未曾看著一張圖
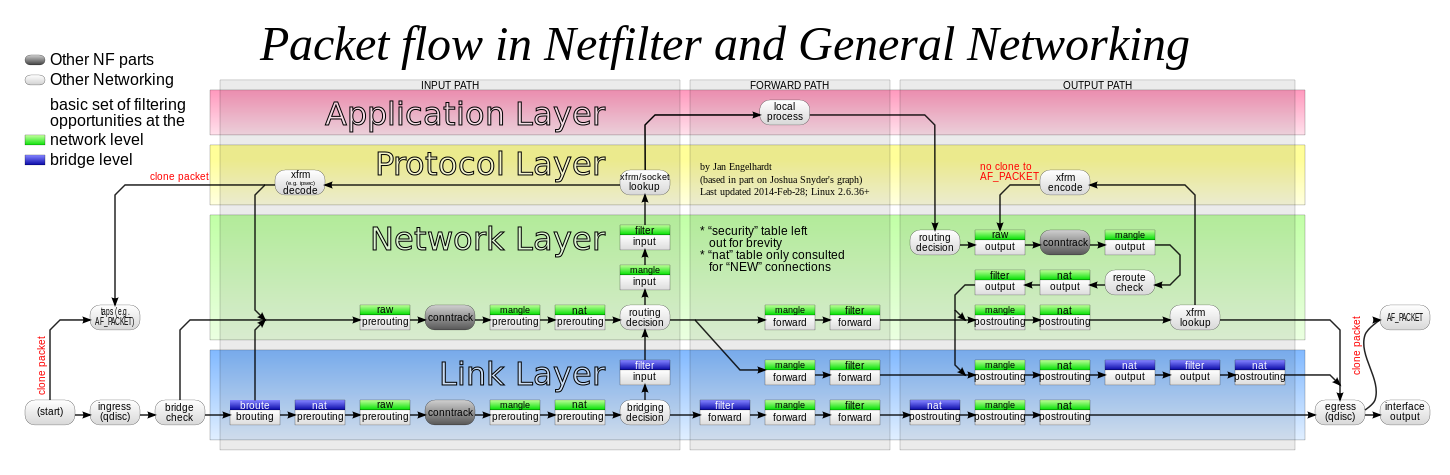
網路封包通過 Netfilter 時的工作流向
懸想多個『網卡』之 IP 封包,如何『流動』與『轉送』者,大概和
iptables
iptables是運行在使用者空間的應用軟體,通過控制Linux內核 netfilter 模組,來管理網路封包的流動與轉送。在大部份Linux系統上,可使用/usr/sbin/iptables來操作iptables,用戶手冊在手冊頁(Man page[2])中,可以透過 man iptables 指令取得。通常iptables都需要內核層級的模組來配合運作,Xtables是主要在內核層級裡面iptables API運作功能的模組。因相關動作上的需要,iptables的操作需要用到超級用戶的權限。
目前iptables在2.4、2.6及3.0版本的內核下運作,舊版的Linux內核(2.2)使用ipchains及ipwadm(Linux 2.0)達成類似的功能,2014年1月19日起發行的新版Linux內核(3.13後)則使用nftables取而代之。
操作摘要
iptables和ip6_tables、arp_tables一同都是建構在Xtables的架構下,這個方案允許系統管理員定義「表(tables)」、「鏈(chain)」、「規則(rules)」三個規則來處理封包的運送。每一個「表」都和不同的封包處理有關、決定封包是否可以通過的是「鏈」、而一條「規則」在鍵裡面則可以決定是否送往下一條鏈(或其它的動作),這個處理可以在巢狀的結構裡面重複使用。每一個網路封包從抵達到離開該電腦至少會經過一個鏈(亦即轉送或本機路由)。
首先,封包的來源決定其應該通過哪一條鏈。iptables的在過濾器(filter)中預先定義了三個鍵:INPUT(輸入)、OUTPUT(輸出 )、跟FORWARD(轉發)。預先定義的鏈也同樣會具有一個預設的”policy”(政策)像是DROP,讓封包在歷經規則到最後仍沒有符合的項目時,可以使用這個”policy”來進行操作。系統管理員可以視需要新增其它的鏈。這些鏈不提供預設的策略。如果一個封包到了這些鏈的最後仍然沒有符合的項目,就會回到前一個調用它的鏈。另外,一個鏈也可以是空白的。
每條在鏈中的規則都包含了與其相符的封包相關資料。它也會包含 “target”的資料。當一個封包穿過一個鏈,每個規則會依序檢查它。如果沒有規則與封包相符,則這個封包會被傳到下一個規則計算,如果與規則相符的話,就會開始運行規則中由target制定的動作,這個動作會決定這個封包是否在這個鏈中繼續運作。
封包穿過鏈的同時會因為:
- 有規則與封包參數相符合,因而決定這個封包的處理方式,像是 “ACCEPT”(接受)或是”DROP”(丟棄)。
- 有規則呼叫RETURN target,則會回歸到上一層呼叫的鏈中。
- 沒有規則與之相處,則會到達這個鏈的最底層。(取決於有無預設政策來決定是否採用預設政策或回歸上一層呼叫的鏈)
………
不熟也!也許該回頭讀讀
《鳥哥的 Linux 私房菜》
乎?
若問 OpenWrt 裡,這一大堆『規矩』打哪來的?!
root@LEDE:~# iptables -L Chain INPUT (policy ACCEPT) target prot opt source destination ACCEPT all -- anywhere anywhere /* !fw3 */ input_rule all -- anywhere anywhere /* !fw3: user chain for input */ ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED /* !fw3 */ syn_flood tcp -- anywhere anywhere tcp flags:FIN,SYN,RST,ACK/SYN /* !fw3 */ zone_lan_input all -- anywhere anywhere /* !fw3 */ zone_wan_input all -- anywhere anywhere /* !fw3 */ zone_wan_input all -- anywhere anywhere /* !fw3 */ Chain FORWARD (policy DROP) target prot opt source destination forwarding_rule all -- anywhere anywhere /* !fw3: user chain for forwarding */ ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED /* !fw3 */ zone_lan_forward all -- anywhere anywhere /* !fw3 */ zone_wan_forward all -- anywhere anywhere /* !fw3 */ zone_wan_forward all -- anywhere anywhere /* !fw3 */ reject all -- anywhere anywhere /* !fw3 */ Chain OUTPUT (policy ACCEPT) target prot opt source destination ACCEPT all -- anywhere anywhere /* !fw3 */ output_rule all -- anywhere anywhere /* !fw3: user chain for output */ ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED /* !fw3 */ zone_lan_output all -- anywhere anywhere /* !fw3 */ zone_wan_output all -- anywhere anywhere /* !fw3 */ zone_wan_output all -- anywhere anywhere /* !fw3 */ Chain forwarding_lan_rule (1 references) target prot opt source destination Chain forwarding_rule (1 references) target prot opt source destination Chain forwarding_wan_rule (1 references) target prot opt source destination Chain input_lan_rule (1 references) target prot opt source destination Chain input_rule (1 references) target prot opt source destination Chain input_wan_rule (1 references) target prot opt source destination Chain output_lan_rule (1 references) target prot opt source destination Chain output_rule (1 references) target prot opt source destination Chain output_wan_rule (1 references) target prot opt source destination Chain reject (5 references) target prot opt source destination REJECT tcp -- anywhere anywhere /* !fw3 */ reject-with tcp-reset REJECT all -- anywhere anywhere /* !fw3 */ reject-with icmp-port-unreachable Chain syn_flood (1 references) target prot opt source destination RETURN tcp -- anywhere anywhere tcp flags:FIN,SYN,RST,ACK/SYN limit: avg 25/sec burst 50 /* !fw3 */ DROP all -- anywhere anywhere /* !fw3 */ Chain zone_lan_dest_ACCEPT (4 references) target prot opt source destination ACCEPT all -- anywhere anywhere /* !fw3 */ Chain zone_lan_forward (1 references) target prot opt source destination forwarding_lan_rule all -- anywhere anywhere /* !fw3: user chain for forwarding */ zone_wan_dest_ACCEPT all -- anywhere anywhere /* !fw3: forwarding lan -> wan */ ACCEPT all -- anywhere anywhere ctstate DNAT /* !fw3: Accept port forwards */ zone_lan_dest_ACCEPT all -- anywhere anywhere /* !fw3 */ Chain zone_lan_input (1 references) target prot opt source destination input_lan_rule all -- anywhere anywhere /* !fw3: user chain for input */ ACCEPT all -- anywhere anywhere ctstate DNAT /* !fw3: Accept port redirections */ zone_lan_src_ACCEPT all -- anywhere anywhere /* !fw3 */ Chain zone_lan_output (1 references) target prot opt source destination output_lan_rule all -- anywhere anywhere /* !fw3: user chain for output */ zone_lan_dest_ACCEPT all -- anywhere anywhere /* !fw3 */ Chain zone_lan_src_ACCEPT (1 references) target prot opt source destination ACCEPT all -- anywhere anywhere ctstate NEW,UNTRACKED /* !fw3 */ Chain zone_wan_dest_ACCEPT (2 references) target prot opt source destination DROP all -- anywhere anywhere ctstate INVALID /* !fw3: Prevent NAT leakage */ ACCEPT all -- anywhere anywhere /* !fw3 */ DROP all -- anywhere anywhere ctstate INVALID /* !fw3: Prevent NAT leakage */ ACCEPT all -- anywhere anywhere /* !fw3 */ Chain zone_wan_dest_REJECT (1 references) target prot opt source destination reject all -- anywhere anywhere /* !fw3 */ reject all -- anywhere anywhere /* !fw3 */ Chain zone_wan_forward (2 references) target prot opt source destination forwarding_wan_rule all -- anywhere anywhere /* !fw3: user chain for forwarding */ zone_lan_dest_ACCEPT esp -- anywhere anywhere /* !fw3: Allow-IPSec-ESP */ zone_lan_dest_ACCEPT udp -- anywhere anywhere udp dpt:isakmp /* !fw3: Allow-ISAKMP */ ACCEPT all -- anywhere anywhere ctstate DNAT /* !fw3: Accept port forwards */ zone_wan_dest_REJECT all -- anywhere anywhere /* !fw3 */ Chain zone_wan_input (2 references) target prot opt source destination input_wan_rule all -- anywhere anywhere /* !fw3: user chain for input */ ACCEPT udp -- anywhere anywhere udp dpt:bootpc /* !fw3: Allow-DHCP-Renew */ ACCEPT icmp -- anywhere anywhere icmp echo-request /* !fw3: Allow-Ping */ ACCEPT igmp -- anywhere anywhere /* !fw3: Allow-IGMP */ ACCEPT tcp -- anywhere anywhere tcp dpt:ssh /* !fw3: @rule[9] */ ACCEPT udp -- anywhere anywhere udp dpt:ssh /* !fw3: @rule[9] */ ACCEPT tcp -- anywhere anywhere tcp dpt:www /* !fw3: @rule[10] */ ACCEPT udp -- anywhere anywhere udp dpt:80 /* !fw3: @rule[10] */ ACCEPT all -- anywhere anywhere ctstate DNAT /* !fw3: Accept port redirections */ zone_wan_src_REJECT all -- anywhere anywhere /* !fw3 */ Chain zone_wan_output (2 references) target prot opt source destination output_wan_rule all -- anywhere anywhere /* !fw3: user chain for output */ zone_wan_dest_ACCEPT all -- anywhere anywhere /* !fw3 */ Chain zone_wan_src_REJECT (1 references) target prot opt source destination reject all -- anywhere anywhere /* !fw3 */ reject all -- anywhere anywhere /* !fw3 */
root@LEDE:~# cat /proc/sys/net/ipv4/ip_forward 1
答之以,產生於
root@LEDE:~# cat /etc/config/firewall
config defaults
option syn_flood ‘1’
option input ‘ACCEPT’
option output ‘ACCEPT’
option forward ‘REJECT’
config zone
option name ‘lan’
option input ‘ACCEPT’
option output ‘ACCEPT’
option forward ‘ACCEPT’
option network ‘lan’
config zone
option name ‘wan’
option input ‘REJECT’
option output ‘ACCEPT’
option forward ‘REJECT’
option masq ‘1’
option mtu_fix ‘1’
option network ‘wan wan6 wwan’
config forwarding
option src ‘lan’
option dest ‘wan’
……
文本呦!?恐費疑猜哩!!
