正義女神
正義女神 (Justitia,古羅馬代表公平正義的女神)是作為法律基礎的公正道德的象徵。文藝復興以來Justitia(正義女神)通常被描述為一名裸露胸膛的婦女,手持天秤及長劍,並有時戴有眼罩。現今經常出現於法院的其肖像是由代表正義的古希臘法律女神忒彌斯(Themis)及古羅馬命運女神福爾圖娜(Fortuna)的形象混合而成。自十五世紀開始,正義女神經常被造成帶眼罩之形象,代表其客觀、不徇私、一視同仁的平等精神。

Justitia blindfolded and holding balance scales and a sword. Court of Final Appeal, Hong Kong
正義女神 Lady Justice 手持『公正天平』,拿著『正義長劍』,但為什麼帶著『眼罩』呢?因為正義是無偏無私之舉,據說眼通心,所以不見『可欲』,象徵無所住而生其心也!
如問鈔票該具名嗎?為了『資安』應反對『匿名通訊』耶??
洋蔥路由
洋蔥路由(英語:Onion routing)為一種在電腦網路上匿名溝通的技術。在洋蔥路由的網路中,訊息一層一層的加密包裝成像洋蔥一樣的封包,並經由一系列被稱作洋蔥路由器的網路節點傳送,每經過一個洋蔥路由器會將封包的最外層解密,直至目的地時將最後一層解密,目的地因而能獲得原始訊息。而因為透過這一系列的加密包裝,每一個網路節點(包含目的地)都只能知道上一個節點的位置,但無法知道整個傳送路徑以及原傳送者的位址。[1]
發明與實作
1990年代中期,美國海軍研究實驗室的研究員保羅‧塞維亞森(Paul Syverson)、麥可‧里德和大衛‧戈爾德施拉格(David Goldschlag)為了保護美國線上情報系統而開發了洋蔥路由[2][3][4]。其後國防高等研究計劃署接手該計畫繼續開發,並在1998年獲得海軍的專利[3][5][6]。2002年電腦科學家羅傑‧丁高戴恩(Roger Dingledine)和尼克‧馬修森(Nick Mathewson)加入了塞維亞森的計畫,並開始開發Tor;Tor為「洋蔥路由專案」(The Onion Routing project)的頭字語,該專案後來成為規模最大的洋蔥路由實作並廣為人知。之後美國海軍研究實驗室將Tor以自由軟體授權的方式公開了原始碼[4][7][8],丁高戴恩、馬修森以及其他五位成員在2006年成立了名為「The Tor Project」的非營利組織,並獲得包含電子前哨基金會在內的幾個組織的財政資助。[9][10]
弱點
計時分析
傳統網際網路不被認為具有匿名性的一個理由為網際網路服務供應商具有紀錄和追蹤各電腦間的連線能力;例如當有人存取一個特定網站時,往來的資訊內容如密碼等,雖然能透過像是HTTPS等加密連線方式保護讓其他人無法得知內容,但是連線本身卻仍會有紀錄 ,包含何時建立連線,多少資料量被傳送等。洋蔥路由雖然能建立並隱藏兩電腦之間的連線,使兩者之間並無一個可分辨的直接連線 ,但仍會有上述的連線紀錄問題。流量分析可藉由搜尋連線紀錄的連線時間和資料傳輸量來試圖判別潛在的一對發送者與接收者;例如當有人傳送51KB的資料到一個未知的電腦,三秒後另一未知的電腦傳送51KB的資料給一個特定的網站,則可以推斷此人可能與該網站曾建立連線[12][13]。此外還有一些原因可以讓流量分析更加有效 ,包含節點的損壞或離開網路[13],以及當鏈已經因為定期重建而改變,但有些鏈上節點卻仍在追蹤此前建立的會話等。[14]
大蒜路由是洋蔥路由的一種變體,其結合了I2P網路並將多份訊息加密打包在一起,使其更難被攻擊者以流量分析的方式破解。[15]
出口節點漏洞
雖然訊息在洋蔥路由網路中被層層加密,但是在出口節點時,該節點會把最後一層解密並將原始訊息傳給接收者;因此若出口節點遭到攻擊或是受控制,則原始的訊息將會被截取[16]。瑞典研究員丹‧伊格史塔德(瑞典語:Dan Egersta)曾用此方式獲得了超過100封寄給外國大使館的電子郵件密碼[17]。出口節點漏洞的原理與未加密無線網路很類似,後者為使用者將未加密的資料在無線網路上傳送時可能中途被其他人截走;這兩種問題都可以透過端對端加密連線如SSL、HTTPS等方式解決。[18]
大蒜路由
大蒜路由(Garlic routing)是洋蔥路由的一個變體,它將傳輸的原始數據拆散為加密數據包通過多條隧道交叉疏散傳遞,令攻擊者的流量分析難上加難。在洋蔥路由中一條或多條數據流的上傳與下載共用一條隧道,而這種路由方式的上傳與下載隧道相互獨立而且兩個方向上的隧道數量都可能>1,所以被稱為大蒜路由。
與洋蔥路由的電路交換(Circuit Switching)相比,大蒜路由也稱為封包交換(Packet Switching)方式。大蒜路由是I2P與Tor及其他隱私/加密網絡的主要區別之一。
彩色的世界,說明不只有『黑白』!詮釋現象,人性之矛盾欲望,總有不同程度的『灰』!!難道『不偏不倚』、『不左不右』、『不□不非□』,就謂之『中』乎??!!在那『開天闢地』之初 ,既無『時間』又無『空間』,哪來『上下左右』,一切無不在其中乎!!??
