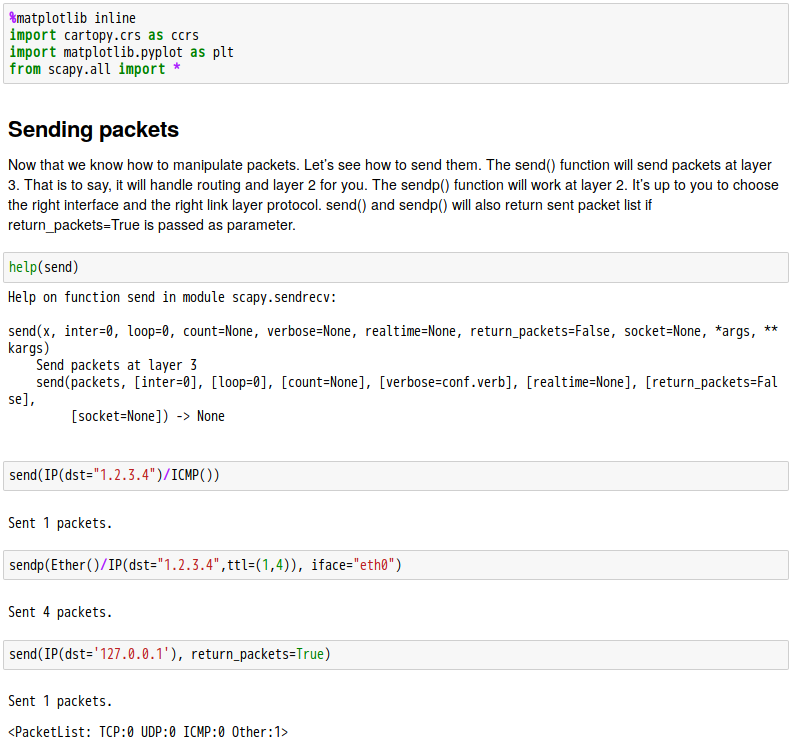
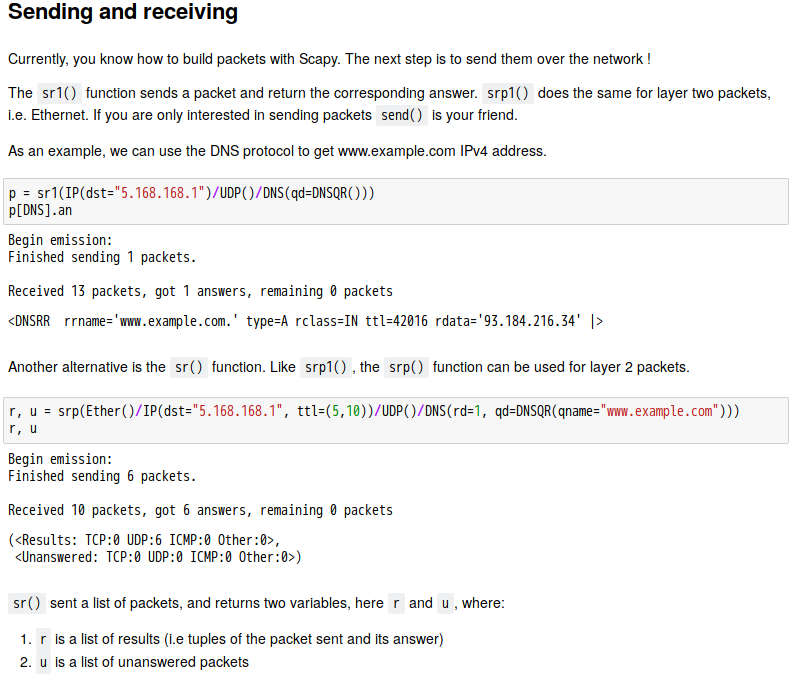
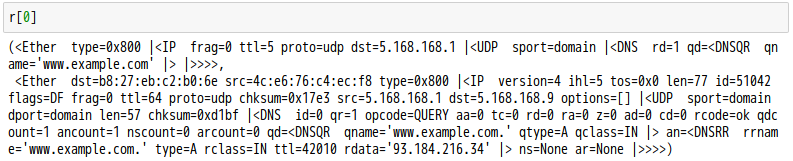
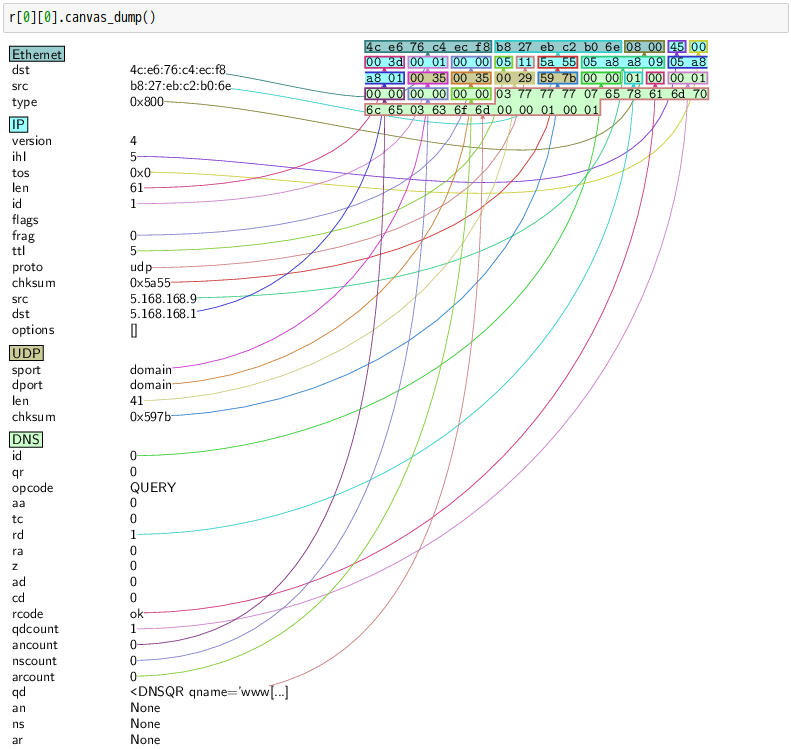
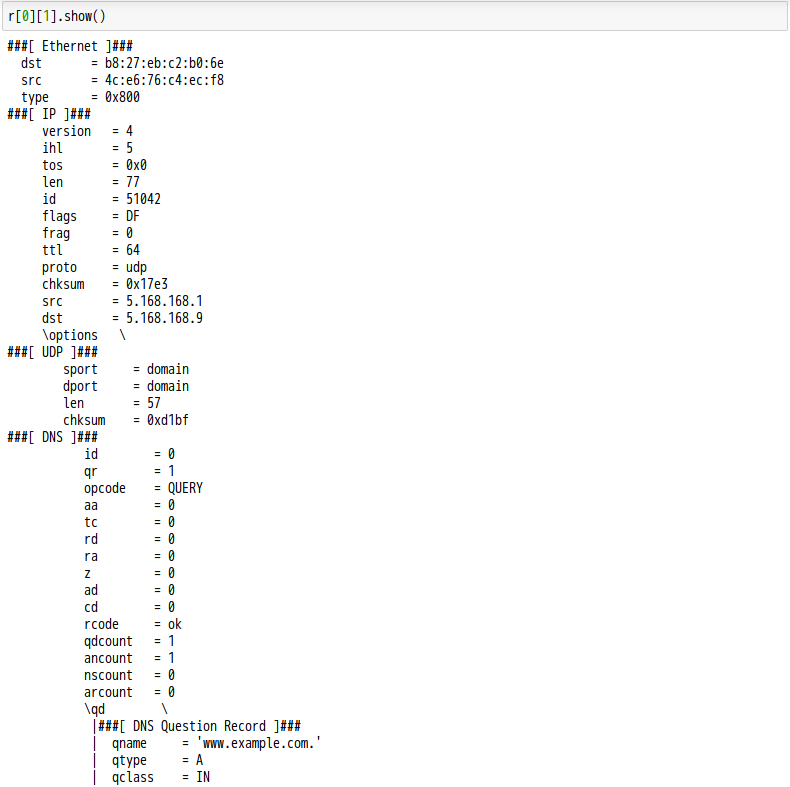
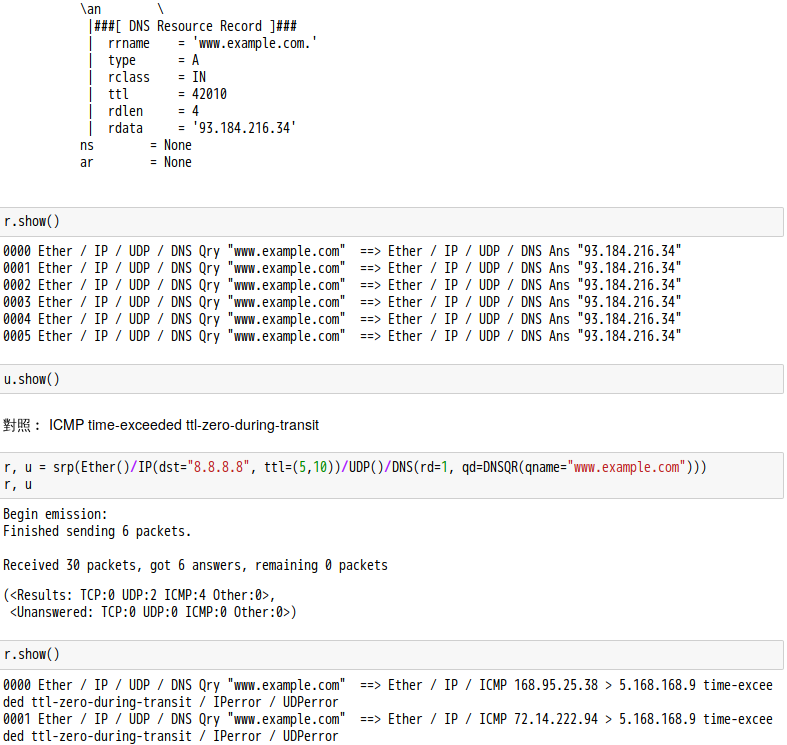
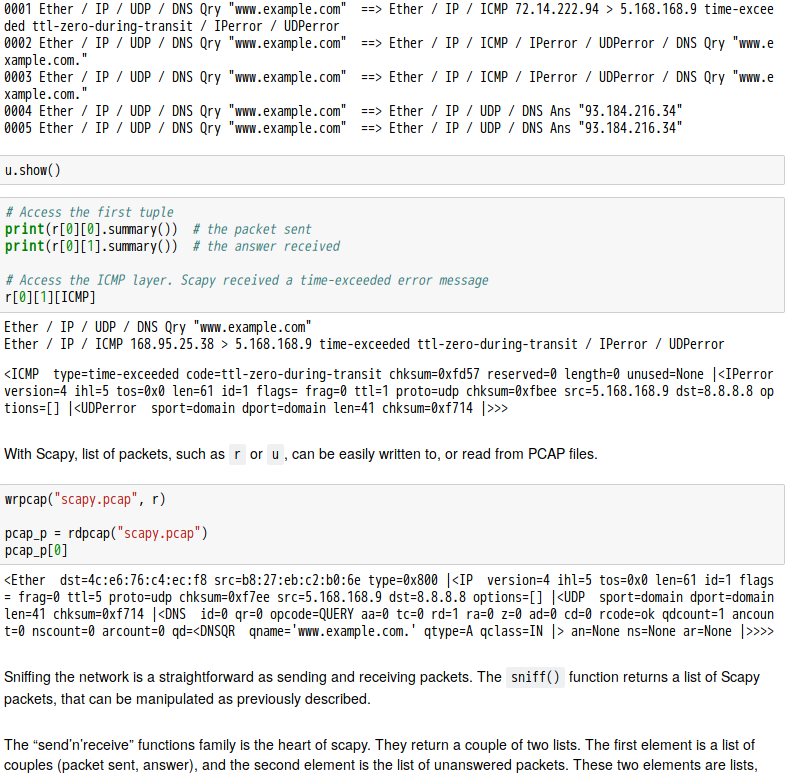
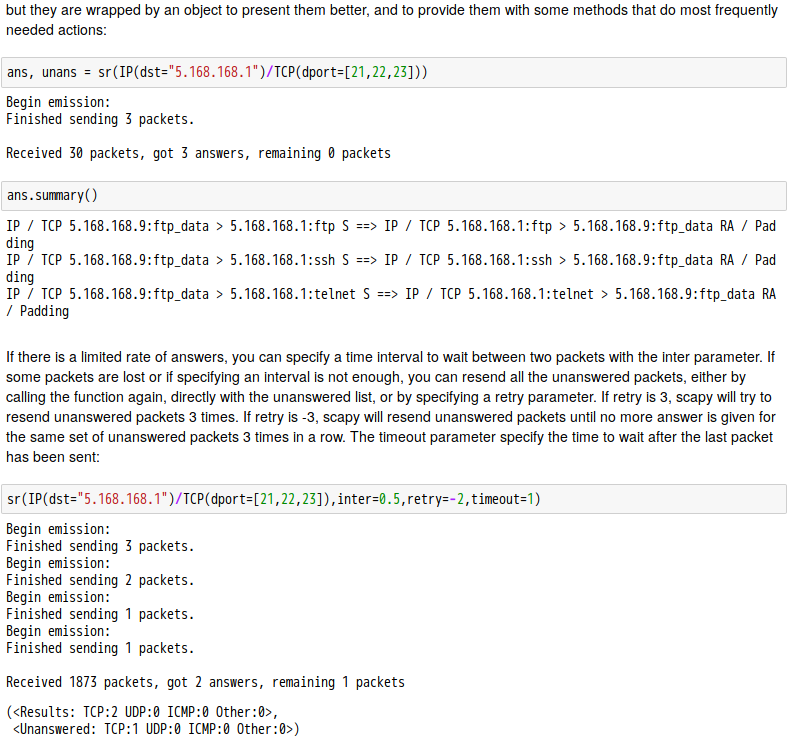