還請先認識
Firewall Configuration in OpenWrt
OpenWrt’s firewall management application fw3 has three provisioning mechanisms
-
UCI Configuration Files
-
uciutility -
LuCI
Most of the information in this section will focus on the configuration files and content. The UCI and LuCI interfaces are user abstractions ultimately modifiying the configuration files.
Firewall Managment through UCI Configuration Files
See UCI System for an overview of the UCI configuration files. The main firewall configuration file is /etc/config/firewall. This can be editted to modify the firewall settings.
![]() save the current
save the current firewall to a backup file. If your changes cause loss-of-connectivity to the router you will need to access it in failsafe mode and restore the backup to /etc/config/firewall.
Once the settings are changed (and double-checked!), use /etc/init.d/firewall restart to reload the firewall rules. This is a simple shell script calling fw3 reload. It will print diagnostics to the console as it parses the new firewall configuration. Check for errors!
![]() Any line using
Any line using # in the first character is not parsed. This is useful for comments to explain a section, or to quickly comment out a section.
The capabilities provided by netfilter are large and continually growing. The UCI firewall configuration in /etc/config/firewall covers a reasonable subset of netfilter rules but not all of them. In order to support more functionality an includessection was added to the UCI firewall configuration to load a file containing native iptable directives. It is processed as a shell script so really any shell command can be added to it but the focus is working with the netfilter subsystem by adding iptables commands. See fw3 Configuration Examples for usage.
![]() The iptables commands can be cryptic and cause unexpected results. Whenever possible, use the fw3 firewall UCI config. There are some scenarios where
The iptables commands can be cryptic and cause unexpected results. Whenever possible, use the fw3 firewall UCI config. There are some scenarios where iptable commands are required. See Netfilter in OpenWrt for more information.
Configuration File Sections
Below is an overview of the section types that may be defined in the firewall configuration. A minimal firewall configuration for a router usually consists of one defaults section, at least two zones (lan and wan) and one forwarding to allow traffic from lan to wan. (The forwarding section is not strictly required when there are no more than two zones as the rule can then be set as the ‘global default’ for that zone.)
Defaults
The defaults section declares global firewall settings which do not belong to specific zones. The following options are defined within this section:
| Name | Type | Required | Default | Description |
|---|---|---|---|---|
input |
string | no | REJECT |
Set policy for the INPUT chain of the filter table. |
forward |
string | no | REJECT |
Set policy for the FORWARD chain of the filter table. |
output |
string | no | REJECT |
Set policy for the OUTPUT chain of the filter table. |
drop_invalid |
boolean | no | 0 |
Drop invalid packets (e.g. not matching any active connection). |
syn_flood |
boolean | no | 0 |
Enable SYN flood protection (obsoleted by synflood_protect setting). |
synflood_protect |
boolean | no | 0 |
Enable SYN flood protection. |
synflood_rate |
string | no | 25 |
Set rate limit (packets/second) for SYN packets above which the traffic is considered a flood. |
synflood_burst |
string | no | 50 |
Set burst limit for SYN packets above which the traffic is considered a flood if it exceeds the allowed rate. |
tcp_syncookies |
boolean | no | 1 |
Enable the use of SYN cookies. |
tcp_ecn |
boolean | no | 0 |
 |
tcp_window_scaling |
boolean | no | 1 |
Enable TCP window scaling. |
accept_redirects |
boolean | no | 0 |
 |
accept_source_route |
boolean | no | 0 |
 |
custom_chains |
boolean | no | 1 |
 |
disable_ipv6 |
boolean | no | 0 |
Disable IPv6 firewall rules. |
flow_offloading |
boolean | no | 0 |
Enable software flow offloading for connections. (decrease cpu load / increase routing throughput) |
flow_offloading_hw |
boolean | no | 0 |
Enable hardware flow offloading for connections. (depends on flow_offloading and hw capability) |
tcp_reject_code |
reject_code | no |  |
 |
any_reject_code |
reject_code | no |  |
 |
auto-helper |
bool | no |  |
 |
Zones
A zone section groups one or more interfaces and serves as a source or destination for forwardings, rules and redirects. Masquerading (NAT) of outgoing traffic is controlled on a per-zone basis. Note that masquerading is defined on the outgoinginterface.