謙謙君子,慎思慎行而已矣☆
─── 《樹莓派 0W 狂想曲︰資安探測器《𝄡》》
理能侑於『工具』應用之辯乎?
人拿刀殺人,罪在刀乎?有製殺人之刀者,有人用以殺人,製刀者果無罪耶 ??工具論者 ── 器物與應用無干 ── 有辯也。依其論 ,隻手亦可殺人,練武動機可疑矣!那麼
《荀子‧王制篇》
馬駭輿,則君子不安輿;庶人駭政,則君子不安位。馬駭輿,則莫若靜之;庶人駭政,則莫若惠之。選賢良,舉篤敬,興孝弟,收孤寡,補貧窮。如是,則庶人安政矣。庶人安政,然後君子安位。傳曰:「君者、舟也,庶人者、水也;水則載舟,水則覆舟。」此之謂也。
言︰水則載舟,水則覆舟。到底是誰之過焉!!
─── 摘自《【鼎革‧革鼎】︰ RASPBIAN STRETCH 《三‧戊》》
設想『暗網』已『寄生』哩!
Dark web
The dark web is the World Wide Web content that exists on darknets, overlay networks that use the Internet but require specific software, configurations, or authorization to access.[1][2] The dark web forms a small part of the deep web, the part of the Web not indexedby web search engines, although sometimes the term deep web is mistakenly used to refer specifically to the dark web.[3][4][5][6][7]
The darknets which constitute the dark web include small, friend-to-friend peer-to-peer networks, as well as large, popular networks like Tor, Freenet, I2P, and Riffle operated by public organizations and individuals. Users of the dark web refer to the regular web as Clearnet due to its unencrypted nature.[8] The Tor dark web may be referred to as onionland,[9] a reference to the network’s top-level domain suffix .onion and the traffic anonymization technique of onion routing.
與其考慮封殺『網際網路』??實不如思考如何建立『資安網』呦 !!比方藉著
n2n
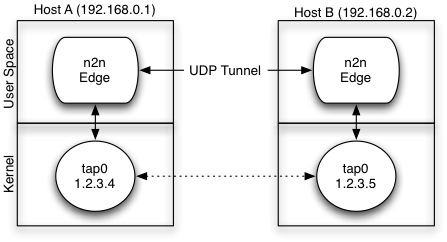
n2n is an open source Layer 2 over Layer 3 VPN application which utilises a peer-to-peer architecture for network membership and routing.
Unlike many other VPN programs, n2n can also connect computers which reside behind NAT routers. These connections are set up with help from a third computer that both computers can reach. This computer, called a supernode, can then route the information between NATed nodes.[2][3]
It is free software licensed under the terms of the GNU General Public License v3.[citation needed]
Turbo VPN is a custom Windows server/client implementation of n2n.[citation needed]
之『免費』、『簡易』及『加密』種種優點,或『亞馬遜』用戶也喜歡哩☺
![]()
Using n2n with Amazon (AWS) EC2
Although we currently have no time to further develop n2n (we have put the project on hold until we have time to work at it again), this tool is still widely used. This article (courtesy of Stuart Buckell) shows how to use n2n to enable broadcast and multicast support on Amazon (AWS) EC2, which is required for certain enterprise applications and protocols.
Enjoy!
所以特別推薦啊☆
n2n
a Layer Two Peer-to-Peer VPN
n2n is a layer-two peer-to-peer virtual private network (VPN) which allows users to exploit features typical of P2P applications at network instead of application level. This means that users can gain native IP visibility (e.g. two PCs belonging to the same n2n network can ping each other) and be reachable with the same network IP address regardless of the network where they currently belong. In a nutshell, as OpenVPN moved SSL from application (e.g. used to implement the https protocol) to network protocol, n2n moves P2P from application to network level.