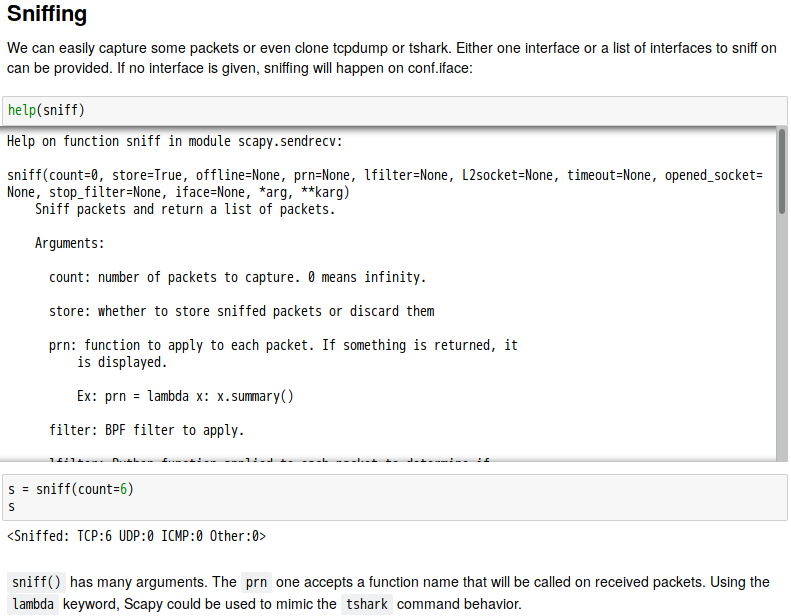
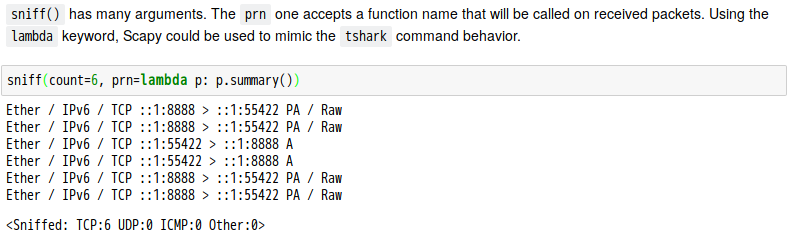
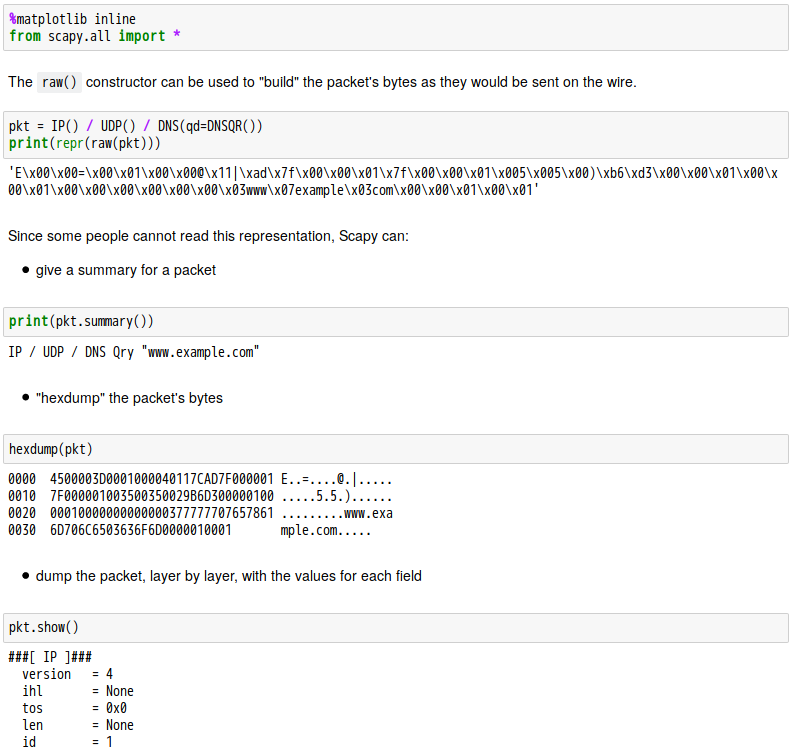
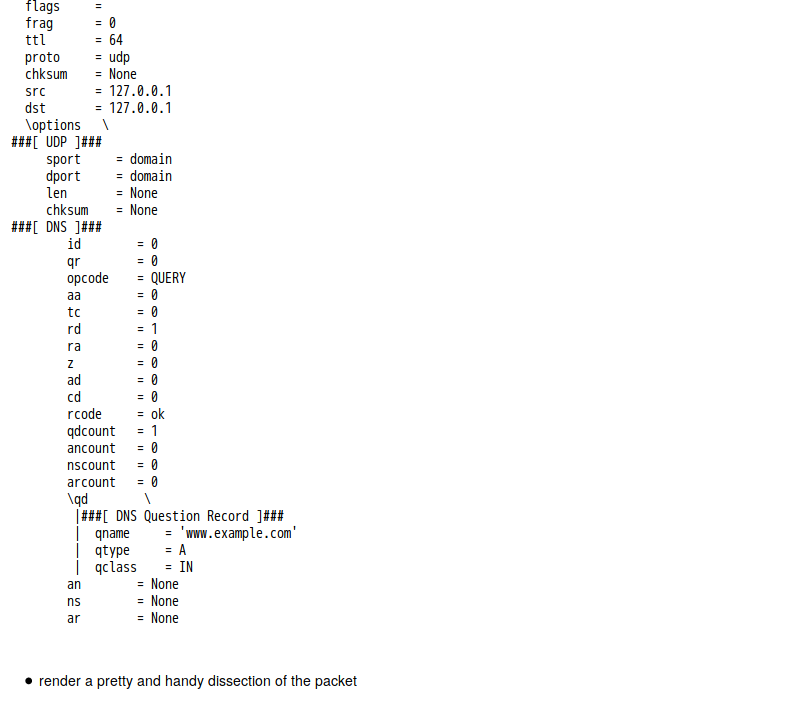
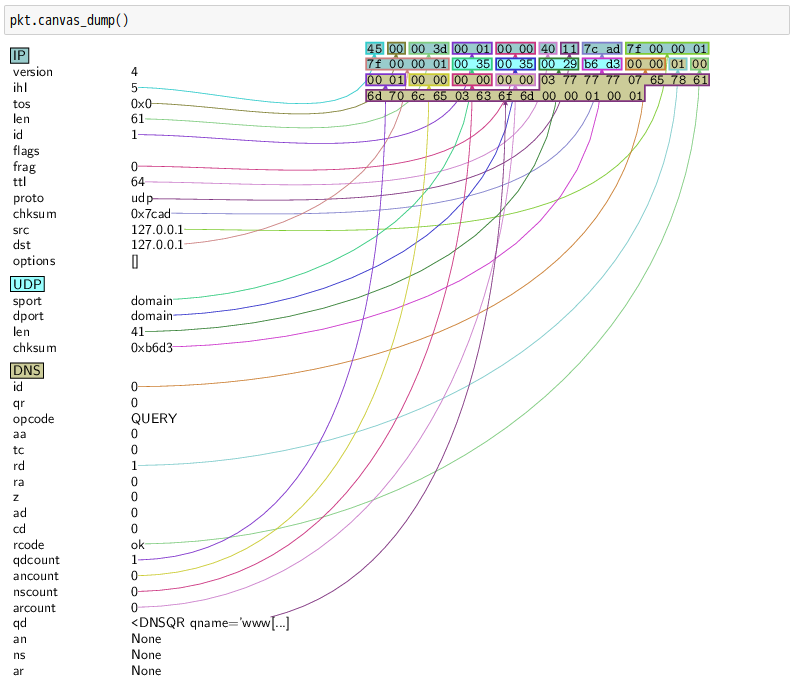
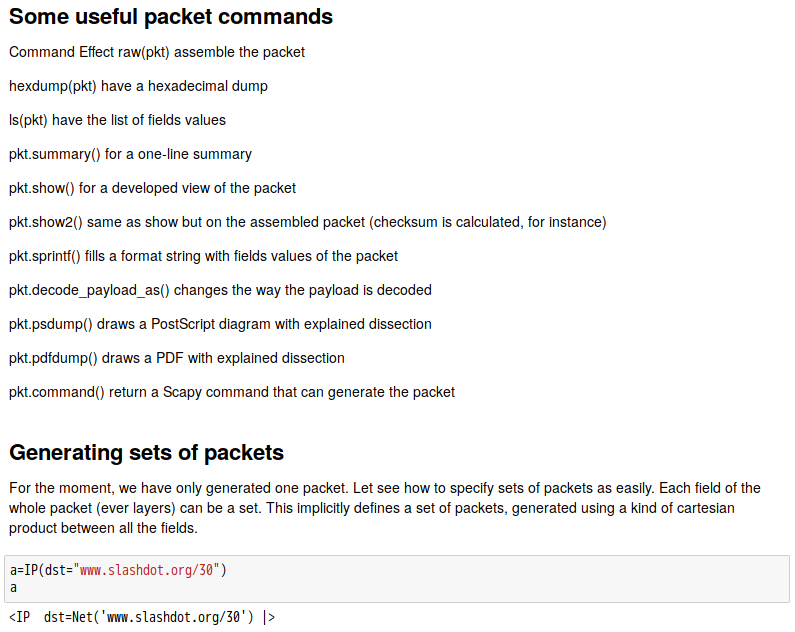
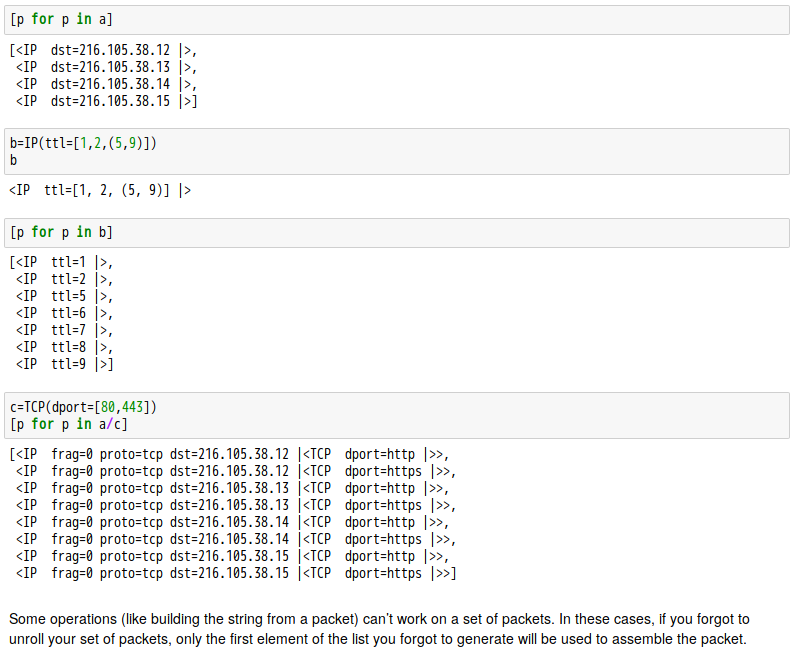
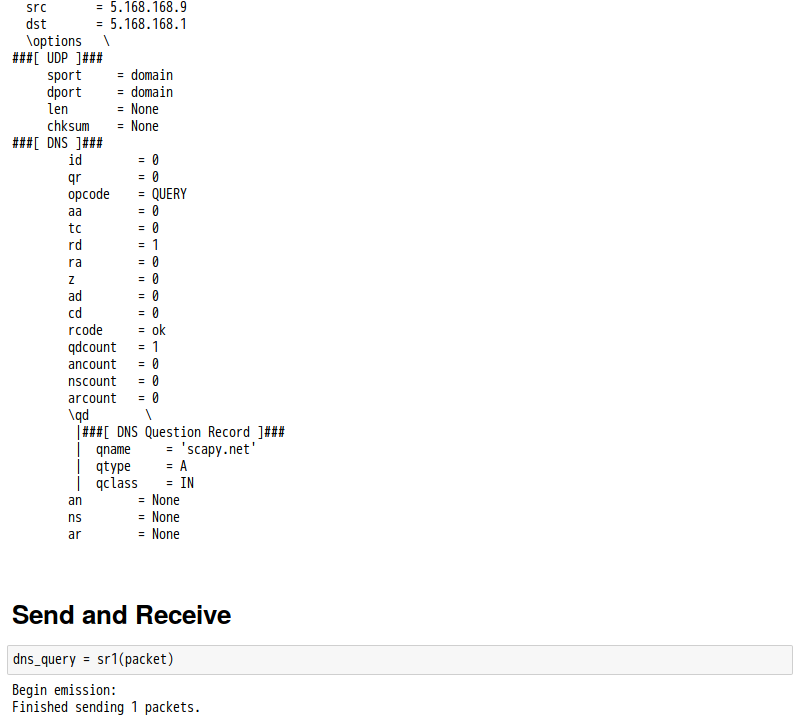
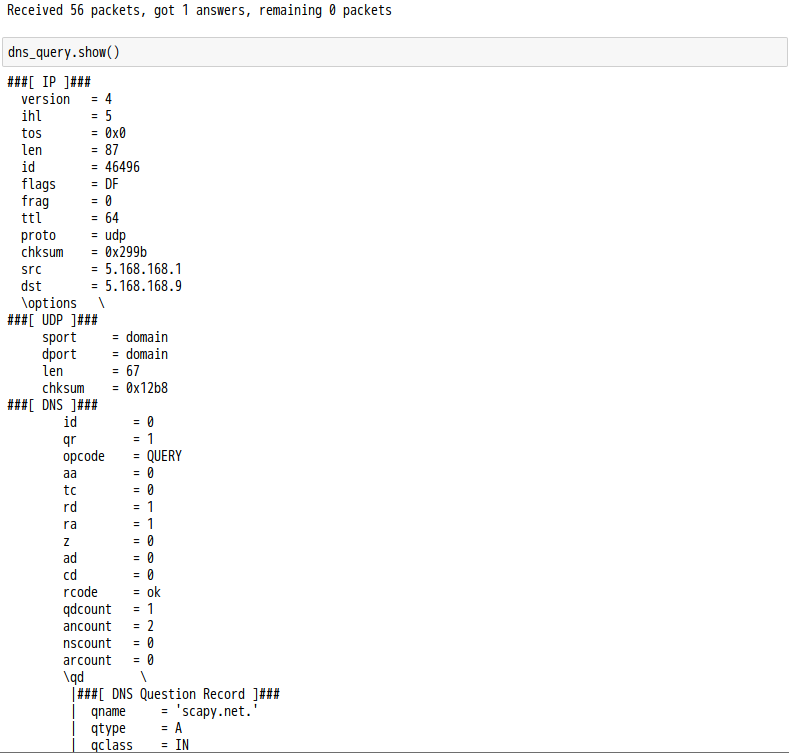