-
INPUT rules for a zone describe what happens to traffic trying to reach the router itself through an interface in that zone.
-
OUTPUT rules for a zone describe what happens to traffic originating from the router itself going through an interface in that zone.
-
FORWARD rules for a zone describe what happens to traffic passing between different interfaces in that zone.
………
了解 fw3 之『武功』勒☆
Firewall Overview
OpenWrt uses the firewall3 (fw3) netfilter/iptable rule builder application. It runs in user-space to parse a configuration file into a set of iptables rules, sending each to the kernel netfilter modules.
fw3 Purpose
The netfilter rule set can be very complex for a typical router. This is by necessity; each rule is tailored to a discrete capability provided by the router to protect its supported networks, provide NAT to conserve scarce IPv4 addresses, even mangle the packets during routing. A typical router has over 100 rules designed to support packet routing.
The fw3 application is used by OpenWRT to “safely” construct a rule set while hiding much of the details.
On inspecting the netfilter rule set using fw3 print, you will see a number of netfilter/iptables rules either not explicitly defined in the fw3 configuration files, or more difficult to understand (thank goodness for the –comment match!) The netfilter rules include:
-
A number of chains (mis-termed
_rule) for each special target and zone -
INPUT and OUTPUT for the often forgotten loopback interface
-
The
option syn_flood 1oroption mtu_fix 1each translate to complex iptable rules -
The
option masq 1translates to the ‘-j MASQUERADE’ target for NAT -
manglerules that match bits in the packets TCP header and then modify the packet
The fw3 configuration is fairly straight forward and automatically provides the router with a base rule set of rules and an understandable configuration file for additional rules.
The rules consumed by netfilter are, at best, difficult to comprehend due to the exacting nature of netfilter. However, every rule provides desired capability or blocks malicious capability, and therefore necessary.
