在《火把節》一文中,我們談過古早的『十月曆』︰
如果說商代甲骨文已有『十天干』和『十二地支』,龜卜上用『六十甲子』以紀時,商王很多用『天干』為名,那麼『后羿射日』與『嫦娥奔月』的傳說,很可能是驚天動地神話了的『歷法變革』︰
傳說堯時,十日並出草木枯亡,又有猰貐、鑿齒、九嬰、大風、封豨、修蛇等等惡獸四方作怪,后羿受堯之命去除惡獸並使射九日,為民除害。……又說后羿之妻為嫦娥,后羿因希望永世能『執子之手, 與子偕老』,求『不死藥』於西王母處,共得了『兩顆』。不知怎的嫦娥卻是乘著后羿外出,獨自將藥全吃了,就飄飄然的飛向了月宮。……其後或聞,她為了再返還人間,一直叫著月兔搗藥!!
這個『日月之戀』是否已然大『明』於天下,作者不得而知;或有人將要說︰
難怪今天日月總不愛相見,祇會之於朔望。
,恐有人又以為,甲骨文上早有的『十二生肖』,自是出自『這個緣故』!!
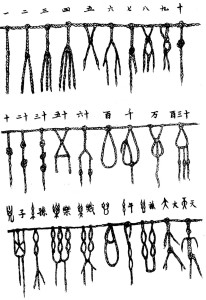
有人以 ![]() 乙為『繩子』,
乙為『繩子』,![]() 己為『結繩』,訴說那上古之『結繩而治』,這些先於『文字』的『符號』,象徵著人類的『抽象化』本事,早在能夠
己為『結繩』,訴說那上古之『結繩而治』,這些先於『文字』的『符號』,象徵著人類的『抽象化』本事,早在能夠 ![]() 『記』『言』之前,遺留給後人的古早『記憶』!在此冀望『梅雨』的暮春時節,也許張先之詞,能帶人入夢,通往那遙遠的過去,
『記』『言』之前,遺留給後人的古早『記憶』!在此冀望『梅雨』的暮春時節,也許張先之詞,能帶人入夢,通往那遙遠的過去,
北宋‧張先《千秋歲》
數聲鶗,
又報芳菲歇。
惜春更選殘紅折。
雨輕風色暴,
梅子青時節。
永豐柳,
無人盡日花飛雪。
莫把么弦撥,
怨極弦能說。
天不老,
情難絕,
心似雙絲網,
中有千千結。
夜過也,
東窗未白孤燈滅。
,一『解』心有『千千結』的吧!!
或許有人曾經聽聞『天上三奇』甲戊庚,『人中三奇』壬癸辛,『地下三奇』乙丙丁,為何十天干中,捨『己』不用?也許好奇者可窺之於
大易總敘章第一
乾坤者,易之門戶,眾卦之父母。坎離匡廓,運轂正軸,牝牡四卦,以為橐蒼。覆冒陰陽之道,尤工御者准繩墨,執銜轡,正規距 ,隨軌轍,處中以制外,數在律歷紀。月節有五六,經緯奉日使,兼并為六十,剛柔有表里。朔旦屯直事,至暮蒙當受,晝夜各一卦用之依次序。即未至晦爽,終則復更始,日月為期度,動靜有早晚 。春夏據內體,從子到辰巳,秋冬當外用,自午訖戌亥。賞罰應春秋,昏明順寒暑,爻辭有仁義,隨時發喜怒,如是應四時,五行得其理。
乾坤設位章第二
天地設位,而易行乎其中。天地者,乾坤之象也﹔設位者,列陰陽配合之位也﹔易謂坎離者,乾坤二用。二用無爻位,周流行六虛,往來既不定,上下亦無常,幽潛淪匿,變化于中,包囊萬物,為道紀綱,以無制有,器用者空,故推消息,坎離沒亡。言不苟造,論不虛生,引驗見效,校度神明,推論結字,原理為証。
坎戊月精,離己日光,日月為易,剛柔相當,土旺四季,羅絡始終,青赤黑白,各居一方,皆秉中宮,戊己之功。
,這個『日光』豈是可『獨享者』耶??
─── 《《派生》 PYTHON 作坊【乙】選址定基》
坎月戊望時節,萬物皆相見耶?