The main n2n design features are:
- An n2n is an encrypted layer two private network based on a P2P protocol.
- Encryption is performed on edge nodes using open protocols with user-defined encryption keys: you control your security without delegating it to companies as it happens with Skype or Hamachi.
- Each n2n user can simultaneously belong to multiple networks (a.k.a. communities).
- Ability to cross NAT and firewalls in the reverse traffic direction (i.e. from outside to inside) so that n2n nodes are reachable even if running on a private network. Firewalls no longer are an obstacle to direct communications at IP level.
- n2n networks are not meant to be self-contained: it is possible to route traffic across n2n and non-n2n networks.
The n2n architecture is based on two components:
- edge nodes: applications installed on user PCs that allow the n2n network to be build. Practically each edge node creates a tun/tap device that is then the entry point to the n2n network.
- an supernode: it is used by edge nodes at startup or for reaching nodes behind symmetrical firewalls. This application is basically a directory register and a packet router for those nodes that cannot talk directly.
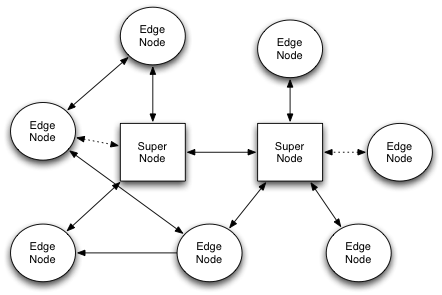
Edge nodes talk by means of virtual tap interfaces. Each tap interface is an n2n edge node. Each PC can have multiple tap interfaces, one per n2n network, so that the same PC can belong to multiple communities.
Quickstart
- Download and compile the code
- Decide where to place your supernode. Suppose you put it on host a.b.c.d at port xyw.
- Decide what encryption password you want to use to secure your data. Suppose you use the password encryptme
- Decide the network name you want to use. Suppose you call it mynetwork. Note that you can use your supernode/edge nodes to handle multiple networks, not just one.
- Decide what IP address you plan to use on your edge nodes. Suppose you use IP address 10.1.2.0/24
- Start your applications:
#supernode > supernode -l xyw #edge node1> edge -a 10.1.2.1 -c mynetwork -k encryptme -l a.b.c.d:xyw #edge node2> edge -a 10.1.2.2 -c mynetwork -k encryptme -l a.b.c.d:xyw
Now test your n2n network:
#edge node1> ping 10.1.2.2 #edge node2> ping 10.1.2.1
※ 執行參考︰
supernode A 5.168.168.6 ─── OpenWrt 路由器 5.168.168.20 ─── edge B 5.168.128.250
【supernode A】
root@kali-pi:~# supernode -l 1234 21/Nov/2018 18:42:03 [supernode.c: 476] Supernode ready: listening on port 1234 [TCP/UDP] 21/Nov/2018 18:42:13 [supernode.c: 119] Registered new node [public_ip=(2)5.168.168.6:36776][private_ip=0.0.0.0:36776][mac=0E:BD:7C:E4:B6:2D][community=mynetwork] 21/Nov/2018 18:43:49 [supernode.c: 119] Registered new node [public_ip=(2)5.168.168.20:37542][private_ip=0.0.0.0:37542][mac=16:6B:C4:FA:61:99][community=mynetwork]
【edge A】
root@kali-pi:~# edge -a 10.1.2.1 -c mynetwork -k encryptme -l 5.168.168.6:1234 10.1.2.1 21/Nov/2018 18:42:13 [ edge.c:1136] Using supernode 5.168.168.6:1234 21/Nov/2018 18:42:13 [tuntap_linux.c: 38] Interface edge0 has MAC 0E:BD:7C:E4:B6:2D 21/Nov/2018 18:42:13 [ edge.c: 670] Registering with supernode 21/Nov/2018 18:42:13 [ edge.c:1367] 21/Nov/2018 18:42:13 [ edge.c:1368] Ready 21/Nov/2018 18:42:13 [ edge.c:1035] Received REGISTER_ACK from remote peer [ip=5.168.168.6:1234] 21/Nov/2018 18:42:13 [ edge.c:1434] STATUS: pending=0, operational=0 21/Nov/2018 18:43:16 [ edge.c: 670] Registering with supernode 21/Nov/2018 18:43:16 [ edge.c:1035] Received REGISTER_ACK from remote peer [ip=5.168.168.6:1234] 21/Nov/2018 18:44:20 [ edge.c: 670] Registering with supernode 21/Nov/2018 18:44:20 [ edge.c:1035] Received REGISTER_ACK from remote peer [ip=5.168.168.6:1234]
root@kali-pi:~# ifconfig
edge0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1400
inet 10.1.2.1 netmask 255.255.255.0 broadcast 10.1.2.255
inet6 fe80::cbd:7cff:fee4:b62d prefixlen 64 scopeid 0x20<link>
ether 0e:bd:7c:e4:b6:2d txqueuelen 1000 (Ethernet)
RX packets 16 bytes 1236 (1.2 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 17 bytes 1314 (1.2 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 5.168.168.6 netmask 255.255.255.0 broadcast 5.168.168.255
inet6 fe80::ba27:ebff:fedb:efad prefixlen 64 scopeid 0x20<link>
ether b8:27:eb:db:ef:ad txqueuelen 1000 (Ethernet)
RX packets 20227495 bytes 1949210996 (1.8 GiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 865121 bytes 114241549 (108.9 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
...
