判讀,所以很難寫個『軟體自動下載』。雖說都是『圖靈測試』,一者想『不能分辨』,另者要『能夠區別』,不知最終的『AI』是『能』還是『不能』的呢??
─── 《人工智慧!!》
短短一篇文章
《 How to break a CAPTCHA system in 15 minutes with Machine Learning 》
標誌了一個『新視野』
based on https://medium.com/@ageitgey/how-to-break-a-captcha-system-in-15-minutes-with-machine-learning-dbebb035a710 by https://github.com/ageitgey https://notebooks.azure.com/run/wegen…
based on https://medium.com/@ageitgey/how-to-break-a-captcha-system-in-15-minutes-with-machine-learning-dbebb035a710 by https://github.com/ageitgey
To run these scripts, you need the following installed:
,『劊客』 AI 紀元之來臨?
『指頭戰爭』的時代,所用武器乃『演算法』以及『概念發想』呦!就像
‧ 有人上網查密碼
findmyhash.py try to crack different types of hashes using free online services.
NOTE: findmyhash.py 2.0 is coming!! The new version will have many changes and improvements. Some of these changes are:
root@kali:~# python Python 2.7.15+ (default, Aug 31 2018, 11:56:52) [GCC 8.2.0] on linux2 Type "help", "copyright", "credits" or "license" for more information. >>> root@kali:~# findmyhash MD5 -h "098f6bcd4621d373cade4e832627b4f6" Cracking hash: 098f6bcd4621d373cade4e832627b4f6 Analyzing with bigtrapeze (http://www.bigtrapeze.com)... ... hash not found in bigtrapeze Analyzing with hashchecker (http://www.hashchecker.com)... ... hash not found in hashchecker Analyzing with md5hashcracker (http://md5hashcracker.appspot.com)... ... hash not found in md5hashcracker Analyzing with passcracking (http://passcracking.com)... ... hash not found in passcracking Analyzing with askcheck (http://askcheck.com)... ... hash not found in askcheck Analyzing with fox21 (http://cracker.fox21.at)... ... hash not found in fox21 Analyzing with nicenamecrew (http://crackfoo.nicenamecrew.com)... ... hash not found in nicenamecrew Analyzing with joomlaaa (http://joomlaaa.com)... ... hash not found in joomlaaa Analyzing with md5-lookup (http://md5-lookup.com)... ... hash not found in md5-lookup Analyzing with md5.com.cn (http://md5.com.cn)... ... hash not found in md5.com.cn Analyzing with digitalsun.pl (http://md5.digitalsun.pl)... ... hash not found in digitalsun.pl Analyzing with drasen.net (http://md5.drasen.net)... ... hash not found in drasen.net Analyzing with myinfosec (http://md5.myinfosec.net)... ... hash not found in myinfosec Analyzing with md5.net (http://md5.net)... ... hash not found in md5.net Analyzing with noisette.ch (http://md5.noisette.ch)... ... hash not found in noisette.ch Analyzing with md5hood (http://md5hood.com)... ... hash not found in md5hood Analyzing with stringfunction (http://www.stringfunction.com)... ... hash not found in stringfunction Analyzing with 99k.org (http://xanadrel.99k.org)... ... hash not found in 99k.org Analyzing with sans (http://isc.sans.edu)... ... hash not found in sans Analyzing with bokehman (http://bokehman.com)... ... hash not found in bokehman Analyzing with goog.li (http://goog.li)... ... hash not found in goog.li Analyzing with schwett (http://schwett.com)... ... hash not found in schwett Analyzing with netmd5crack (http://www.netmd5crack.com)... ... hash not found in netmd5crack Analyzing with md5-cracker (http://www.md5-cracker.tk)... ... hash not found in md5-cracker Analyzing with benramsey (http://tools.benramsey.com)... ... hash not found in benramsey Analyzing with gromweb (http://md5.gromweb.com)... ... hash not found in gromweb Analyzing with hashcracking (http://md5.hashcracking.com)... ... hash not found in hashcracking Analyzing with hashcracking (http://victorov.su)... ... hash not found in hashcracking Analyzing with thekaine (http://md5.thekaine.de)... ... hash not found in thekaine Analyzing with tmto (http://www.tmto.org)... ... hash not found in tmto Analyzing with rednoize (http://md5.rednoize.com)... ... hash not found in rednoize Analyzing with md5-db (http://md5-db.de)... ... hash not found in md5-db Analyzing with my-addr (http://md5.my-addr.com)... ***** HASH CRACKED!! ***** The original string is: test The following hashes were cracked: ---------------------------------- 098f6bcd4621d373cade4e832627b4f6 -> test
‧ 有人方便窮舉
Simple brute forcing in Python.
Simple brute forcing in Python.
Brute forcing passwords, and other things often requires a bit of hacking to get working properly.
This library makes generating all possible permutations of strings really easy — and is very customizable.
You can then brute force whatever you want, however you want >:)
root@kali:~# python Python 2.7.15+ (default, Aug 31 2018, 11:56:52) [GCC 8.2.0] on linux2 Type "help", "copyright", "credits" or "license" for more information. >>> from brute import brute >>> n = 0 >>> for s in brute(): ... n = n + 1 ... >>> print n 839514 >>>
‧ 也有人綜合發展
A Python Script For BrtuForce Attack On Multi HASHES YOU CAN BRTU-FORCE ATTACK ON THIS HASHES [ MD5, SHA1, SHA224, SHA256, SHA384, SHA512 ] Using this Script 🙂
root@kali:~/test/HASHCat# ./HASHCat.py -H 5eb63bbbe01eeed093cb22bb8f5acdc3 -W ../rockyou.txt
__ __ ______ ______ __ __ ______ ______ ______
/\ \_\ \ /\ __ \ /\ ___\ /\ \_\ \ /\ ___\ /\ __ \ /\__ _\
\ \ __ \ \ \ __ \ \ \___ \ \ \ __ \ \ \ \____ \ \ __ \ \/_/\ \/
\ \_\ \_\ \ \_\ \_\ \/\_____\ \ \_\ \_\ \ \_____\ \ \_\ \_\ \ \_\
\/_/\/_/ \/_/\/_/ \/_____/ \/_/\/_/ \/_____/ \/_/\/_/ \/_/
---------------------------------------------------------------------
[+>]=====>> By: Oseid Aldary <<=====[-]====>> Version: 2.5 <<====[<+]
---------------------------------------------------------------------
[+>]<====================> CONFIG <====================>[<+]
[*] HASH NAME :> [ MD5
[+] HASH :> [ 5eb63bbbe01eeed093cb22bb8f5acd-...