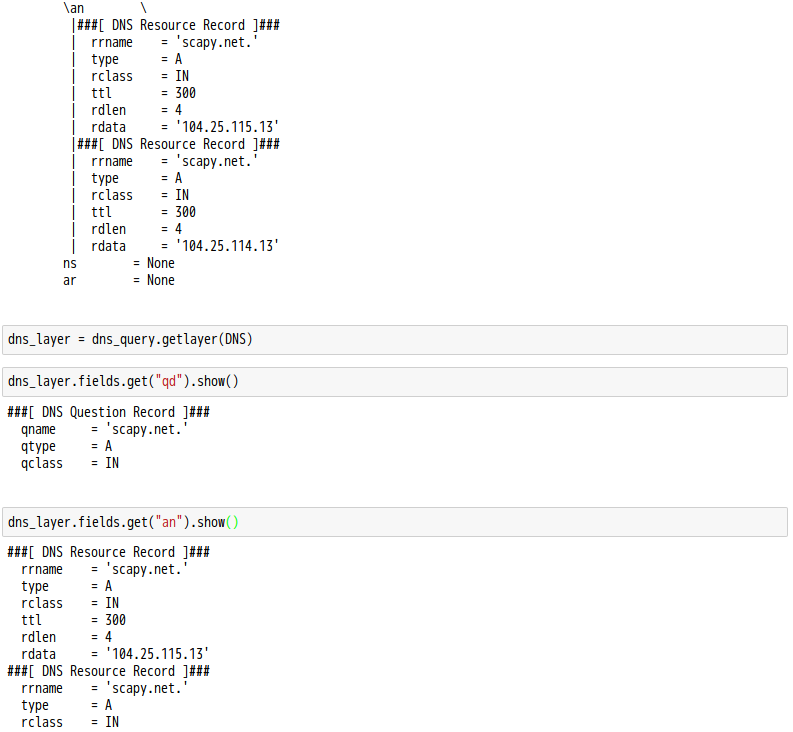
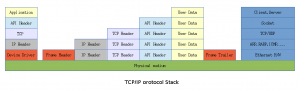
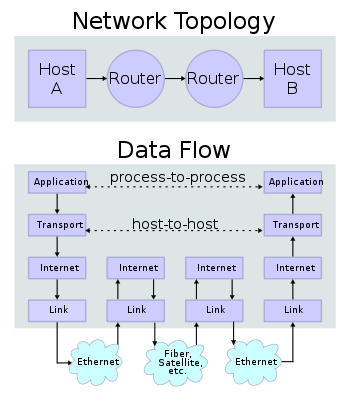
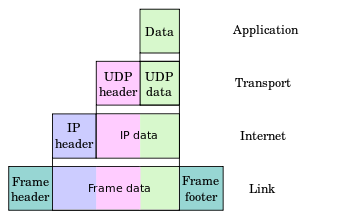
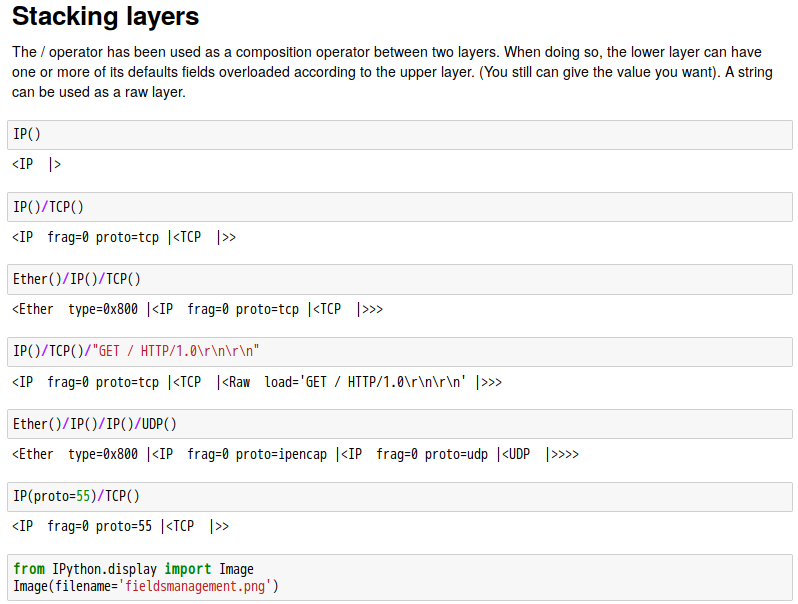
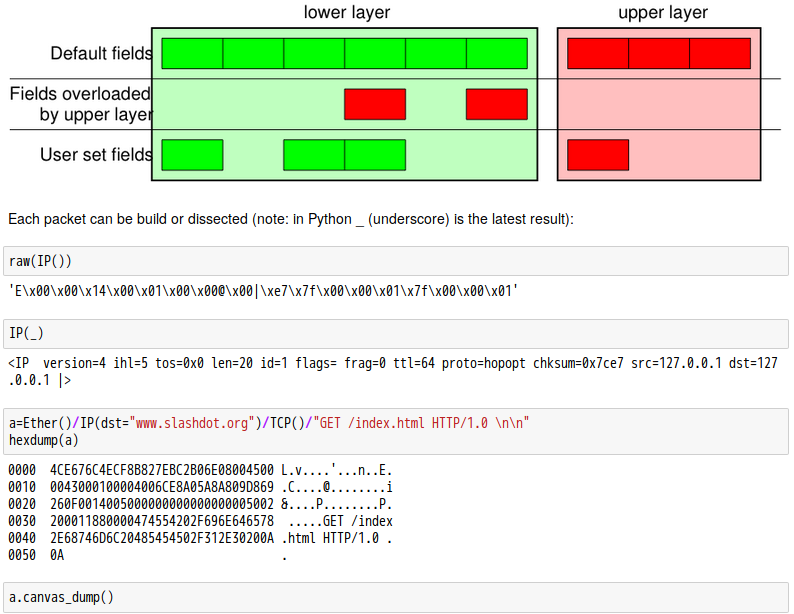
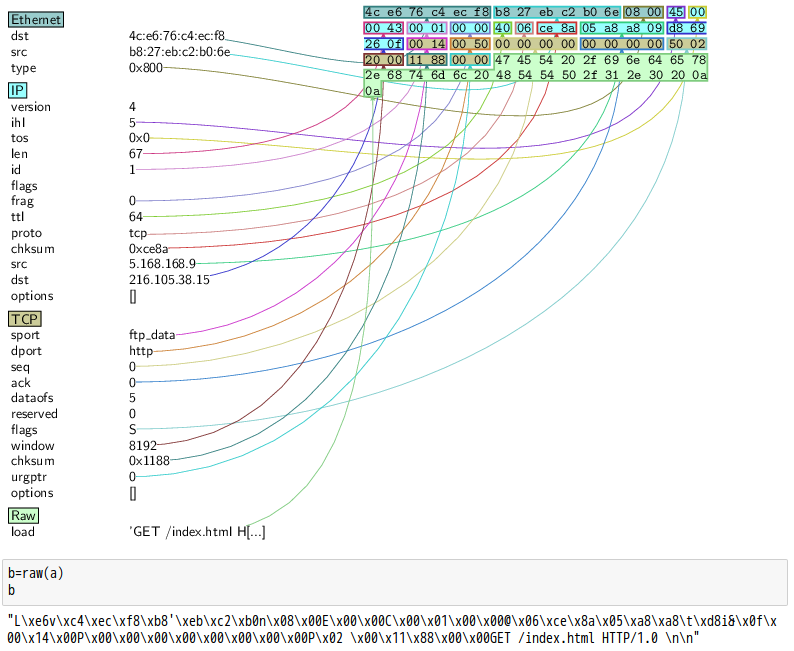
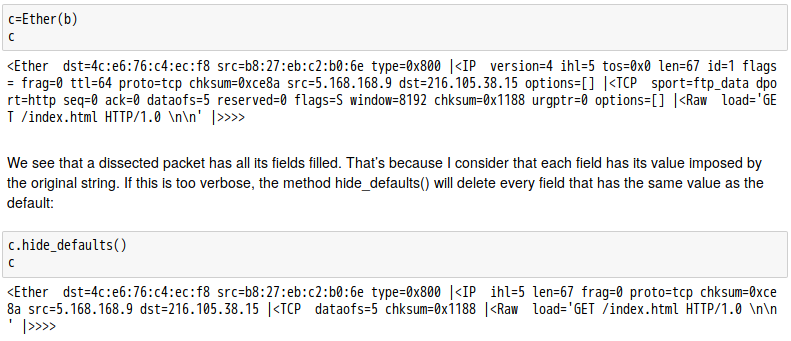
話說 Scapy 裡有一個
Traceroute
In computing, traceroute is a computer network diagnostic tool for displaying the route (path) and measuring transit delays of packets across an Internet Protocol (IP) network. The history of the route is recorded as the round-trip times of the packets received from each successive host (remote node) in the route (path); the sum of the mean times in each hop is a measure of the total time spent to establish the connection. Traceroute proceeds unless all (three) sent packets are lost more than twice, then the connection is lost and the route cannot be evaluated. Ping, on the other hand, only computes the final round-trip times from the destination point.