………
root@LEDE:~# fw3 -h
fw3 [-4] [-6] [-q] print
fw3 [-q] {start|stop|flush|reload|restart}
fw3 [-q] network {net}
fw3 [-q] device {dev}
fw3 [-q] zone {zone} [dev]
root@LEDE:~# fw3 -4 print Warning: Unable to locate ipset utility, disabling ipset support Warning: Section @zone[1] (wan) cannot resolve device of network 'wan6' Warning: Section @rule[9] does not specify a protocol, assuming TCP+UDP Warning: Section @rule[10] does not specify a protocol, assuming TCP+UDP iptables -t filter -P INPUT ACCEPT iptables -t filter -P OUTPUT ACCEPT iptables -t filter -P FORWARD DROP iptables -t filter -N reject iptables -t filter -N input_rule iptables -t filter -N output_rule iptables -t filter -N forwarding_rule iptables -t filter -N syn_flood iptables -t filter -N zone_lan_input iptables -t filter -N zone_lan_output iptables -t filter -N zone_lan_forward iptables -t filter -N zone_lan_src_ACCEPT iptables -t filter -N zone_lan_dest_ACCEPT iptables -t filter -N input_lan_rule iptables -t filter -N output_lan_rule iptables -t filter -N forwarding_lan_rule iptables -t filter -A zone_lan_input -m comment --comment "!fw3: user chain for input" -j input_lan_rule iptables -t filter -A zone_lan_output -m comment --comment "!fw3: user chain for output" -j output_lan_rule iptables -t filter -A zone_lan_forward -m comment --comment "!fw3: user chain for forwarding" -j forwarding_lan_rule iptables -t filter -N zone_wan_input iptables -t filter -N zone_wan_output iptables -t filter -N zone_wan_forward iptables -t filter -N zone_wan_src_REJECT iptables -t filter -N zone_wan_dest_ACCEPT iptables -t filter -N zone_wan_dest_REJECT iptables -t filter -N input_wan_rule iptables -t filter -N output_wan_rule iptables -t filter -N forwarding_wan_rule iptables -t filter -A zone_wan_input -m comment --comment "!fw3: user chain for input" -j input_wan_rule iptables -t filter -A zone_wan_output -m comment --comment "!fw3: user chain for output" -j output_wan_rule iptables -t filter -A zone_wan_forward -m comment --comment "!fw3: user chain for forwarding" -j forwarding_wan_rule iptables -t filter -A INPUT -i lo -m comment --comment "!fw3" -j ACCEPT iptables -t filter -A OUTPUT -o lo -m comment --comment "!fw3" -j ACCEPT iptables -t filter -A INPUT -m comment --comment "!fw3: user chain for input" -j input_rule iptables -t filter -A OUTPUT -m comment --comment "!fw3: user chain for output" -j output_rule iptables -t filter -A FORWARD -m comment --comment "!fw3: user chain for forwarding" -j forwarding_rule iptables -t filter -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT iptables -t filter -A OUTPUT -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT iptables -t filter -A FORWARD -m conntrack --ctstate RELATED,ESTABLISHED -m comment --comment "!fw3" -j ACCEPT iptables -t filter -A syn_flood -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m limit --limit 25/sec --limit-burst 50 -m comment --comment "!fw3" -j RETURN iptables -t filter -A syn_flood -m comment --comment "!fw3" -j DROP iptables -t filter -A INPUT -p tcp -m tcp --tcp-flags FIN,SYN,RST,ACK SYN -m comment --comment "!fw3" -j syn_flood iptables -t filter -A reject -p tcp -m comment --comment "!fw3" -j REJECT --reject-with tcp-reset iptables -t filter -A reject -m comment --comment "!fw3" -j REJECT --reject-with icmp-port-unreachable iptables -t filter -A zone_wan_input -p udp -m udp --dport 68 -m comment --comment "!fw3: Allow-DHCP-Renew" -j ACCEPT iptables -t filter -A zone_wan_input -p icmp -m icmp --icmp-type 8 -m comment --comment "!fw3: Allow-Ping" -j ACCEPT iptables -t filter -A zone_wan_input -p 2 -m comment --comment "!fw3: Allow-IGMP" -j ACCEPT iptables -t filter -A zone_wan_forward -p esp -m comment --comment "!fw3: Allow-IPSec-ESP" -j zone_lan_dest_ACCEPT iptables -t filter -A zone_wan_forward -p udp -m udp --dport 500 -m comment --comment "!fw3: Allow-ISAKMP" -j zone_lan_dest_ACCEPT iptables -t filter -A zone_wan_input -p tcp -m tcp --dport 22 -m comment --comment "!fw3: @rule[9]" -j ACCEPT iptables -t filter -A zone_wan_input -p udp -m udp --dport 22 -m comment --comment "!fw3: @rule[9]" -j ACCEPT iptables -t filter -A zone_wan_input -p tcp -m tcp --dport 80 -m comment --comment "!fw3: @rule[10]" -j ACCEPT iptables -t filter -A zone_wan_input -p udp -m udp --dport 80 -m comment --comment "!fw3: @rule[10]" -j ACCEPT iptables -t filter -A zone_lan_forward -m comment --comment "!fw3: forwarding lan -> wan" -j zone_wan_dest_ACCEPT iptables -t filter -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT iptables -t filter -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT iptables -t filter -A zone_lan_input -m comment --comment "!fw3" -j zone_lan_src_ACCEPT iptables -t filter -A zone_lan_forward -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT iptables -t filter -A zone_lan_output -m comment --comment "!fw3" -j zone_lan_dest_ACCEPT iptables -t filter -D zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT iptables -t filter -A zone_lan_src_ACCEPT -i br-lan -m conntrack --ctstate NEW,UNTRACKED -m comment --comment "!fw3" -j ACCEPT iptables -t filter -D zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT iptables -t filter -A zone_lan_dest_ACCEPT -o br-lan -m comment --comment "!fw3" -j ACCEPT iptables -t filter -D INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input iptables -t filter -A INPUT -i br-lan -m comment --comment "!fw3" -j zone_lan_input iptables -t filter -D OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output iptables -t filter -A OUTPUT -o br-lan -m comment --comment "!fw3" -j zone_lan_output iptables -t filter -D FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward iptables -t filter -A FORWARD -i br-lan -m comment --comment "!fw3" -j zone_lan_forward iptables -t filter -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT iptables -t filter -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT iptables -t filter -A zone_wan_input -m comment --comment "!fw3" -j zone_wan_src_REJECT iptables -t filter -A zone_wan_forward -m comment --comment "!fw3" -j zone_wan_dest_REJECT iptables -t filter -A zone_wan_output -m comment --comment "!fw3" -j zone_wan_dest_ACCEPT iptables -t filter -D zone_wan_dest_ACCEPT -o br-wan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP iptables -t filter -A zone_wan_dest_ACCEPT -o br-wan -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP iptables -t filter -D zone_wan_dest_ACCEPT -o br-wan -m comment --comment "!fw3" -j ACCEPT iptables -t filter -A zone_wan_dest_ACCEPT -o br-wan -m comment --comment "!fw3" -j ACCEPT iptables -t filter -D zone_wan_src_REJECT -i br-wan -m comment --comment "!fw3" -j reject iptables -t filter -A zone_wan_src_REJECT -i br-wan -m comment --comment "!fw3" -j reject iptables -t filter -D zone_wan_dest_REJECT -o br-wan -m comment --comment "!fw3" -j reject iptables -t filter -A zone_wan_dest_REJECT -o br-wan -m comment --comment "!fw3" -j reject iptables -t filter -D INPUT -i br-wan -m comment --comment "!fw3" -j zone_wan_input iptables -t filter -A INPUT -i br-wan -m comment --comment "!fw3" -j zone_wan_input iptables -t filter -D OUTPUT -o br-wan -m comment --comment "!fw3" -j zone_wan_output iptables -t filter -A OUTPUT -o br-wan -m comment --comment "!fw3" -j zone_wan_output iptables -t filter -D FORWARD -i br-wan -m comment --comment "!fw3" -j zone_wan_forward iptables -t filter -A FORWARD -i br-wan -m comment --comment "!fw3" -j zone_wan_forward iptables -t filter -D zone_wan_dest_ACCEPT -o wlan1 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP iptables -t filter -A zone_wan_dest_ACCEPT -o wlan1 -m conntrack --ctstate INVALID -m comment --comment "!fw3: Prevent NAT leakage" -j DROP iptables -t filter -D