[>] Wordlist :> [ ../rockyou.txt
[@] Words Loaded :> [ 14344392
...
[!]:Trying Password[933478] : hello!!!!
[+]:HASH CRACK!:
[*]:INFO:
----------
[*]:HASH Name:[ MD5 ]
[+]:HASH:[ 5eb63bbbe01eeed093cb22bb8f5acdc3 ]
[#>]:HASH CAT:[ hello world ]
或希望『素客』們,不要掉以輕心的啊☆★
如果知道
World’s fastest and most advanced password recovery utility https://hashcat.net/hashcat/
hashcat is the world’s fastest and most advanced password recovery utility, supporting five unique modes of attack for over 200 highly-optimized hashing algorithms. hashcat currently supports CPUs, GPUs, and other hardware accelerators on Linux, Windows, and macOS, and has facilities to help enable distributed password cracking.
hashcat is licensed under the MIT license. Refer to docs/license.txt for more information.
恐因樹莓派『GPU』之故︰
無法『安裝』,果然以為『好事』耶?怕不知『劊客』肚腸哩!
沒有『快意我攻』之環境,所以才『起心動念』呦!?
難道他不會『揣摩』何謂
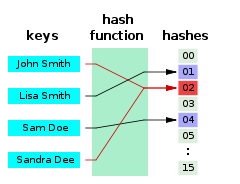
A hash function that maps names to integers from 0 to 15. There is a collision between keys “John Smith” and “Sandra Dee”.
A hash function is any function that can be used to map data of arbitrary size to data of a fixed size. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. Hash functions are often used in combination with a hash table, a common data structure used in computer software for rapid data lookup. Hash functions accelerate table or database lookup by detecting duplicated records in a large file. One such application is finding similar stretches in DNA sequences. They are also useful in cryptography. A cryptographic hash function allows one to easily verify that some input data maps to a given hash value, but if the input data is unknown, it is deliberately difficult to reconstruct it (or any equivalent alternatives) by knowing the stored hash value. This is used for assuring integrity of transmitted data, and is the building block for HMACs, which provide message authentication.
Hash functions are related to (and often confused with) checksums, check digits, fingerprints, lossy compression, randomization functions, error-correcting codes, and ciphers. Although the concepts overlap to some extent, each one has its own uses and requirements and is designed and optimized differently. The HashKeeper database maintained by the American National Drug Intelligence Center, for instance, is more aptly described as a catalogue of file fingerprints than of hash values.
『嘗試』如何加味嗎?!
In cryptography, a salt is random data that is used as an additional input to a one-way function that “hashes” data, a password or passphrase. Salts are used to safeguard passwords in storage. Historically a password was stored in plaintext on a system, but over time additional safeguards developed to protect a user’s password against being read from the system. A salt is one of those methods.
A new salt is randomly generated for each password. In a typical setting, the salt and the password (or its version after Key stretching) are concatenated and processed with a cryptographic hash function, and the resulting output (but not the original password) is stored with the salt in a database. Hashing allows for later authentication without keeping and therefore risking the plaintext password in the event that the authentication data store is compromised.
Salts defend against dictionary attacks or against their hashed equivalent, a pre-computed rainbow table attack.[1] Since salts do not have to be memorized by humans they can make the size of the rainbow table required for a successful attack prohibitively large without placing a burden on the users. Since salts are different in each case, they also protect commonly used passwords, or those users who use the same password on several sites, by making all salted hash instances for the same password different from each other.
Cryptographic salts are broadly used in many modern computer systems, from Unix system credentials to Internet security.
Salts are closely related to the concept of a cryptographic nonce.
故而自許『素客』者,務須『深研』呀◎
藉著
hashlib — Secure hashes and message digests
Source code: Lib/hashlib.py
This module implements a common interface to many different secure hash and message digest algorithms. Included are the FIPS secure hash algorithms SHA1, SHA224, SHA256, SHA384, and SHA512 (defined in FIPS 180-2) as well as RSA’s MD5 algorithm (defined in Internet RFC 1321). The terms “secure hash” and “message digest” are interchangeable. Older algorithms were called message digests. The modern term is secure hash.
Note
If you want the adler32 or crc32 hash functions, they are available in the zlib module.
Warning
Some algorithms have known hash collision weaknesses, refer to the “See also” section at the end.
There is one constructor method named for each type of hash. All return a hash object with the same simple interface. For example: use sha256() to create a SHA-256 hash object. You can now feed this object with bytes-like objects (normally bytes) using the update() method. At any point you can ask it for the digest of the concatenation of the data fed to it so far using the digest() or hexdigest() methods.
Note
For better multithreading performance, the Python GIL is released for data larger than 2047 bytes at object creation or on update.
Note
Feeding string objects into update() is not supported, as hashes work on bytes, not on characters.
Constructors for hash algorithms that are always present in this module are sha1(), sha224(), sha256(), sha384(),sha512(), blake2b(), and blake2s(). md5() is normally available as well, though it may be missing if you are using a rare “FIPS compliant” build of Python. Additional algorithms may also be available depending upon the OpenSSL library that Python uses on your platform. On most platforms the sha3_224(), sha3_256(), sha3_384(), sha3_512(),shake_128(), shake_256() are also available.
New in version 3.6: SHA3 (Keccak) and SHAKE constructors sha3_224(), sha3_256(), sha3_384(), sha3_512(),shake_128(), shake_256().
『程式庫』,經由
We’re happy to announce Passlib 1.7.1. The 1.7 series has been a while in coming, and has a lot of great improvements…
See the release notes for more details.
Passlib is a password hashing library for Python 2 & 3, which provides cross-platform implementations of over 30 password hashing algorithms, as well as a framework for managing existing password hashes. It’s designed to be useful for a wide range of tasks, from verifying a hash found in /etc/shadow, to providing full-strength password hashing for multi-user application.