Rootkit
A rootkit is a collection of computer software, typically malicious, designed to enable access to a computer or areas of its software that is not otherwise allowed (for example, to an unauthorized user) and often masks its existence or the existence of other software.[1] The term rootkit is a concatenation of “root” (the traditional name of the privileged account on Unix-like operating systems) and the word “kit” (which refers to the software components that implement the tool). The term “rootkit” has negative connotations through its association with malware.[1]
Rootkit installation can be automated, or an attacker can install it after having obtained root or Administrator access. Obtaining this access is a result of direct attack on a system, i.e. exploiting a known vulnerability (such as privilege escalation) or a password (obtained by cracking or social engineering tactics like “phishing“). Once installed, it becomes possible to hide the intrusion as well as to maintain privileged access. The key is the root or administrator access. Full control over a system means that existing software can be modified, including software that might otherwise be used to detect or circumvent it.
Rootkit detection is difficult because a rootkit may be able to subvert the software that is intended to find it. Detection methods include using an alternative and trusted operating system, behavioral-based methods, signature scanning, difference scanning, and memory dump analysis. Removal can be complicated or practically impossible, especially in cases where the rootkit resides in the kernel; reinstallation of the operating system may be the only available solution to the problem.[2] When dealing with firmware rootkits, removal may require hardware replacement, or specialized equipment.
History
The term rootkit or root kit originally referred to a maliciously modified set of administrative tools for a Unix-like operating system that granted “root” access.[3] If an intruder could replace the standard administrative tools on a system with a rootkit, the intruder could obtain root access over the system whilst simultaneously concealing these activities from the legitimate system administrator. These first-generation rootkits were trivial to detect by using tools such as Tripwire that had not been compromised to access the same information.[4][5] Lane Davis and Steven Dake wrote the earliest known rootkit in 1990 for Sun Microsystems‘ SunOS UNIX operating system.[6] In the lecture he gave upon receiving the Turing award in 1983, Ken Thompson of Bell Labs, one of the creators of Unix, theorized about subverting the C compiler in a Unix distribution and discussed the exploit. The modified compiler would detect attempts to compile the Unix login command and generate altered code that would accept not only the user’s correct password, but an additional “backdoor” password known to the attacker. Additionally, the compiler would detect attempts to compile a new version of the compiler, and would insert the same exploits into the new compiler. A review of the source code for the login command or the updated compiler would not reveal any malicious code.[7] This exploit was equivalent to a rootkit.
The first documented computer virus to target the personal computer, discovered in 1986, used cloaking techniques to hide itself: the Brain virus intercepted attempts to read the boot sector, and redirected these to elsewhere on the disk, where a copy of the original boot sector was kept.[1] Over time, DOS-virus cloaking methods became more sophisticated, with advanced techniques including the hooking of low-level disk INT 13H BIOS interrupt calls to hide unauthorized modifications to files.[1]
The first malicious rootkit for the Windows NT operating system appeared in 1999: a trojan called NTRootkit created by Greg Hoglund.[8] It was followed by HackerDefender in 2003.[1] The first rootkit targeting Mac OS X appeared in 2009,[9] while the Stuxnet worm was the first to target programmable logic controllers (PLC).[10]
Sony BMG copy protection rootkit scandal
Main article: Sony BMG copy protection rootkit scandal
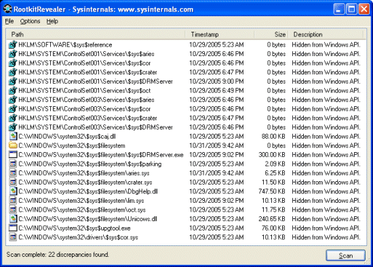
In 2005, Sony BMG published CDs with copy protection and digital rights management software called Extended Copy Protection, created by software company First 4 Internet. The software included a music player but silently installed a rootkit which limited the user’s ability to access the CD.[11] Software engineer Mark Russinovich, who created the rootkit detection tool RootkitRevealer, discovered the rootkit on one of his computers.[1] The ensuing scandal raised the public’s awareness of rootkits.[12] To cloak itself, the rootkit hid from the user any file starting with “$sys$”. Soon after Russinovich’s report, malware appeared which took advantage of that vulnerability of affected systems.[1] One BBC analyst called it a “public relations nightmare.”[13] Sony BMG released patches to uninstall the rootkit, but it exposed users to an even more serious vulnerability.[14] The company eventually recalled the CDs. In the United States, a class-action lawsuit was brought against Sony BMG.[15]
幽深隱微,有事不可睹乎!
