三十三章
知人者智,自知者明。知人者,智而已矣,未若自知者超智之上也。 勝人者有力,自勝者強。勝人者,有力而已矣,未若自勝者無物以損其力,用其智於人,未若用其智於己也。用其力於人,未若用其力於己也。明用於己,則物無避焉,力用於己,則物無改焉。 知足者富。知足自不失,故富也。 強行者有志 。勤能行之,其志必獲,故曰強行者有志矣。 不失其所者久。以明自察,量力而行,不失其所,必獲久長矣。 死而不亡者壽。雖死而以為生之道不亡,乃得全其壽,身沒而道猶存,況身存而道不卒乎。
史實與小說不同,其人其事果能全真乎?
周伯通,金朝山東寧海(今山東牟平)人,知名全真道居士。
史實
王重陽始創全真道時曾受其資助。周伯通是全真道北七真中馬鈺、譚處端、王處一、郝大通、孫不二的同鄉。當時在寧海、文登等地傳道的王重陽先後收了丘處機、譚處端、馬鈺、王處一、郝大通為徒。1169年春(金大定九年巳丑四月),王重陽帶領馬、譚、丘、郝四弟子回到寧海,周伯通築庵請王重陽居住,名曰「金蓮堂」。不久馬鈺的妻子孫不二也在金蓮堂出家。八月,王重陽在金蓮堂成立「三教金蓮會」。隨後王重陽赴福山、登州、萊州等地繼續傳道 ,收劉處玄。
金庸武俠小說裡的周伯通
在金庸的《射鵰英雄傳》及《神鵰俠侶》中,周伯通被演繹為王重陽(書中為「天下五絕」之首,有「中神通」之號)的師弟,全真七子的師叔。為金庸小說中武功最絕頂的高手之一。 周伯通滿臉花影,髮鬚烏黑,雖然甚長,卻未見斑白。
生平
周伯通天性純真, 又如孩童般任意妄為,常不看場面緩急狀況下胡鬧,故有「老頑童」之稱。他不拘小節,好武成癡,當被生平未見的武功吸引時,有甘願向施功者磕頭拜師求教的舉動。(如初見歐陽鋒施展的輕功、郭靖所練的降龍十八掌、楊過獨創的黯然銷魂掌等)。
與晚輩郭靖(《射鵰英雄傳》男主角)結拜為兄弟。
天生是個樂天派,喜歡無拘無束地玩;雖未隨王重陽出家入道,卻在全真道門內深得道家養生要旨,長壽有道,逍遙自在地生活在天地之間。
武功方面,周伯通早已不下於「天下五絕」,後來因自創絕學「空明拳」、「雙手互搏」令他的武功早與「天下五絕」不相伯仲,於教授郭靖上下卷《九陰真經》時不知不覺間習得,令他武功近乎天下第一,大概已頗不下於其師兄王重陽。於《神鵰俠侶》結尾時,繼承師兄王重陽「中神通」地位得「中頑童」之號,成為了「天下五絕」之首。
周伯通之『空明拳』能『雙手互搏』,一心二用至忘我一人之境 ,是否為『自勝者』耶?因此說其得道家養生要旨,豈是全假呢! ! ??不講相機軟件,反倒先講起武俠,不會太無厘頭的嗎??!!
─── 《樹莓派相機︰ RASPICAM 之軟件《二》》
有容乃大俠客情,含笑駕鶴倚天飛。
有容乃大俠客情,
無慾則剛論政壇,
看破放下五蘊空,
含笑駕鶴倚天飛。
查傳倜
十月三十日,金庸“下午走了,很安详!”