『原始碼』的『學習』︰
class sha512_crypt(_SHA2_Common):
"""This class implements the SHA512-Crypt password hash, and follows the :ref:`password-hash-api`.
It supports a variable-length salt, and a variable number of rounds.
The :meth:`~passlib.ifc.PasswordHash.using` method accepts the following optional keywords:
:type salt: str
:param salt:
Optional salt string.
If not specified, one will be autogenerated (this is recommended).
If specified, it must be 0-16 characters, drawn from the regexp range ``[./0-9A-Za-z]``.
:type rounds: int
:param rounds:
Optional number of rounds to use.
Defaults to 656000, must be between 1000 and 999999999, inclusive.
:type implicit_rounds: bool
:param implicit_rounds:
this is an internal option which generally doesn't need to be touched.
this flag determines whether the hash should omit the rounds parameter
when encoding it to a string; this is only permitted by the spec for rounds=5000,
and the flag is ignored otherwise. the spec requires the two different
encodings be preserved as they are, instead of normalizing them.
:type relaxed: bool
:param relaxed:
By default, providing an invalid value for one of the other
keywords will result in a :exc:`ValueError`. If ``relaxed=True``,
and the error can be corrected, a :exc:`~passlib.exc.PasslibHashWarning`
will be issued instead. Correctable errors include ``rounds``
that are too small or too large, and ``salt`` strings that are too long.
.. versionadded:: 1.6
"""
root@kali:~# python3 Python 3.6.6 (default, Jun 27 2018, 14:44:17) [GCC 8.1.0] on linux Type "help", "copyright", "credits" or "license" for more information. >>> import passlib.hash, crypt >>> 密碼樣態 = "6" >>> 加密鹽 = "zWfdesqL" >>> 加密格式 = '{}
6
W37U8bi4X4TBfCBbpl0Xg3igJmJpZaRLjkmEceZudlf6OJ/.BVglCb1Z8VUFpXT.mpw6FUUyqP6qZZmx9VqMh.' >>> >>> 雜湊二 = crypt.crypt(密碼,加密格式) >>> 雜湊二 '
zWfdesqL$W37U8bi4X4TBfCBbpl0Xg3igJmJpZaRLjkmEceZudlf6OJ/.BVglCb1Z8VUFpXT.mpw6FUUyqP6qZZmx9VqMh.' >>> 雜湊一 == 雜湊二 True >>>
通達密碼『演算法』強弱之旨也☆
crypt — Function to check Unix passwordsSource code: Lib/crypt.py
This module implements an interface to the crypt(3) routine, which is a one-way hash function based upon a modified DES algorithm; see the Unix man page for further details. Possible uses include storing hashed passwords so you can check passwords without storing the actual password, or attempting to crack Unix passwords with a dictionary.
Notice that the behavior of this module depends on the actual implementation of the crypt(3) routine in the running system. Therefore, any extensions available on the current implementation will also be available on this module.
New in version 3.3.
The crypt module defines the list of hashing methods (not all methods are available on all platforms):
crypt.METHOD_SHA512crypt.METHOD_SHA256crypt.METHOD_BLOWFISHNew in version 3.7.
crypt.METHOD_MD5crypt.METHOD_CRYPT
一時想起派生的『非同步計算』架構建議
This PEP proposes a design for a package that facilitates the evaluation of callables using threads and processes.
Python currently has powerful primitives to construct multi-threaded and multi-process applications but parallelizing simple operations requires a lot of work i.e. explicitly launching processes/threads, constructing a work/results queue, and waiting for completion or some other termination condition (e.g. failure, timeout). It is also difficult to design an application with a global process/thread limit when each component invents its own parallel execution strategy.
───
,以及『 SCOOP 』 Python 『分佈式』可擴張『並行運算』平台,
SCOOP (Scalable COncurrent Operations in Python) is a distributed task module allowing concurrent parallel programming on various environments, from heterogeneous grids to supercomputers.
Our philosophy is based on these ideas:
- The future is parallel;
- Simple is beautiful;
- Parallelism should be simpler.
These tenets are translated concretely in a minimum number of functions allowing maximum parallel efficiency while keeping at minimum the inner knowledge required to use them. It is implemented with Python 3 in mind while being compatible with 2.6+ to allow fast prototyping without sacrificing efficiency and speed.
SCOOP has many features and advantages over Futures, multiprocessing and similar modules, such as:
- Harness the power of multiple computers over network;
- Ability to spawn subtasks within tasks;
- API compatible with PEP 3148;
- Parallelizing serial programs with only minor modifications;
- Efficient load-balancing.
SCOOP can handle multiple diversified multi-layered tasks. You can submit your different functions and data simultaneously and effortlessly while the framework executes them locally or remotely. Contrarily to most multiprocessing frameworks, it allows to launch subtasks within tasks.
 Through SCOOP, you can simultaneously execute tasks that are of different nature (Discs of different colors) or different by complexity (Discs radiuses). The module will handle the physical considerations of parallelization such as task distribution over your resources (load balancing), communications, etc.
Through SCOOP, you can simultaneously execute tasks that are of different nature (Discs of different colors) or different by complexity (Discs radiuses). The module will handle the physical considerations of parallelization such as task distribution over your resources (load balancing), communications, etc.
The common applications of SCOOP consist of, but is not limited to:
- Evolutionary Algorithms
- Monte Carlo simulations
- Data mining
- Data processing
- I/O processing
- Graph traversal
───
也許如是方能將『一萬臺樹莓派』給組織起來,真可以同時協作的吧?畢竟根本不知那『 It 網』的構造方式原理,即使想問也不知該從何問起的哩!
─── 《勇闖新世界︰ W!O《卡夫卡村》變形祭︰感知自然‧尖端‧六上》
xkcd/936 上的簡短漫畫︰

A webcomic of romance,
sarcasm, math, and language.