The command traceroute is available on many modern operating systems. On Unix-like systems such as FreeBSD, macOS, and Linux it is available as a command line tool. Traceroute is also graphically accessible in macOS within the Network Utilities suite. OnMicrosoft Windows and ReactOS, it is named tracert. Windows NT-based operating systems also provide PathPing, with similar functionality. For Internet Protocol Version 6 (IPv6) the tool sometimes has the name traceroute6 or tracert6.
Implementation
On Unix-like operating systems, traceroute sends, by default, a sequence of User Datagram Protocol (UDP) packets, with destination port numbers ranging from 33434 to 33534; the implementations of traceroute shipped with Linux,[1] FreeBSD,[2] NetBSD,[3]OpenBSD,[4] DragonFly BSD,[5] and macOS include an option to use ICMP Echo Request packets (-I), or any arbitrary protocol (-P) such as UDP, TCP using TCP SYN packets, or ICMP.[6] In Windows, traceroute sends ICMP echo requests instead of UDP packets.[7]
The time-to-live (TTL) value, also known as hop limit, is used in determining the intermediate routers being traversed towards the destination. Traceroute sends packets with TTL values that gradually increase from packet to packet, starting with TTL value of one. Routers decrement TTL values of packets by one when routing and discard packets whose TTL value has reached zero, returning the ICMP error message ICMP Time Exceeded.[6] For the first set of packets, the first router receives the packet, decrements the TTL value and drops the packet because it then has TTL value zero. The router sends an ICMP Time Exceeded message back to the source. The next set of packets are given a TTL value of two, so the first router forwards the packets, but the second router drops them and replies with ICMP Time Exceeded. Proceeding in this way, traceroute uses the returned ICMP Time Exceeded messages to build a list of routers that packets traverse, until the destination is reached and returns an ICMP Echo Reply message.[6]
The timestamp values returned for each router along the path are the delay (latency) values, typically measured in milliseconds for each packet.
The sender expects a reply within a specified number of seconds. If a packet is not acknowledged within the expected interval, an asterisk is displayed. The Internet Protocol does not require packets to take the same route towards a particular destination, thus hosts listed might be hosts that other packets have traversed. If the host at hop #N does not reply, the hop is skipped in the output.
If a network has a firewall and operates both Windows and Unix-like systems, more than one protocol must be enabled inbound through the firewall for traceroute to work and receive replies.
Some traceroute implementations use TCP packets, such as tcptraceroute and layer four traceroute. PathPing is a utility introduced with Windows NT that combines ping and traceroute functionality. MTR is an enhanced version of ICMP traceroute available for Unix-like and Windows systems. The various implementations of traceroute all rely on ICMP Time Exceeded (type 11) packets being sent to the source.
On Linux, tracepath is a utility similar to traceroute, with the primary difference of not requiring superuser privileges.[8]
Cisco‘s implementation of traceroute also uses a sequence of UDP datagrams, each with incrementing TTL values, to an invalid port number at the remote host; by default, UDP port 33434 is used. An extended version of this command (known as the extended traceroute command) can change the destination port number used by the UDP probe messages.[9]
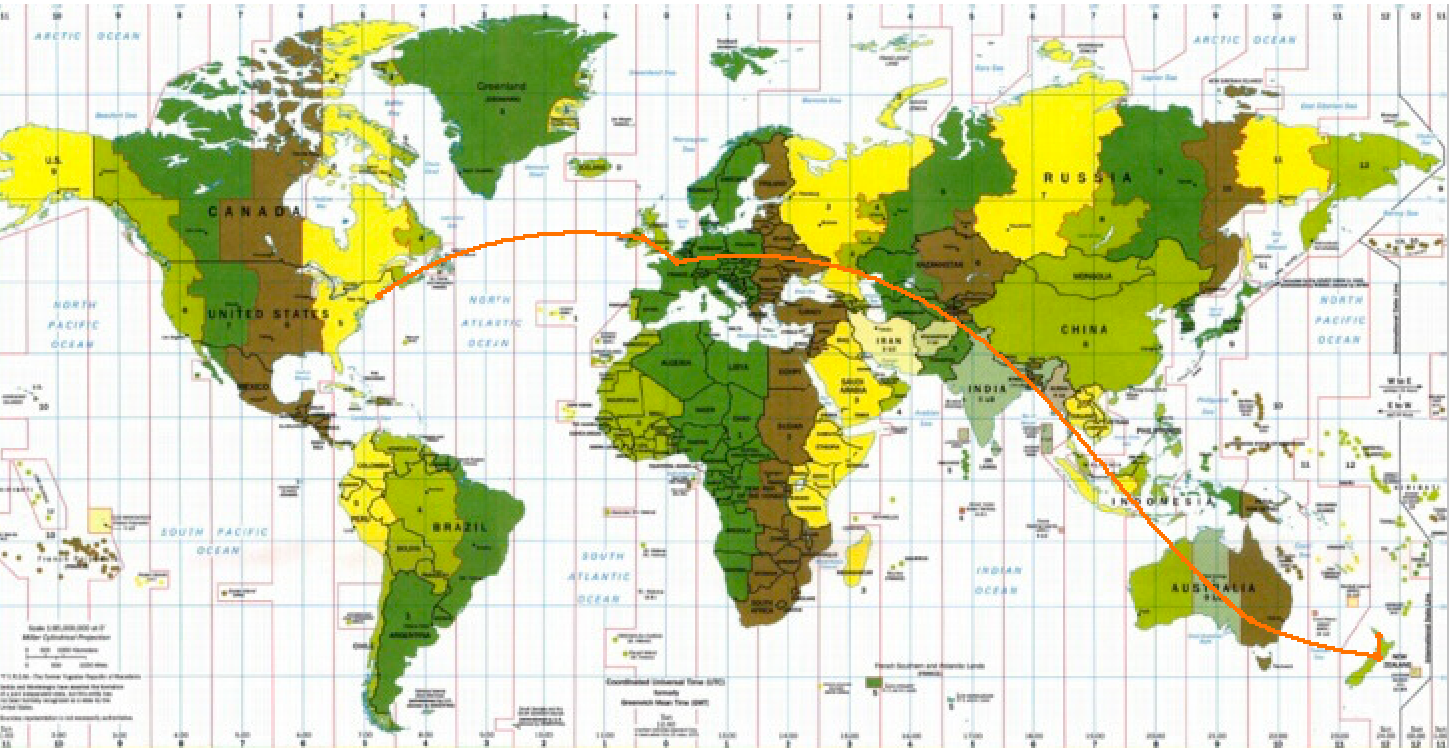
Router addresses can be superimposed upon maps of their physical locations. This example shows a request fromNew Zealand to an IP in Massachusetts which takes a route that passes through Europe.