寫故事的人走了,故事在◎

查良鏞於2007年7月
查良鏞,GBM ,OBE(英語:Louis Cha Jing-yong[2][註 1],1924年3月10日[3]-2018年10月30日[4]),男,筆名金庸,浙江海寧人,武俠小說泰斗,1948年移居香港。自1950年代起,其以筆名「金庸」創作多部膾炙人口的武俠小說,包括《射鵰英雄傳》、《神鵰俠侶》、《倚天屠龍記》、《天龍八部》、《笑傲江湖》、《鹿鼎記》等。歷年來金庸筆下的著作屢次改編為電視劇、電影等影視作品,對華人影視文化可謂貢獻重大。這亦奠定其成為華人知名作家的基礎,素有「有華人的地方,就有金庸的武俠」的稱讚。金庸早年於香港創辦《明報》系列報刊,並在1980年代涉足政界,曾任香港基本法起草委員會委員[5][6]。他因其優秀的小說作品而被稱為「香港四大才子」之一[7],後與古龍、梁羽生合稱為「中國武俠小說三劍客」。2018年10月30日下午,金庸於香港養和醫院逝世,享壽94歲[8]。
所謂伯通頑童心,招招是好招,就講點 OpenWrt 裡安裝 scapy ︰
root@LEDE:~# opkg update
root@LEDE:~# opkg upgrade
root@LEDE:~# opkg install python tcpdump unzip
root@LEDE:~# wget https://github.com/secdev/scapy/archive/master.zip
root@LEDE:~# unzip master
root@LEDE:~# cd scapy-master/
root@LEDE:~# python setup.py install
root@LEDE:~# rm master
耍耍 tcpdump 吧︰
【一終端機,先跑】
tcpdump -i lo -nn
root@LEDE:~# tcpdump -i lo -nn
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on lo, link-type EN10MB (Ethernet), capture size 262144 bytes
16:48:06.314949 IP6 ::1.60058 > ::1.22: Flags [S], seq 4222582636, win 43690, options [mss 65476,sackOK,TS val 27022763 ecr 0,nop,wscale 7], length 0
16:48:06.315538 IP6 ::1.22 > ::1.60058: Flags [S.], seq 1109362750, ack 4222582637, win 43690, options [mss 65476,sackOK,TS val 27022763 ecr 27022763,nop,wscale 7], length 0
16:48:06.316038 IP6 ::1.60058 > ::1.22: Flags [.], ack 1, win 342, options [nop,nop,TS val 27022763 ecr 27022763], length 0
16:48:06.316459 IP6 ::1.60058 > ::1.22: Flags [P.], seq 1:371, ack 1, win 342, options [nop,nop,TS val 27022763 ecr 27022763], length 370
16:48:06.316987 IP6 ::1.22 > ::1.60058: Flags [.], ack 371, win 350, options [nop,nop,TS val 27022763 ecr 27022763], length 0
16:48:06.320072 IP6 ::1.22 > ::1.60058: Flags [P.], seq 1:323, ack 371, win 350, options [nop,nop,TS val 27022764 ecr 27022763], length 322
16:48:06.320557 IP6 ::1.60058 > ::1.22: Flags [.], ack 323, win 350, options [nop,nop,TS val 27022764 ecr 27022764], length 0
16:48:06.625534 IP6 ::1.22 > ::1.60058: Flags [P.], seq 323:947, ack 371, win 350, options [nop,nop,TS val 27022794 ecr 27022764], length 624
16:48:06.626046 IP6 ::1.60058 > ::1.22: Flags [.], ack 947, win 360, options [nop,nop,TS val 27022794 ecr 27022794], length 0
16:48:09.202957 IP6 ::1.60058 > ::1.22: Flags [P.], seq 371:387, ack 947, win 360, options [nop,nop,TS val 27023052 ecr 27022794], length 16
16:48:09.203326 IP6 ::1.60058 > ::1.22: Flags [P.], seq 387:507, ack 947, win 360, options [nop,nop,TS val 27023052 ecr 27022794], length 120
16:48:09.203895 IP6 ::1.22 > ::1.60058: Flags [P.], seq 947:999, ack 507, win 350, options [nop,nop,TS val 27023052 ecr 27023052], length 52
16:48:09.204403 IP6 ::1.22 > ::1.60058: Flags [P.], seq 999:1067, ack 507, win 350, options [nop,nop,TS val 27023052 ecr 27023052], length 68
16:48:09.204473 IP6 ::1.60058 > ::1.22: Flags [.], ack 999, win 360, options [nop,nop,TS val 27023052 ecr 27023052], length 0
16:48:09.204945 IP6 ::1.60058 > ::1.22: Flags [.], ack 1067, win 360, options [nop,nop,TS val 27023052 ecr 27023052], length 0
16:48:24.264957 IP6 ::1.60058 > ::1.22: Flags [P.], seq 507:591, ack 1067, win 360, options [nop,nop,TS val 27024558 ecr 27023052], length 84
16:48:24.271341 IP6 ::1.22 > ::1.60058: Flags [P.], seq 1067:1103, ack 591, win 350, options [nop,nop,TS val 27024559 ecr 27024558], length 36