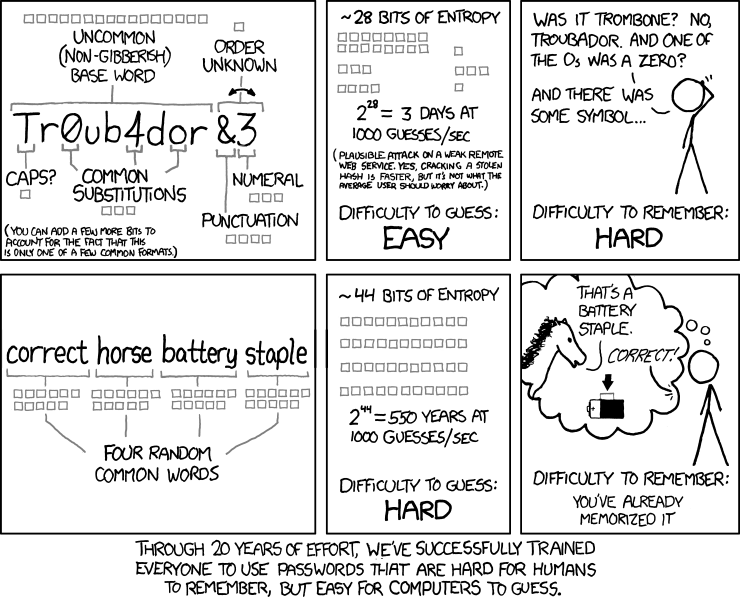
笑話人『難』記,電腦『易』猜之『密碼』?
俗話說︰時間即金錢。
恰是那個『難』『易』的『尺度』哩!
切莫以此為『心』『安』!?
怎知『劊客』他不擅長『讀心術』呢?!
root@kali:~/test# unshadow /etc/passwd /etc/shadow > passwords.txt root@kali:~/test# john passwords.txt Created directory: /root/.john Using default input encoding: UTF-8 Loaded 1 password hash (sha512crypt, crypt(3)[SHA512 64/32 OpenSSL]) Press 'q' or Ctrl-C to abort, almost any other key for status toor (root) 1g 0:00:00:00 DONE 1/3 (2018-10-26 08:45) 4.761g/s 33.33p/s 33.33c/s 33.33C/s toor Use the "--show" option to display all of the cracked passwords reliably Session completed root@kali:~/test# john --show passwords.txt root:toor:0:0:root:/root:/bin/bash 1 password hash cracked, 0 left
※ 註︰
This is the mode you should start cracking with. It will use the login names, “GECOS” / “Full Name” fields, and users’ home directory names as candidate passwords, also with a large set of mangling rules applied. Since the information is only used against passwords for the accounts it was taken from (and against password hashes which happened to be assigned the same salt), “single crack” mode is much faster than wordlist mode. This permits for the use of a much larger set of word mangling rules with “single crack”, and their use is always enabled with this mode. Successfully guessed passwords are also tried against all loaded password hashes just in case more users have the same password.
Note that running this mode on many password files simultaneously may sometimes get more passwords cracked than it would if you ran it on the individual password files separately.
萬一他還有 SCoOP 組成之『超級電腦』網絡,又精通『資料探勘』耶☻
| Download | PACK-0.0.4.tar.gz |
|---|---|
| Size | 68.8 KB |
| Date | August 8th, 2013 |
| Version | 0.0.4 |
PACK (Password Analysis and Cracking Toolkit) is a collection of utilities developed to aid in analysis of password lists in order to enhance password cracking through pattern detection of masks, rules, character-sets and other password characteristics. The toolkit generates valid input files for Hashcat family of password crackers.
NOTE: The toolkit itself is not able to crack passwords, but instead designed to make operation of password crackers more efficient.
Table of Contents
Before we can begin using the toolkit we must establish a selection criteria of password lists. Since we are looking to analyze the way people create their passwords, we must obtain as large of a sample of leaked passwords as possible. One such excellent list is based on RockYou.com compromise. This list both provides large and diverse enough collection that provides a good results for common passwords used by similar sites (e.g. social networking). The analysis obtained from this list may not work for organizations with specific password policies. As such, selecting sample input should be as close to your target as possible. In addition, try to avoid obtaining lists based on already cracked passwords as it will generate statistics bias of rules and masks used by individual(s) cracking the list and not actual users.
問『鹿』死誰手?眼下結果不分明呦★
The most basic analysis that you can perform is simply obtaining most common length, character-set and other characteristics of passwords in the provided list. In the example below, we will use ‘rockyou.txt’ containing approximately 14 million passwords. Launch statsgen.pywith the following command line:
$ python statsgen.py rockyou.txt
Below is the output from the above command:
root@kali:~/test# statsgen rockyou.txt
_
StatsGen 0.0.3 | |
_ __ __ _ ___| | _
| '_ \ / _` |/ __| |/ /
| |_) | (_| | (__| <
| .__/ \__,_|\___|_|\_\
| |
|_| iphelix@thesprawl.org
[*] Analyzing passwords in [rockyou.txt]
[+] Analyzing 100% (14344391/14344391) of passwords
NOTE: Statistics below is relative to the number of analyzed passwords, not total number of passwords
[*] Length:
[+] 8: 20% (2966037)
[+] 7: 17% (2506271)
[+] 9: 15% (2191040)
[+] 10: 14% (2013695)
[+] 6: 13% (1947798)
[+] 11: 06% (866035)
[+] 12: 03% (555350)
[+] 13: 02% (364174)
[+] 5: 01% (259169)
[+] 14: 01% (248527)
[+] 15: 01% (161213)
[+] 16: 00% (118406)
[+] 17: 00% (36884)
[+] 18: 00% (23769)
[+] 4: 00% (17899)
[+] 19: 00% (15567)
[+] 20: 00% (13069)
[+] 21: 00% (7850)
[+] 22: 00% (6156)
[+] 23: 00% (4849)
[+] 24: 00% (4237)
[+] 25: 00% (2950)
[+] 3: 00% (2461)
[+] 26: 00% (2249)
[+] 27: 00% (1811)
[+] 28: 00% (1198)
[+] 30: 00% (992)
[+] 29: 00% (785)
[+] 255: 00% (476)
[+] 31: 00% (469)
[+] 32: 00% (407)
[+] 2: 00% (335)
[+] 33: 00% (296)
[+] 34: 00% (193)
[+] 36: 00% (188)
[+] 35: 00% (131)
[+] 39: 00% (118)
[+] 37: 00% (81)
[+] 42: 00% (81)
[+] 38: 00% (67)
[+] 45: 00% (56)
[+] 40: 00% (55)
[+] 41: 00% (46)
[+] 1: 00% (45)
[+] 71: 00% (45)
[+] 43: 00% (43)
[+] 48: 00% (40)