root@kali-pi:~# route Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface default 5.168.168.1 0.0.0.0 UG 0 0 0 eth0 5.168.168.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0 10.1.2.0 0.0.0.0 255.255.255.0 U 0 0 0 edge0
【edge B】
root@kali:~# edge -a 10.1.2.2 -c mynetwork -k encryptme -l 5.168.168.6:1234 10.1.2.2 21/Nov/2018 07:43:49 [ edge.c:1136] Using supernode 5.168.168.6:1234 21/Nov/2018 07:43:49 [tuntap_linux.c: 38] Interface edge0 has MAC 16:6B:C4:FA:61:99 21/Nov/2018 07:43:49 [ edge.c: 670] Registering with supernode 21/Nov/2018 07:43:49 [ edge.c:1367] 21/Nov/2018 07:43:49 [ edge.c:1368] Ready 21/Nov/2018 07:43:49 [ edge.c:1035] Received REGISTER_ACK from remote peer [ip=5.168.168.6:1234] 21/Nov/2018 07:43:49 [ edge.c:1434] STATUS: pending=0, operational=0 21/Nov/2018 07:44:49 [ edge.c: 670] Registering with supernode 21/Nov/2018 07:44:49 [ edge.c:1035] Received REGISTER_ACK from remote peer [ip=5.168.168.6:1234] 21/Nov/2018 07:45:55 [ edge.c: 670] Registering with supernode 21/Nov/2018 07:45:55 [ edge.c:1035] Received REGISTER_ACK from remote peer [ip=5.168.168.6:1234]
root@kali:~# ifconfig
edge0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1400
inet 10.1.2.2 netmask 255.255.255.0 broadcast 10.1.2.255
inet6 fe80::146b:c4ff:fefa:6199 prefixlen 64 scopeid 0x20<link>
ether 16:6b:c4:fa:61:99 txqueuelen 1000 (Ethernet)
RX packets 7 bytes 518 (518.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 17 bytes 1306 (1.2 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 5.168.128.250 netmask 255.255.255.0 broadcast 5.168.128.255
inet6 fe80::ba27:ebff:fec2:b06e prefixlen 64 scopeid 0x20<link>
ether b8:27:eb:c2:b0:6e txqueuelen 1000 (Ethernet)
RX packets 346585 bytes 212092128 (202.2 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 293387 bytes 54265187 (51.7 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
...
root@kali:~# route Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface default 5.168.128.66 0.0.0.0 UG 0 0 0 eth0 5.168.128.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0 10.1.2.0 0.0.0.0 255.255.255.0 U 0 0 0 edge0
【A ssh B】
root@kali-pi:~# ssh -l root 10.1.2.2 The authenticity of host '10.1.2.2 (10.1.2.2)' can't be established. ECDSA key fingerprint is SHA256:+k1xOqFbG0NPv4aFzHT6Dd+iD3O6sWJALOXInXZxiZg. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '10.1.2.2' (ECDSA) to the list of known hosts. root@10.1.2.2's password: Linux kali 4.9.59-v7_Re4son-Kali-Pi+ #1 SMP Wed Feb 14 20:50:28 CST 2018 armv7l The programs included with the Kali GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Kali GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law.
關心未來發展者,自可到此處呀◎
/n2n
A development branch of the n2n p2p vpn software https://github.com/ntop/n2n
This is a development branch of the n2n p2p vpn software.
It contains some modifications of the v2 version of n2n, which is the latest stable version
and should be used for productive environments.
All the current development happens in this repository in the new_protocol branch, which is
intended to be come version v3 of n2n and then merged back into the original svn repository
on ntop.org.
Uses sglib http://sglib.sourceforge.net.
For further information please visit the wiki https://github.com/meyerd/n2n/wiki.