指令,依著使用手冊講解
TCP traceroute
……
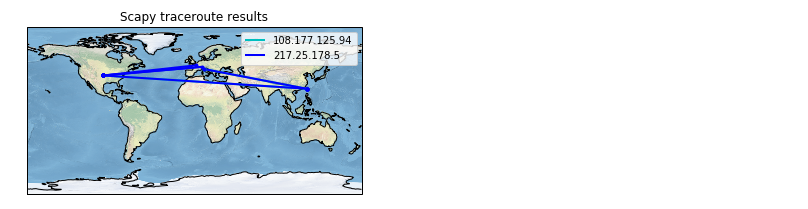
Scapy may also use the GeoIP2 module, in combination with matplotlib and cartopy to generate fancy graphics such as below:
Scapy may also use the GeoIP2 module, in combination with matplotlib and cartopy to generate fancy graphics such as below:
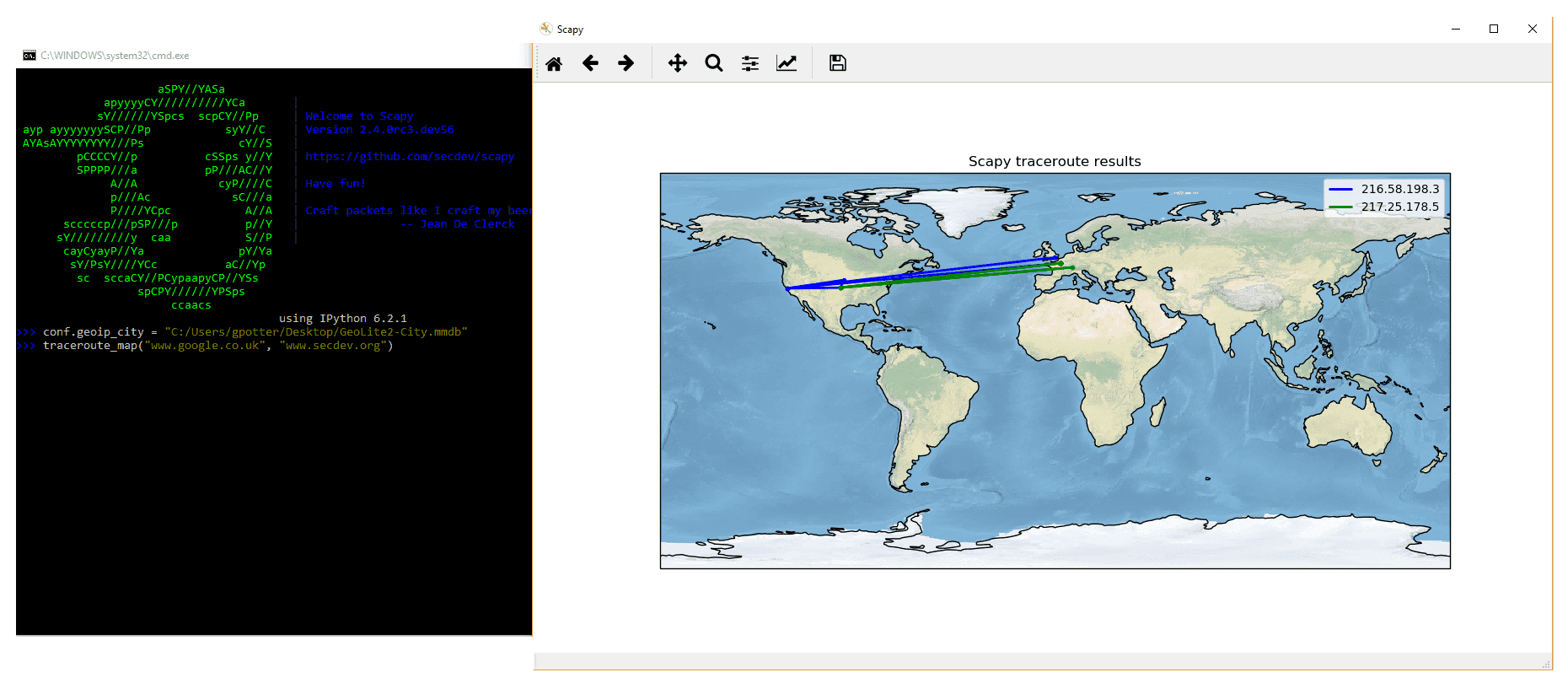
In this example, we used the traceroute_map() function to print the graphic. This method is a shortcut which uses the world_trace of the TracerouteResult objects. It could have been done differently:
>>> conf.geoip_city = "path/to/GeoLite2-City.mmdb" >>> a = traceroute(["www.google.co.uk", "www.secdev.org"], verbose=0) >>> a.world_trace()
or such as above:
>>> conf.geoip_city = "path/to/GeoLite2-City.mmdb" >>> traceroute_map(["www.google.co.uk", "www.secdev.org"])
To use those functions, it is required to have installed the geoip2 module, its database (direct download) but also the cartopy module.