[+] 44: 00% (31)
[+] 55: 00% (28)
[+] 54: 00% (27)
[+] 50: 00% (26)
[+] 46: 00% (25)
[+] 47: 00% (23)
[+] 69: 00% (23)
[+] 51: 00% (22)
[+] 61: 00% (21)
[+] 60: 00% (20)
[+] 49: 00% (18)
[+] 58: 00% (18)
[+] 56: 00% (17)
[+] 57: 00% (17)
[+] 64: 00% (17)
[+] 52: 00% (16)
[+] 53: 00% (16)
[+] 63: 00% (16)
[+] 70: 00% (16)
[+] 222: 00% (15)
[+] 66: 00% (12)
[+] 67: 00% (12)
[+] 74: 00% (12)
[+] 75: 00% (11)
[+] 59: 00% (9)
[+] 84: 00% (9)
[+] 62: 00% (8)
[+] 68: 00% (8)
[+] 72: 00% (8)
[+] 65: 00% (7)
[+] 73: 00% (7)
[+] 80: 00% (7)
[+] 76: 00% (6)
[+] 79: 00% (6)
[+] 81: 00% (6)
[+] 101: 00% (6)
[+] 246: 00% (6)
[+] 78: 00% (5)
[+] 87: 00% (5)
[+] 210: 00% (5)
[+] 219: 00% (5)
[+] 77: 00% (4)
[+] 82: 00% (4)
[+] 85: 00% (4)
[+] 88: 00% (4)
[+] 96: 00% (4)
[+] 117: 00% (4)
[+] 129: 00% (4)
[+] 150: 00% (4)
[+] 221: 00% (4)
[+] 83: 00% (3)
[+] 91: 00% (3)
[+] 94: 00% (3)
[+] 95: 00% (3)
[+] 108: 00% (3)
[+] 125: 00% (3)
[+] 142: 00% (3)
[+] 146: 00% (3)
[+] 165: 00% (3)
[+] 188: 00% (3)
[+] 220: 00% (3)
[+] 224: 00% (3)
[+] 232: 00% (3)
[+] 243: 00% (3)
[+] 90: 00% (2)
[+] 92: 00% (2)
[+] 98: 00% (2)
[+] 102: 00% (2)
[+] 103: 00% (2)
[+] 104: 00% (2)
[+] 109: 00% (2)
[+] 111: 00% (2)
[+] 113: 00% (2)
[+] 123: 00% (2)
[+] 124: 00% (2)
[+] 134: 00% (2)
[+] 154: 00% (2)
[+] 173: 00% (2)
[+] 178: 00% (2)
[+] 182: 00% (2)
[+] 190: 00% (2)
[+] 194: 00% (2)
[+] 195: 00% (2)
[+] 197: 00% (2)
[+] 207: 00% (2)
[+] 208: 00% (2)
[+] 216: 00% (2)
[+] 217: 00% (2)
[+] 218: 00% (2)
[+] 225: 00% (2)
[+] 226: 00% (2)
[+] 228: 00% (2)
[+] 237: 00% (2)
[+] 238: 00% (2)
[+] 239: 00% (2)
[+] 241: 00% (2)
[+] 249: 00% (2)
[+] 254: 00% (2)
[+] 257: 00% (2)
[+] 262: 00% (2)
[+] 86: 00% (1)
[+] 89: 00% (1)
[+] 93: 00% (1)
[+] 97: 00% (1)
[+] 99: 00% (1)
[+] 100: 00% (1)
[+] 105: 00% (1)
[+] 106: 00% (1)
[+] 115: 00% (1)
[+] 118: 00% (1)
[+] 126: 00% (1)
[+] 131: 00% (1)
[+] 132: 00% (1)
[+] 133: 00% (1)
[+] 137: 00% (1)
[+] 138: 00% (1)
[+] 141: 00% (1)
[+] 145: 00% (1)
[+] 148: 00% (1)
[+] 149: 00% (1)
[+] 151: 00% (1)
[+] 153: 00% (1)
[+] 162: 00% (1)
[+] 168: 00% (1)
[+] 170: 00% (1)
[+] 171: 00% (1)
[+] 172: 00% (1)
[+] 174: 00% (1)
[+] 175: 00% (1)
[+] 176: 00% (1)
[+] 184: 00% (1)
[+] 189: 00% (1)
[+] 192: 00% (1)
[+] 198: 00% (1)
[+] 200: 00% (1)
[+] 202: 00% (1)
[+] 203: 00% (1)
[+] 204: 00% (1)
[+] 206: 00% (1)
[+] 209: 00% (1)
[+] 211: 00% (1)
[+] 213: 00% (1)
[+] 230: 00% (1)
[+] 231: 00% (1)
[+] 233: 00% (1)
[+] 234: 00% (1)
[+] 240: 00% (1)
[+] 242: 00% (1)
[+] 244: 00% (1)
[+] 245: 00% (1)
[+] 248: 00% (1)
[+] 251: 00% (1)
[+] 252: 00% (1)
[+] 258: 00% (1)
[+] 266: 00% (1)
[+] 285: 00% (1)
[*] Character-set:
[+] loweralphanum: 42% (6074867)
[+] loweralpha: 25% (3726129)
[+] numeric: 16% (2346744)
[+] loweralphaspecialnum: 02% (426353)
[+] upperalphanum: 02% (407431)
[+] mixedalphanum: 02% (382237)
[+] loweralphaspecial: 02% (381623)
[+] upperalpha: 01% (229875)
[+] mixedalpha: 01% (159310)
[+] all: 00% (53238)
[+] mixedalphaspecial: 00% (49655)
[+] specialnum: 00% (46606)
[+] upperalphaspecialnum: 00% (27737)
[+] upperalphaspecial: 00% (26813)
[+] special: 00% (5773)
[*] Password complexity:
[+] digit: min(0) max(255)
[+] lower: min(0) max(255)
[+] upper: min(0) max(187)
[+] special: min(0) max(255)
[*] Simple Masks:
[+] stringdigit: 37% (5339556)
[+] string: 28% (4115314)
[+] digit: 16% (2346744)
[+] digitstring: 04% (663951)
[+] othermask: 04% (576325)
[+] stringdigitstring: 03% (450742)
[+] stringspecialstring: 01% (204441)
[+] stringspecialdigit: 01% (167816)
[+] stringspecial: 01% (148328)
[+] digitstringdigit: 00% (130517)
[+] stringdigitspecial: 00% (77378)
[+] specialstringspecial: 00% (25127)
[+] digitspecialstring: 00% (16821)
[+] specialstring: 00% (14496)
[+] digitstringspecial: 00% (12242)
[+] digitspecialdigit: 00% (12114)
[+] digitspecial: 00% (11017)
[+] specialstringdigit: 00% (9609)
[+] specialdigitstring: 00% (8328)
[+] special: 00% (5773)
[+] specialdigit: 00% (4142)
[+] specialdigitspecial: 00% (3610)
[*] Advanced Masks:
[+] ?l?l?l?l?l?l?l?l: 04% (687991)
[+] ?l?l?l?l?l?l: 04% (601152)
[+] ?l?l?l?l?l?l?l: 04% (585013)
[+] ?l?l?l?l?l?l?l?l?l: 03% (516830)
[+] ?d?d?d?d?d?d?d: 03% (487429)
[+] ?d?d?d?d?d?d?d?d?d?d: 03% (478196)
[+] ?d?d?d?d?d?d?d?d: 02% (428296)
[+] ?l?l?l?l?l?l?d?d: 02% (420318)
[+] ?l?l?l?l?l?l?l?l?l?l: 02% (416939)
[+] ?d?d?d?d?d?d: 02% (390529)
[+] ?d?d?d?d?d?d?d?d?d: 02% (307532)
[+] ?l?l?l?l?l?d?d: 02% (292306)
[+] ?l?l?l?l?l?l?l?d?d: 01% (273624)
[+] ?l?l?l?l?l?l?l?l?l?l?l: 01% (267733)
[+] ?l?l?l?l?d?d?d?d: 01% (235360)
[+] ?l?l?l?l?d?d: 01% (215074)
[+] ?l?l?l?l?l?l?l?l?d?d: 01% (213109)
[+] ?l?l?l?l?l?l?d: 01% (193097)
[+] ?l?l?l?l?l?l?l?d: 01% (189847)
[+] ?l?l?l?l?l?l?l?l?l?l?l?l: 01% (189355)
[+] ?l?l?l?d?d?d?d: 01% (178304)
