萬聖夜剛過,怎了想起了
斯巴達
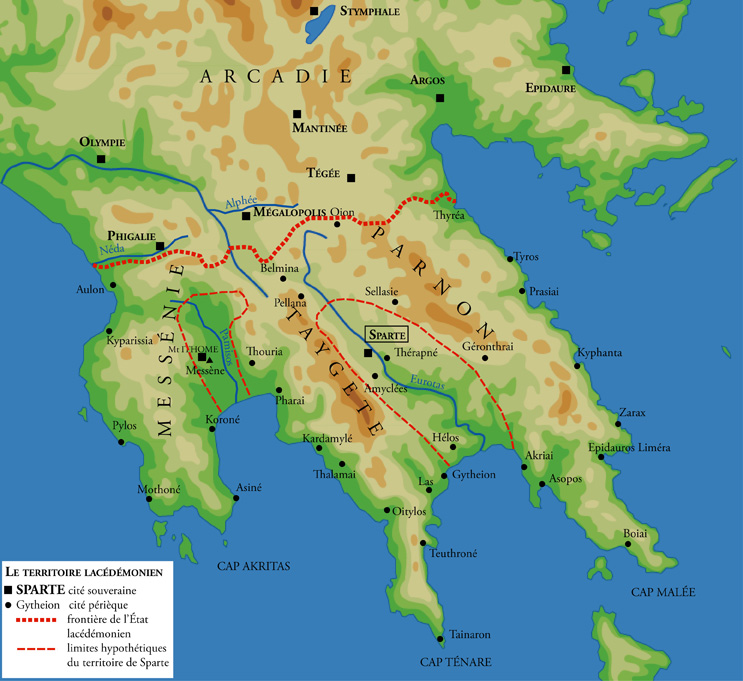
古斯巴達疆域
斯巴達(希臘語:Σπάρτη),又稱拉刻代蒙(Λακεδαίμων, Lakedaímōn)是古代希臘城邦之一,斯巴達城位於中拉哥尼亞平原的南部,埃夫羅塔斯河的西岸。斯巴達城是個戰略要衝,三面環山 ,扼守著塔伊耶托斯山脈,塔伊耶托斯山脈上的隘口是進入拉科尼亞和南部伯羅奔尼撒半島的必經之路,斯巴達城並不靠海,離她的海港吉雄有27英里的距離。
斯巴達以其名。斯巴達是寡頭政治,和當時雅典的民主制度形成鮮明對比。斯巴達規定所有男人必須從軍。斯巴達擁有眾多國的奴隸 ,稱為黑勞士,因此「斯巴達式」也成為艱苦地進行的代名詞。在伯羅奔尼撒戰爭中,斯巴達及其同盟者戰勝雅典軍隊並霸權整個希臘。但斯巴達在稱霸希臘不久後便被新興的底比斯打敗,在北方的馬其頓崛起後,斯巴達失去了在希臘的影響力。
?或因『劊客』多半不睡覺的吧!
今天既是『諸聖之日』,且講點『整合工具』好了︰
SPARTA
Network Infrastructure Penetration Testing Tool
………
Authors:
SECFORCE
Antonio Quina (@st3r30byt3)
Leonidas Stavliotis (@lstavliotis)
Known issues
SPARTA uses a third-party tool called Cutycapt to take screenshots. One of the problems with the version that is currently in Kali’s repositories is that it fails to take screenshots of HTTPS pages when self-signed certificates are in use. A way around this is to compile the Cutycapt executable yourself and edit SPARTA’s configuration file to specify the path to the compiled executable.
It can be compiled in Kali by following these instructions:
% sudo apt-get install subversion libqt4-webkit libqt4-dev g++ % svn co svn://svn.code.sf.net/p/cutycapt/code/ cutycapt % cd cutycapt/CutyCapt % qmake % make % ./CutyCapt --url=http://www.example.org --out=example.png
Credits
Credits where credits are due. The nmap XML output parsing engine was largely based on code by yunshu, modified by ketchup and modified by us. SPARTA relies heavily on nmap, hydra, cutycapt, python, PyQt, Elixir and many other tools and technologies so we would like to thank all of the people involved in the creation of those. Credits to Bernardo Damele A.G. for the ms08-067_check script used by smbenum.sh. Credit to Diana Guardão (https://www.behance.net/didoquinhasfaaa) for the logo design. Thanks as well to our incredible team at SECFORCE for the countless bug reports and feedback. Last but not least, thank you for using SPARTA. Let us know how we can improve it! Happy hacking!
………
DOCUMENTATION
This documentation will grow organically and is a work in progress.
Configuration
At the moment, SPARTA can be configured by editing the sparta.conf file located in SPARTA’s root folder. At launch time, SPARTA checks if this file exists and if it does not, a new file is created with default values. In the future, there will be a settings menu which will remove the need to manually edit this file and will make changing the configuration easier and safer.