16:48:24.271827 IP6 ::1.60058 > ::1.22: Flags [.], ack 1103, win 360, options [nop,nop,TS val 27024559 ecr 27024559], length 0
16:48:24.272188 IP6 ::1.60058 > ::1.22: Flags [P.], seq 591:659, ack 1103, win 360, options [nop,nop,TS val 27024559 ecr 27024559], length 68
16:48:24.272763 IP6 ::1.22 > ::1.60058: Flags [P.], seq 1103:1155, ack 659, win 350, options [nop,nop,TS val 27024559 ecr 27024559], length 52
16:48:24.273508 IP6 ::1.60058 > ::1.22: Flags [P.], seq 659:1051, ack 1155, win 360, options [nop,nop,TS val 27024559 ecr 27024559], length 392
16:48:24.279439 IP6 ::1.22 > ::1.60058: Flags [P.], seq 1155:1255, ack 1051, win 359, options [nop,nop,TS val 27024560 ecr 27024559], length 100
16:48:24.282828 IP6 ::1.22 > ::1.60058: Flags [P.], seq 1255:1755, ack 1051, win 359, options [nop,nop,TS val 27024560 ecr 27024559], length 500
16:48:24.283519 IP6 ::1.60058 > ::1.22: Flags [.], ack 1755, win 370, options [nop,nop,TS val 27024560 ecr 27024560], length 0
16:48:24.294540 IP6 ::1.22 > ::1.60058: Flags [P.], seq 1755:1807, ack 1051, win 359, options [nop,nop,TS val 27024561 ecr 27024560], length 52
16:48:24.328406 IP6 ::1.60058 > ::1.22: Flags [.], ack 1807, win 370, options [nop,nop,TS val 27024565 ecr 27024561], length 0
【另一終端機,後跑】
ssh localhost
root@LEDE:~# ssh localhost
Host 'localhost' is not in the trusted hosts file.
(ssh-rsa fingerprint md5 2c:65:ec:d9:30:65:91:36:d8:4c:bd:75:0a:b1:ed:23)
Do you want to continue connecting? (y/n) y
root@localhost's password:
BusyBox v1.25.1 () built-in shell (ash)
_________
/ /\ _ ___ ___ ___
/ LE / \ | | | __| \| __|
/ DE / \ | |__| _|| |) | _|
/________/ LE \ |____|___|___/|___| lede-project.org
\ \ DE /
\ LE \ / -----------------------------------------------------------
\ DE \ / Reboot (17.01.6, r3979-2252731af4)
\________\/ -----------------------------------------------------------
root@LEDE:~#
再次參讀《鳥哥的 Linux 私房菜》文字,自得其中味也!
 5.5 封包擷取功能
5.5 封包擷取功能
很多時候由於我們的網路連線出現問題,使用類似 ping 的軟體功能卻又無法找出問題點,最常見的是因為路由與 IP 轉遞後所產生的一些困擾 (請參考防火牆與 NAT 主機部分),這個時候要怎麼辦?最簡單的方法就是『分析封包的流向』囉!透過分析封包的流向,我們可以瞭解一條連線應該是如何進行雙向的連線的動作, 也就會清楚的瞭解到可能發生的問題所在了!底下我們就來談一談這個 tcpdump 與圖形介面的封包分析軟體吧!
 5.5.1 文字介面封包擷取器: tcpdump
5.5.1 文字介面封包擷取器: tcpdump
說實在的,對於 tcpdump 這個軟體來說,你甚至可以說這個軟體其實就是個駭客軟體, 因為他不但可以分析封包的流向,連封包的內容也可以進行『監聽』, 如果你使用的傳輸資料是明碼的話,不得了,在 router 或 hub 上面就可能被人家監聽走了! 我們在第二章談到的 CSMA/CD 流程中,不是說過有所謂的『監聽軟體』嗎?這個 tcpdump 就是啦! 很可怕吶!所以,我們也要來瞭解一下這個軟體啊!(註:這個 tcpdump 必須使用 root 的身份執行)
[root@www ~]# tcpdump [-AennqX] [-i 介面] [-w 儲存檔名] [-c 次數] \
[-r 檔案] [所欲擷取的封包資料格式]
選項與參數:
-A :封包的內容以 ASCII 顯示,通常用來捉取 WWW 的網頁封包資料。
-e :使用資料連接層 (OSI 第二層) 的 MAC 封包資料來顯示;
-nn:直接以 IP 及 port number 顯示,而非主機名與服務名稱
-q :僅列出較為簡短的封包資訊,每一行的內容比較精簡
-X :可以列出十六進位 (hex) 以及 ASCII 的封包內容,對於監聽封包內容很有用
-i :後面接要『監聽』的網路介面,例如 eth0, lo, ppp0 等等的介面;
-w :如果你要將監聽所得的封包資料儲存下來,用這個參數就對了!後面接檔名
-r :從後面接的檔案將封包資料讀出來。那個『檔案』是已經存在的檔案,
並且這個『檔案』是由 -w 所製作出來的。
-c :監聽的封包數,如果沒有這個參數, tcpdump 會持續不斷的監聽,
直到使用者輸入 [ctrl]-c 為止。
所欲擷取的封包資料格式:我們可以專門針對某些通訊協定或者是 IP 來源進行封包擷取,
那就可以簡化輸出的結果,並取得最有用的資訊。常見的表示方法有:
'host foo', 'host 127.0.0.1' :針對單部主機來進行封包擷取
'net 192.168' :針對某個網域來進行封包的擷取;
'src host 127.0.0.1' 'dst net 192.168':同時加上來源(src)或目標(dst)限制
'tcp port 21':還可以針對通訊協定偵測,如 tcp, udp, arp, ether 等
還可以利用 and 與 or 來進行封包資料的整合顯示呢!