[+] ?l?l?l?l?l?d?d?d?d: 01% (173559)
[+] ?l?l?l?l?l?l?d?d?d?d: 01% (160592)
[+] ?l?l?l?l?l?l?l?l?d: 01% (160054)
[+] ?l?l?l?l?l?d?d?d: 01% (152400)
何謂『資安問題』呢?這樣模糊隴統問法,無法回答也。比方說 Unix 裡有個『無名氏』使用者︰
In many Unix variants, “nobody” is the conventional name of a user account which owns no files, is in no privileged groups, and has no abilities except those which every other user has. Some systems also define an equivalent group “nogroup“.
難到可講因他的『妥協』 Compromise ?導致了『信息外洩』嘛!
常常複雜系統『設計』之『目的』與『應用』的『結果』差異頗大的呦!?
舉例而言,系統『管理者』正面看待『密碼檔』之變革︰
passwd is a tool on most Unix and Unix-like operating systems used to change a user’s password. The password entered by the user is run through a key derivation function to create a hashed version of the new password, which is saved. Only the hashed version is stored; the entered password is not saved for security reasons.
When the user logs on, the password entered by the user during the log on process is run through the same key derivation function and the resulting hashed version is compared with the saved version. If the hashes are identical, the entered password is considered to be correct, and the user is authenticated. In theory, it is possible for two different passwords to produce the same hash. However, cryptographic hash functions are designed in such a way that finding any password that produces the same hash is very difficult and practically infeasible, so if the produced hash matches the stored one, the user can be authenticated.
The passwd command may be used to change passwords for local accounts, and on most systems, can also be used to change passwords managed in a distributed authentication mechanism such as NIS, Kerberos, or LDAP.
The /etc/passwd file is a text-based database of information about users that may loginto the system or other operating system user identities that own running processes.
In many operating systems this file is just one of many possible back-ends for the more general passwd name service.
The file’s name originates from one of its initial functions as it contained the data used to verify passwords of user accounts. However, on modern Unix systems the security-sensitive password information is instead often stored in a different file using shadow passwords, or other database implementations.
The /etc/passwd file typically has file system permissions that allow it to be readable by all users of the system (world-readable), although it may only be modified by the superuser or by using a few special purpose privileged commands.
The /etc/passwd file is a text file with one record per line, each describing a user account. Each record consists of seven fields separated by colons. The ordering of the records within the file is generally unimportant.
An example record may be:
jsmith:x:1001:1000:Joe Smith,Room 1007,(234)555-8910,(234)555-0044,email:/home/jsmith:/bin/sh
The fields, in order from left to right, are:[1]
/etc/shadow is used to increase the security level of passwords by restricting all but highly privileged users’ access to hashed password data. Typically, that data is kept in files owned by and accessible only by the super user.
Systems administrators can reduce the likelihood of brute-force attacks by making the list of hashed passwords unreadable by unprivileged users. The obvious way to do this is to make the passwd database itself readable only by the root user. However, this would restrict access to other data in the file such as username-to-userid mappings, which would break many existing utilities and provisions. One solution is a “shadow” password file to hold the password hashes separate from the other data in the world-readable passwdfile. For local files, this is usually /etc/shadow on Linux and Unix systems, or /etc/master.passwd on BSD systems; each is readable only by root. (Root access to the data is considered acceptable since on systems with the traditional “all-powerful root” security model, the root user would be able to obtain the information in other ways in any case). Virtually all recent Unix-like operating systems use shadowed passwords.
The shadow password file does not entirely solve the problem of attacker access to hashed passwords, as some network authentication schemes operate by transmitting the hashed password over the network (sometimes in cleartext, e.g., Telnet[3]), making it vulnerable to interception. Copies of system data, such as system backups written to tape or optical media, can also become a means for illicitly obtaining hashed passwords. In addition, the functions used by legitimate password-checking programs need to be written in such a way that malicious programs cannot make large numbers of authentication checks at high rates of speed.