WARNING: Apart from tools, do not remove any lines from sparta.conf as it could break functionality. Also, assume that setting values are case-sensitive.
Adding new actions
In SPARTA we separate actions in three classes:
- Host Actions: are invoked by right-clicking on a host and their tool output will be stored and displayed in SPARTA
- Port Actions: are invoked by right-clicking on a port or service and their tool output will be stored and displayed in SPARTA (Eg: Nikto)
- Terminal Actions: are invoked by right-clicking on a port and will spawn an external terminal window (Eg: Connect with netcat)
………
大概不必多言,就可知其『目的』乎?!
more /etc/sparta.conf
[GeneralSettings] default-terminal=gnome-terminal tool-output-black-background=False screenshooter-timeout=15000 web-services="http,https,ssl,soap,http-proxy,http-alt,https-alt" enable-scheduler=True enable-scheduler-on-import=False max-fast-processes=10 max-slow-processes=10 [BruteSettings] store-cleartext-passwords-on-exit=True username-wordlist-path=/usr/share/wordlists/ password-wordlist-path=/usr/share/wordlists/ default-username=root default-password=password services="asterisk,afp,cisco,cisco-enable,cvs,firebird,ftp,ftps,http-head,http-g et,https-head,https-get,http-get-form,http-post-form,https-get-form,https-post-f orm,http-proxy,http-proxy-urlenum,icq,imap,imaps,irc,ldap2,ldap2s,ldap3,ldap3s,l dap3-crammd5,ldap3-crammd5s,ldap3-digestmd5,ldap3-digestmd5s,mssql,mysql,ncp,nnt p,oracle-listener,oracle-sid,pcanywhere,pcnfs,pop3,pop3s,postgres,rdp,rexec,rlog in,rsh,s7-300,sip,smb,smtp,smtps,smtp-enum,snmp,socks5,ssh,sshkey,svn,teamspeak, telnet,telnets,vmauthd,vnc,xmpp" ...
何不盡己所學,藉此攻向自家 OpenWrt 『路由器』也!?
_2.png)
看看費幾多時,成也不成,蓋『評估』那個『密碼』安不安全哩☺
[quark@localhost ~]$ ssh -l root 5.168.168.20
root@5.168.168.20's password:
BusyBox v1.25.1 () built-in shell (ash)
_________
/ /\ _ ___ ___ ___
/ LE / \ | | | __| \| __|
/ DE / \ | |__| _|| |) | _|
/________/ LE \ |____|___|___/|___| lede-project.org
\ \ DE /
\ LE \ / -----------------------------------------------------------
\ DE \ / Reboot (17.01.6, r3979-2252731af4)
\________\/ -----------------------------------------------------------
root@LEDE:~#
彷彿傳說『八卦爐』裡,方能練得這樣『火眼精睛』呦︰
日後讀文能聽『弦外之音』☆
Secure your router’s access
There are some possibilities to grant access to the router (or to any PC/Server):
-
ask for nothing: anybody who can establish a connection gets access
-
ask for username and password on an unsecured connection (e.g. telnet)
-
ask for username and password on an encrypted connection (e.g. SSH) (e.g. by following walkthrough_login)
-
ask for username and merely a
signatureinstead of apassword(e.g. SSH with signature.authentication)
If you ask for username/password, an attacker has to guess the combination. If you use an unencrypted connection, he could eavesdrop on you and obtain them.
If you use an encrypted connection, any eavesdropper would have to decrypt the packets first. This is always possible. How long it takes to decrypt the content, depends on the algorithm and key length you used.
Also, as long as an attacker has network access to the console, he can always run a brute-force attack to find out username and password. He does not have to do that himself: he can let his computer(s) do the guessing. To render this option improbable or even impossible you can:
-
not offer access from the Internet at all, or restrict it to certain IP addresses or IP address ranges
-
by blocking incoming connections to those ports (TCP 22, 80 and 443 by default) in your firewall
-
make it more difficult to guess:
-
don’t use the username
root -
don’t use a weak password with 8 or less characters
-
don’t let the SSH server dropbear listen on the default port (22)
-
-
use the combination of
-
username different than
root -
public key authentication. Your public keys can be specified in Administation → System → SSH-keys. The guide to DropBear SSH public key authentication has detailed information on generating SSH keypairs which include the public key(s) you should upload to your configuration.
-
觀法能有『清涼之見』☆
/dropBrute
Lightweight fail2ban alternative for OpenWRT – inspects ssh log for brute force attacks and blocks via iptables – w/ whitelist and blacklist support
dropBrute
dropBrute has been superceeded by bearDropper
—
Lightweight fail2ban alternative for OpenWRT
Runs via cron; inspects ssh log for brute force attacks and blocks via iptables. Includes whitelist and blacklist support.
Initial version posted 10/31/2011 at https://forum.openwrt.org/viewtopic.php?pid=224122
自由自在,豈不快活耶◎◎