# 範例一:以 IP 與 port number 捉下 eth0 這個網路卡上的封包,持續 3 秒
[root@www ~]# tcpdump -i eth0 -nn
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on eth0, link-type EN10MB (Ethernet), capture size 65535 bytes
17:01:47.360523 IP 192.168.1.101.1937 > 192.168.1.100.22: Flags [.], ack 196, win 65219,
17:01:47.362139 IP 192.168.1.100.22 > 192.168.1.101.1937: Flags [P.], seq 196:472, ack 1,
17:01:47.363201 IP 192.168.1.100.22 > 192.168.1.101.1937: Flags [P.], seq 472:636, ack 1,
17:01:47.363328 IP 192.168.1.101.1937 > 192.168.1.100.22: Flags [.], ack 636, win 64779,
<==按下 [ctrl]-c 之後結束
6680 packets captured <==捉下來的封包數量
14250 packets received by filter <==由過濾所得的總封包數量
7512 packets dropped by kernel <==被核心所丟棄的封包
|
如果你是第一次看 tcpdump 的 man page 時,肯定一個頭兩個大,因為 tcpdump 幾乎都是分析封包的表頭資料,使用者如果沒有簡易的網路封包基礎,要看懂粉難吶! 所以,至少你得要回到網路基礎裡面去將 TCP 封包的表頭資料理解理解才好啊! ^_^!至於那個範例一所產生的輸出範例中,我們可以約略區分為數個欄位, 我們以範例一當中那個特殊字體行來說明一下:
- 17:01:47.362139:這個是此封包被擷取的時間,『時:分:秒』的單位;
- IP:透過的通訊協定是 IP ;
- 192.168.1.100.22 > :傳送端是 192.168.1.100 這個 IP,而傳送的 port number 為 22,你必須要瞭解的是,那個大於 (>) 的符號指的是封包的傳輸方向喔!
- 192.168.1.101.1937:接收端的 IP 是 192.168.1.101, 且該主機開啟 port 1937 來接收;
- [P.], seq 196:472:這個封包帶有 PUSH 的資料傳輸標誌, 且傳輸的資料為整體資料的 196~472 byte;
- ack 1:ACK 的相關資料。
最簡單的說法,就是該封包是由 192.168.1.100 傳到 192.168.1.101,透過的 port 是由 22 到 1937 , 使用的是 PUSH 的旗標,而不是 SYN 之類的主動連線標誌。呵呵!不容易看的懂吧!所以說,上頭才講請務必到 TCP 表頭資料的部分去瞧一瞧的啊!