果然行禮如儀呦☺
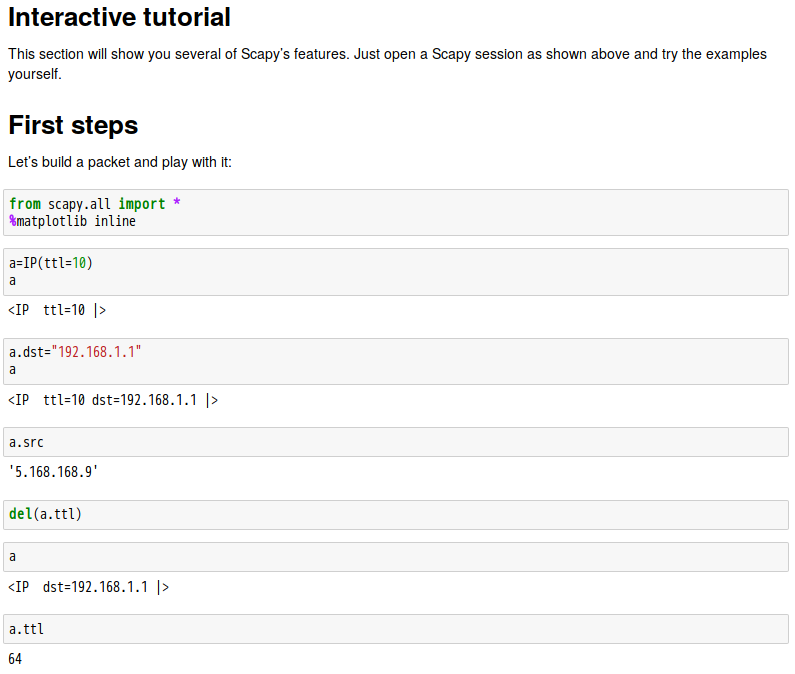
root@kali:~# python Python 2.7.15+ (default, Aug 31 2018, 11:56:52) [GCC 8.2.0] on linux2 Type "help", "copyright", "credits" or "license" for more information. >>> from scapy.all import * >>> conf.geoip_city = "/root/test/GeoLite2-City_20181030/GeoLite2-City.mmdb" >>> ans,uans = traceroute(["www.google.co.uk", "www.secdev.org"], verbose=0) >>> ans.world_trace()
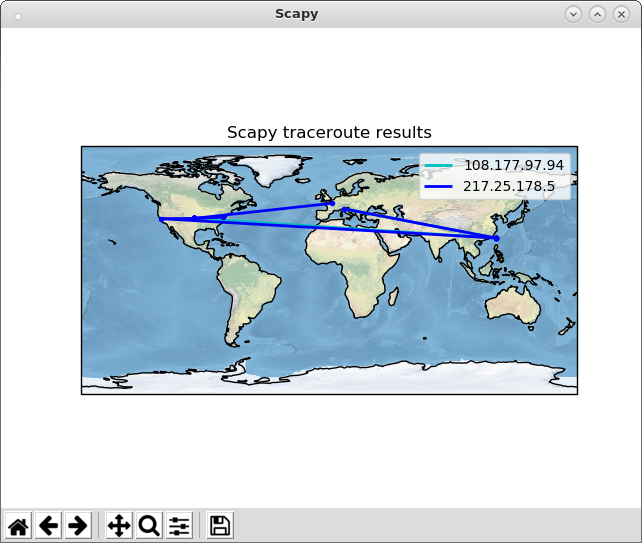
【After closing the Scapy window】
>>> [<matplotlib.collections.LineCollection object at 0x6cf7f4f0>, [<matplotlib.lines.Line2D object at 0x6ced7570>], [<matplotlib.lines.Line2D object at 0x6ced76d0>], [<matplotlib.lines.Line2D object at 0x6ced7670>], [<matplotlib.lines.Line2D object at 0x6ced7950>], [<matplotlib.lines.Line2D object at 0x6ced7bf0>], [<matplotlib.lines.Line2D object at 0x6ced7e90>], [<matplotlib.lines.Line2D object at 0x6ceee170>], [<matplotlib.lines.Line2D object at 0x6ceee430>], <matplotlib.collections.LineCollection object at 0x6ced75b0>, [<matplotlib.lines.Line2D object at 0x6cef7030>], [<matplotlib.lines.Line2D object at 0x6cef7090>], [<matplotlib.lines.Line2D object at 0x6cef7130>], [<matplotlib.lines.Line2D object at 0x6cef73d0>], [<matplotlib.lines.Line2D object at 0x6cef7690>], [<matplotlib.lines.Line2D object at 0x6cef7950>], [<matplotlib.lines.Line2D object at 0x6cef7c10>], [<matplotlib.lines.Line2D object at 0x6cef7ed0>], [<matplotlib.lines.Line2D object at 0x6ce811b0>], [<matplotlib.lines.Line2D object at 0x6ce81470>], [<matplotlib.lines.Line2D object at 0x6ce81730>], [<matplotlib.lines.Line2D object at 0x6ce819f0>], [<matplotlib.lines.Line2D object at 0x6ce81cb0>], [<matplotlib.lines.Line2D object at 0x6ce81f70>], [<matplotlib.lines.Line2D object at 0x6ce8a250>], [<matplotlib.lines.Line2D object at 0x6ce8a510>], [<matplotlib.lines.Line2D object at 0x6ce8a7d0>], [<matplotlib.lines.Line2D object at 0x6ce8aa90>], [<matplotlib.lines.Line2D object at 0x6ce8ad50>], [<matplotlib.lines.Line2D object at 0x6ce93030>], [<matplotlib.lines.Line2D object at 0x6ce932f0>], [<matplotlib.lines.Line2D object at 0x6ce935b0>], [<matplotlib.lines.Line2D object at 0x6ce93870>], [<matplotlib.lines.Line2D object at 0x6ce93b30>], [<matplotlib.lines.Line2D object at 0x6ce93df0>]] >>>
怎知在『筆記本』環境下,卻『無圖』也☻
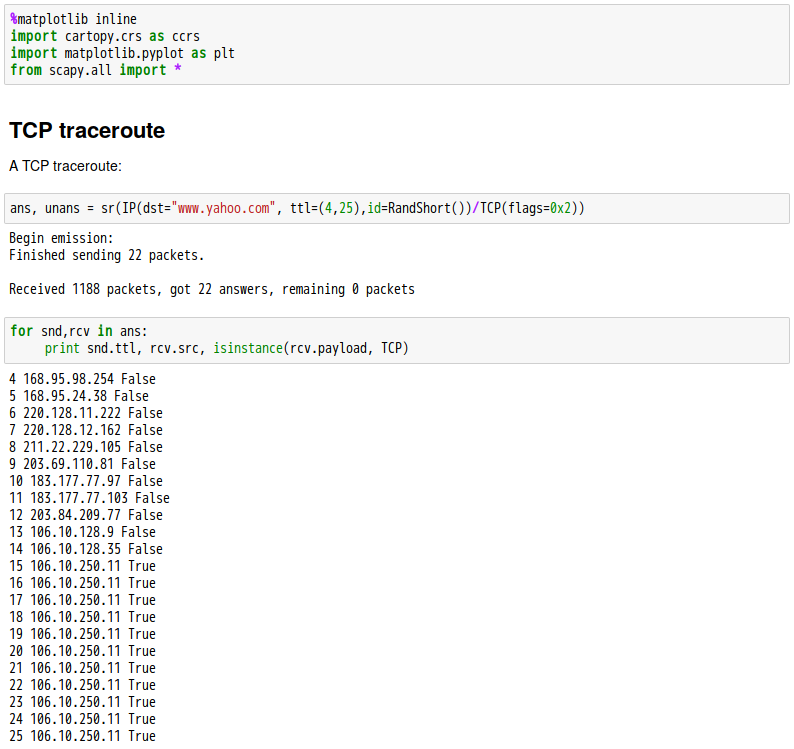
幾經『推敲』,多次閱讀『原始碼』,發現
ax.remove()
被擦掉了啊★
修正之後
def world_trace(self):
"""Display traceroute results on a world map."""
# Check that the geoip2 module can be imported
# Doc: http://geoip2.readthedocs.io/en/latest/
try:
# GeoIP2 modules need to be imported as below
import geoip2.database
import geoip2.errors
except ImportError:
ax.add_collection(line_col)
# Create map points
lines.extend([ax.plot(*x, marker='.', color=color) for x in trc])
# Generate legend
ax.legend()
# Call show() if matplotlib is not inlined
if not MATPLOTLIB_INLINED:
plt.show()
※ 修正
###
ax.remove()
# Clean
# ax.remove()
###
# Return the drawn lines
return lines
實出現其後的矣☆