Kernel, Hypervisor, Virtualization, Trusted Computing and other system-level security stuff
Thursday, June 22, 2006
Introducing Blue Pill
About Me
All the current rootkits and backdoors, which I am aware of, are based on a concept. For example: FU was based on an idea of unlinking EPROCESS blocks from the kernel list of active processes, Shadow Walker was based on a concept of hooking the page fault handler and marking some pages as invalid, deepdoor on changing some fields in NDIS data structure, etc… Once you know the concept you can (at least theoretically) detect the given rootkit.
Now, imagine a malware (e.g. a network backdoor, keylogger, etc…) whose capabilities to remain undetectable do not rely on obscurity of the concept. Malware, which could not be detected even though its algorithm (concept) is publicly known. Let’s go further and imagine that even its code could be made public, but still there would be no way for detecting that this creature is running on our machines…
Over the past few months I have been working on a technology code-named Blue Pill, which is just about that – creating 100% undetectable malware, which is not based on an obscure concept.
 The idea behind Blue Pill is simple: your operating system swallows the Blue Pill and it awakes inside the Matrix controlled by the ultra thin Blue Pill hypervisor. This all happens on-the-fly (i.e. without restarting the system) and there is no performance penalty and all the devices, like graphics card, are fully accessible to the operating system, which is now executing inside virtual machine. This is all possible thanks to the latest virtualization technology from AMD called SVM/Pacifica.
The idea behind Blue Pill is simple: your operating system swallows the Blue Pill and it awakes inside the Matrix controlled by the ultra thin Blue Pill hypervisor. This all happens on-the-fly (i.e. without restarting the system) and there is no performance penalty and all the devices, like graphics card, are fully accessible to the operating system, which is now executing inside virtual machine. This is all possible thanks to the latest virtualization technology from AMD called SVM/Pacifica.
………
※ 原始碼︰
www.invisiblethingslab.com/resources/bh07/nbp-0.32-public.zip
如何選擇一顆小藥丸呦☆
Blue Pill (software)
Blue Pill is the codename for a rootkit based on x86 virtualization. Blue Pill originally required AMD-V (Pacifica) virtualization support, but was later ported to support Intel VT-x (Vanderpool) as well. It was designed by Joanna Rutkowska and originally demonstrated at the Black Hat Briefings on August 3, 2006, with a reference implementation for the Microsoft Windows Vista kernel.
The name is a reference to the red pill and blue pill concept from the 1999 film The Matrix.
Overview
The Blue Pill concept is to trap a running instance of the operating system by starting a thin hypervisor and virtualizing the rest of the machine under it. The previous operating system would still maintain its existing references to all devices and files, but nearly anything, including hardware interrupts, requests for data and even the system time could be intercepted (and a fake response sent) by the hypervisor. The original concept of Blue Pill was published by another researcher at IEEE Oakland on May 2006, under the name VMBR (virtual-machine based rootkit).[1]
Joanna Rutkowska claims that, since any detection program could be fooled by the hypervisor, such a system could be “100% undetectable”. Since AMD virtualization is seamless by design, a virtualized guest is not supposed to be able to query whether it is a guest or not. Therefore, the only way Blue Pill could be detected is if the virtualization implementation were not functioning as specified.[2]
This assessment, repeated in numerous press articles, is disputed: AMD issued a statement dismissing the claim of full undetectability.[3] Some other security researchers and journalists also dismissed the concept as implausible.[4] Virtualization could be detected by atiming attack relying on external sources of time.[5]
In 2007, a group of researchers led by Thomas Ptacek of Matasano Security challenged Rutkowska to put Blue Pill against their rootkit detector software at that year’s Black Hat conference,[6] but the deal was deemed a no-go following Rutkowska’s request for $384,000 in funding as a prerequisite for entering the competition.[7] Rutkowska and Alexander Tereshkin countered detractors’ claims during a subsequent Black Hat speech, arguing that the proposed detection methods were inaccurate.[8]
The source code for Blue Pill has since been made public,[9][10] under the following license: Any unauthorized use (including publishing and distribution) of this software requires a valid license from the copyright holder. This software has been provided for the educational use only during the Black Hat training and conference.[11]
Red Pill
Red Pill is a technique to detect the presence of a virtual machine also developed by Joanna Rutkowska.[12]