Regardless of whether password shadowing is in effect on a given system, the passwd file is readable by all users so that various system utilities (e.g., ls) can work (e.g., to ensure that user names are shown when the user lists the contents of a folder), while only the root user can write to it. Without password shadowing, this means that an attacker with unprivileged access to the system can obtain the hashed form of every user’s password. Those values can be used to mount a brute force attack offline, testing possible passwords against the hashed passwords relatively quickly without alerting system security arrangements designed to detect an abnormal number of failed login attempts. Especially when the hash is not salted it is also possible to look up these hashed passwords in rainbow tables, databases specially made for giving back a password for a unique hash.
With a shadowed password scheme in use, the /etc/passwd file typically shows a character such as ‘*‘, or ‘x‘ in the password field for each user instead of the hashed password, and /etc/shadow usually contains the following user information:
1$” stands for MD5, “$2a$” is Blowfish, “$2y$” is Blowfish (correct handling of 8-bit chars), “$5$” is SHA-256 and “$6$” is SHA-512,[4] other Unix may have different values, like NetBSD. Key stretching is used to increase password cracking difficulty, using by default 1000 rounds of modified MD5,[5] 64 rounds of Blowfish, 5000 rounds of SHA-256 or SHA-512.[6] The number of rounds may be varied for Blowfish, or for SHA-256 and SHA-512 by using e.g. “$6$rounds=50000$”.The format of the shadow file is simple, and basically identical to that of the password file, to wit, one line per user, ordered fields on each line, and fields separated by colons. Many systems require the order of user lines in the shadow file be identical to the order of the corresponding users in the password file.
甚至知其『必要性』勒?!
By default, most current Linux distributions do not contain the Shadow Suite installed. This includes Slackware 2.3, Slackware 3.0, and other popular distributions. One of the reasons for this is that the copyright notices in the original Shadow Suite were not clear on redistribution if a fee was charged. Linux uses a GNU Copyright (sometimes refereed to as a Copyleft) that allows people to package it into a convenient package (like a CD-ROM distribution) and charge a fee for it.
The current maintainer of the Shadow Suite, Marek Michalkiewicz <marekm@i17linuxb.ists.pwr.wroc.pl> received the source code from the original author under a BSD style copyright that allowed redistribution. Now that the copyright issues are resolved, it is expected that future distributions will contain password shadowing by default. Until then, you will need to install it yourself.
If you installed your distribution from a CD-ROM, you may find that, even though the distribution did not have the Shadow Suite installed, some of the files you need to install the Shadow Suite may be on the CD-ROM.
However, Shadow Suite versions 3.3.1, 3.3.1-2, and shadow-mk all have security problems with their login program and several other suid root programs that came with them, and should no longer be used.
All of the necessary files may be obtained via anonymous FTP or through the World Wide Web.
On a Linux system without the Shadow Suite installed, user information including passwords is stored in the /etc/passwd file. The password is stored in an encrypted format. If you ask a cryptography expert, however, he or she will tell you that the password is actually in an encoded rather than encrypted format because when using crypt(3), the text is set to null and the password is the key. Therefore, from here on, I will use the term encoded in this document.
The algorithm used to encode the password field is technically referred to as a one way hash function. This is an algorithm that is easy to compute in one direction, but very difficult to calculate in the reverse direction. More about the actual algorithm used can be found in section 2.4 or your crypt(3) manual page.
When a user picks or is assigned a password, it is encoded with a randomly generated value called the salt. This means that any particular password could be stored in 4096 different ways. The salt value is then stored with the encoded password.
When a user logs in and supplies a password, the salt is first retrieved from the stored encoded password. Then the supplied password is encoded with the salt value, and then compared with the encoded password. If there is a match, then the user is authenticated.
It is computationally difficult (but not impossible) to take a randomly encoded password and recover the original password. However, on any system with more than just a few users, at least some of the passwords will be common words (or simple variations of common words).
System crackers know all this, and will simply encrypt a dictionary of words and common passwords using all possible 4096 salt values. Then they will compare the encoded passwords in your /etc/passwd file with their database. Once they have found a match, they have the password for another account. This is referred to as a dictionary attack, and is one of the most common methods for gaining or expanding unauthorized access to a system.
If you think about it, an 8 character password encodes to 4096 * 13 character strings. So a dictionary of say 400,000 common words, names, passwords, and simple variations would easily fit on a 4GB hard drive. The attacker need only sort them, and then check for matches. Since a 4GB hard drive can be had for under ![Rendered by QuickLaTeX.com 1000.00, this is well within the means of most system crackers.</span> <span style="color: #008080;">Also, if a cracker obtains your <code>/etc/passwd</code> file first, they only need to encode the dictionary with the <code>salt</code> values actually contained in your <code>/etc/passwd</code> file. This method is usable by your average teenager with a couple of hundred spare Megabytes and a 486 class computer.</span> <span style="color: #008080;">Even without lots of drive space, utilities like crack(1) can usually break at least a couple of passwords on a system with enough users (assuming the users of the system are allowed to pick their own passwords).</span> <span style="color: #008080;">The <code>/etc/passwd</code> file also contains information like user ID's and group ID's that are used by many system programs. Therefore, the <code>/etc/passwd</code> file <em>must</em> remain world readable. If you were to change the <code>/etc/passwd</code> file so that nobody can read it, the first thing that you would notice is that the <code>ls -l</code> command now displays user ID's instead of names!