zone_wan_dest_ACCEPT -o wlan1 -m comment --comment "!fw3" -j ACCEPT iptables -t filter -A zone_wan_dest_ACCEPT -o wlan1 -m comment --comment "!fw3" -j ACCEPT iptables -t filter -D zone_wan_src_REJECT -i wlan1 -m comment --comment "!fw3" -j reject iptables -t filter -A zone_wan_src_REJECT -i wlan1 -m comment --comment "!fw3" -j reject iptables -t filter -D zone_wan_dest_REJECT -o wlan1 -m comment --comment "!fw3" -j reject iptables -t filter -A zone_wan_dest_REJECT -o wlan1 -m comment --comment "!fw3" -j reject iptables -t filter -D INPUT -i wlan1 -m comment --comment "!fw3" -j zone_wan_input iptables -t filter -A INPUT -i wlan1 -m comment --comment "!fw3" -j zone_wan_input iptables -t filter -D OUTPUT -o wlan1 -m comment --comment "!fw3" -j zone_wan_output iptables -t filter -A OUTPUT -o wlan1 -m comment --comment "!fw3" -j zone_wan_output iptables -t filter -D FORWARD -i wlan1 -m comment --comment "!fw3" -j zone_wan_forward iptables -t filter -A FORWARD -i wlan1 -m comment --comment "!fw3" -j zone_wan_forward iptables -t filter -A FORWARD -m comment --comment "!fw3" -j reject iptables -t nat -N prerouting_rule iptables -t nat -N postrouting_rule iptables -t nat -N zone_lan_postrouting iptables -t nat -N zone_lan_prerouting iptables -t nat -N prerouting_lan_rule iptables -t nat -N postrouting_lan_rule iptables -t nat -A zone_lan_prerouting -m comment --comment "!fw3: user chain for prerouting" -j prerouting_lan_rule iptables -t nat -A zone_lan_postrouting -m comment --comment "!fw3: user chain for postrouting" -j postrouting_lan_rule iptables -t nat -N zone_wan_postrouting iptables -t nat -N zone_wan_prerouting iptables -t nat -N prerouting_wan_rule iptables -t nat -N postrouting_wan_rule iptables -t nat -A zone_wan_prerouting -m comment --comment "!fw3: user chain for prerouting" -j prerouting_wan_rule iptables -t nat -A zone_wan_postrouting -m comment --comment "!fw3: user chain for postrouting" -j postrouting_wan_rule iptables -t nat -A PREROUTING -m comment --comment "!fw3: user chain for prerouting" -j prerouting_rule iptables -t nat -A POSTROUTING -m comment --comment "!fw3: user chain for postrouting" -j postrouting_rule iptables -t nat -D PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting iptables -t nat -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting iptables -t nat -D POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting iptables -t nat -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting iptables -t nat -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE iptables -t nat -D PREROUTING -i br-wan -m comment --comment "!fw3" -j zone_wan_prerouting iptables -t nat -A PREROUTING -i br-wan -m comment --comment "!fw3" -j zone_wan_prerouting iptables -t nat -D POSTROUTING -o br-wan -m comment --comment "!fw3" -j zone_wan_postrouting iptables -t nat -A POSTROUTING -o br-wan -m comment --comment "!fw3" -j zone_wan_postrouting iptables -t nat -D PREROUTING -i wlan1 -m comment --comment "!fw3" -j zone_wan_prerouting iptables -t nat -A PREROUTING -i wlan1 -m comment --comment "!fw3" -j zone_wan_prerouting iptables -t nat -D POSTROUTING -o wlan1 -m comment --comment "!fw3" -j zone_wan_postrouting iptables -t nat -A POSTROUTING -o wlan1 -m comment --comment "!fw3" -j zone_wan_postrouting iptables -t mangle -D FORWARD -p tcp -o br-wan -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: wan (mtu_fix)" -j TCPMSS --clamp-mss-to-pmtu iptables -t mangle -A FORWARD -p tcp -o br-wan -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: wan (mtu_fix)" -j TCPMSS --clamp-mss-to-pmtu iptables -t mangle -D FORWARD -p tcp -o wlan1 -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: wan (mtu_fix)" -j TCPMSS --clamp-mss-to-pmtu iptables -t mangle -A FORWARD -p tcp -o wlan1 -m tcp --tcp-flags SYN,RST SYN -m comment --comment "!fw3: wan (mtu_fix)" -j TCPMSS --clamp-mss-to-pmtu