</span> <span style="color: #808000;">The <em>Shadow Suite</em> solves the problem by relocating the passwords to another file (usually <code>/etc/shadow</code>). The <code>/etc/shadow</code> file is set so that it cannot be read by just anyone. Only <em>root</em> will be able to read and write to the <code>/etc/shadow</code> file. Some programs (like xlock) don't need to be able to change passwords, they only need to be able to verify them. These programs can either be run <em>suid root</em> or you can set up a group <em>shadow</em> that is allowed read only access to the <code>/etc/shadow</code> file. Then the program can be run <em>sgid shadow</em>.</span> <span style="color: #808000;">By moving the passwords to the <code>/etc/shadow</code> file, we are effectively keeping the attacker from having access to the encoded passwords with which to perform a <em>dictionary attack</em>.</span> <span style="color: #808000;">Additionally, the <em>Shadow Suite</em> adds lots of other nice features:</span> <ul> <li><span style="color: #808000;">A configuration file to set login defaults (<code>/etc/login.defs</code>)</span></li> <li><span style="color: #808000;">Utilities for adding, modifying, and deleting user accounts and groups</span></li> <li><span style="color: #808000;">Password aging and expiration</span></li> <li><span style="color: #808000;">Account expiration and locking</span></li> <li><span style="color: #808000;">Shadowed group passwords (optional)</span></li> <li><span style="color: #808000;">Double length passwords (16 character passwords) NOT RECOMMENDED]</span></li> <li><span style="color: #808000;">Better control over user's password selection</span></li> <li><span style="color: #808000;">Dial-up passwords</span></li> <li><span style="color: #808000;">Secondary authentication programs [NOT RECOMMENDED]</span></li> </ul> <span style="color: #808000;">Installing the <em>Shadow Suite</em> contributes toward a more secure system, but there are many other things that can also be done to improve the security of a Linux system, and there will eventually be a series of Linux Security HOWTO's that will discuss other security measures and related issues.</span> <span style="color: #808000;">For current information on other Linux security issues, including warnings on known vulnerabilities see the <a style="color: #808000;" href="http://bach.cis.temple.edu/linux/linux-security/">Linux Security home page.</a></span> <h2><a name="ss2.1"></a><span style="color: #339966;">2.1 Why you might NOT want to shadow your passwd file.</span></h2> <span style="color: #339966;">There are a few circumstances and configurations in which installing the <em>Shadow Suite</em> would <em>NOT</em> be a good idea:</span> <ul> <li><span style="color: #339966;">The machine does not contain user accounts.</span></li> <li><span style="color: #339966;">Your machine is running on a LAN and is using NIS (Network Information Services) to get or supply user names and passwords to other machines on the network. (This can actually be done, but is beyond the scope of this document, and really won't increase security much anyway)</span></li> <li><span style="color: #339966;">Your machine is being used by terminal servers to verify users via NFS (Network File System), NIS, or some other method.</span></li> <li><span style="color: #339966;">Your machine runs other software that validates users, and there is no shadow version available, and you don't have the source code.</span></li> </ul> <span style="color: #666699;">不過『劊客』逆向思維︰</span> <h2><a name="ss3.3"></a><span style="color: #008080;"><a style="color: #008080;" href="https://www.tldp.org/HOWTO/Shadow-Password-HOWTO-3.html">3.3 What is included with the Shadow Suite.</a></span></h2> <span style="color: #008080;">The <em>Shadow Suite</em> contains replacement programs for:</span> <span style="color: #008080;"><code>su, login, passwd, newgrp, chfn, chsh, and id</code></span> <span style="color: #008080;">The package also contains the new programs:</span> <span style="color: #008080;"><code>chage, newusers, dpasswd, gpasswd, useradd, userdel, usermod, groupadd, groupdel, groupmod, groups, pwck, grpck, lastlog, pwconv, and pwunconv</code></span> <span style="color: #008080;">Additionally, the library: <code>libshadow.a</code> is included for writing and/or compiling programs that need to access user passwords.</span> <span style="color: #008080;">Also, manual pages for the programs are also included.</span> <span style="color: #008080;">There is also a configuration file for the login program which will be installed as <code>/etc/login.defs</code>.</span> <pre class="lang:default decode:true">PWCONV(8) System Management Commands PWCONV(8) NAME pwconv, pwunconv, grpconv, grpunconv - convert to and from shadow passwords and groups SYNOPSIS pwconv [options] pwunconv [options] grpconv [options] grpunconv [options] DESCRIPTION The pwconv command creates shadow from passwd and an optionally existing shadow. The pwunconv command creates passwd from passwd and shadow and then removes shadow. The grpconv command creates gshadow from group and an optionally </pre> <span style="color: #808080;">more /etc/<span style="color: #ff9900;">passwd</span></span> <pre class="lang:default decode:true ">root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologi n nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin _apt:x:100:65534::/nonexistent:/usr/sbin/nologin systemd-network:x:101:102:systemd Network Management,,,:/run/systemd/netif:/usr/ sbin/nologin systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nol ...</pre> <span style="color: #808080;">more /etc/<span style="color: #ff9900;">shadow</span></span> <pre class="lang:default decode:true ">root:](http://www.freesandal.org/wp-content/ql-cache/quicklatex.com-f906b221839f66d11a959ea845daf3ba_l3.png) 6
6![]() W37U8bi4X4TBfCBbpl0Xg3igJmJpZaRLjkmEceZudlf6OJ/.BVglCb1Z8VUFpXT
W37U8bi4X4TBfCBbpl0Xg3igJmJpZaRLjkmEceZudlf6OJ/.BVglCb1Z8VUFpXT
.mpw6FUUyqP6qZZmx9VqMh.:17577:0:99999:7:::
daemon:*:17577:0:99999:7:::
bin:*:17577:0:99999:7:::
sys:*:17577:0:99999:7:::
sync:*:17577:0:99999:7:::
games:*:17577:0:99999:7:::
man:*:17577:0:99999:7:::
lp:*:17577:0:99999:7:::
mail:*:17577:0:99999:7:::
news:*:17577:0:99999:7:::
uucp:*:17577:0:99999:7:::
proxy:*:17577:0:99999:7:::
www-data:*:17577:0:99999:7:::
backup:*:17577:0:99999:7:::
list:*:17577:0:99999:7:::
irc:*:17577:0:99999:7:::
gnats:*:17577:0:99999:7:::
nobody:*:17577:0:99999:7:::
_apt:*:17577:0:99999:7:::
systemd-network:*:17577:0:99999:7:::
systemd-resolve:*:17577:0:99999:7:::
usbmux:*:17577:0:99999:7:::
…
挖掘『工具』的用法,企求『可能性』之術︰
root@kali:~# mkpasswd -m sha-512 toor zWfdesqLzWfdesqL
1
6
' % salt) >>> print (hashed)
zWfdesqL$W37U8bi4X4TBfCBbpl0Xg3igJmJpZaRLjkmEceZudlf6OJ/.BVglCb1Z8VUFpXT.mpw6FUUyqP6qZZmx9VqMh. >>>
不難曉,為什麼想要『那些檔案』的吧★