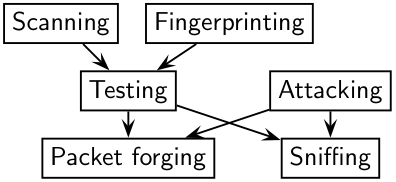
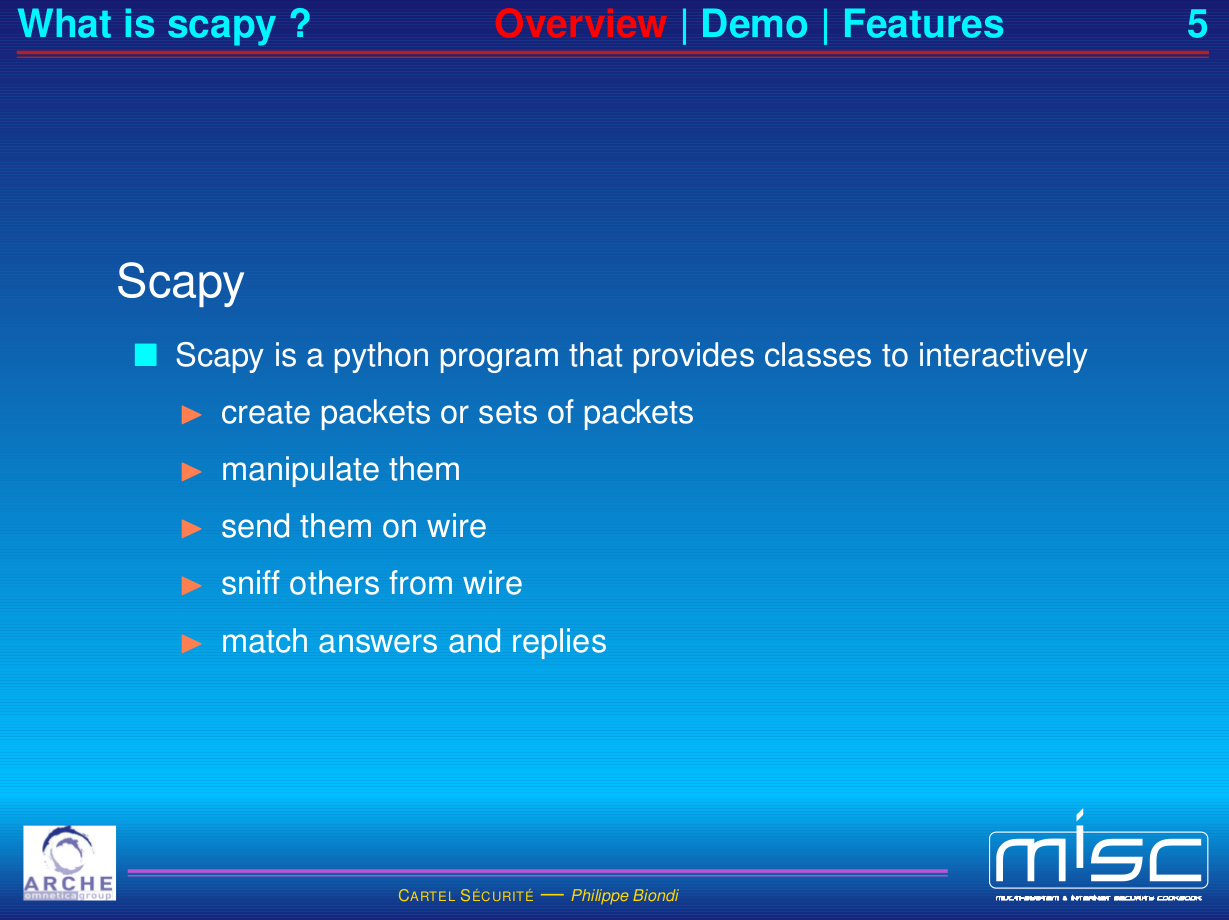
自會興起修煉 Scapy 心法之念乎?
Usage
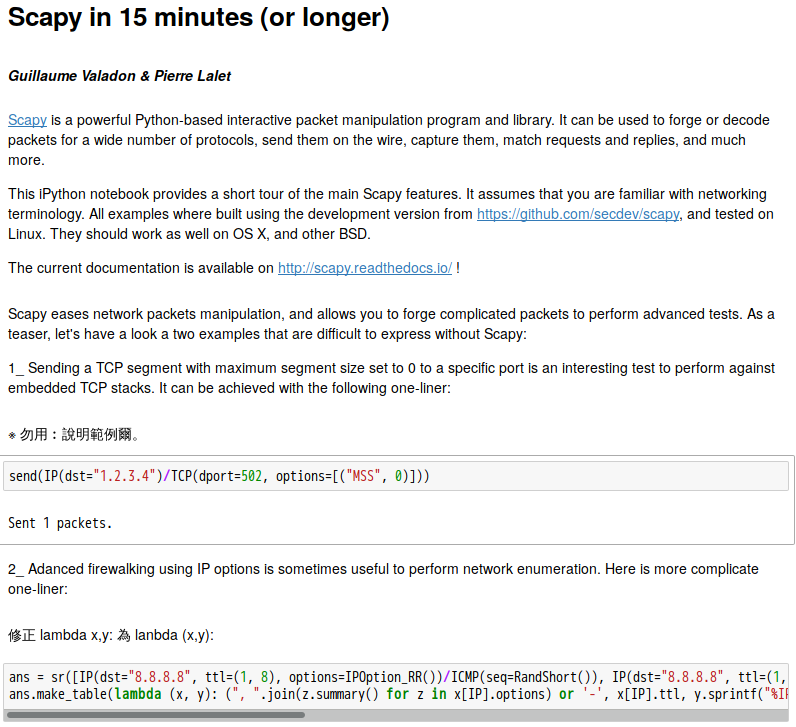
Scapy’s interactive shell is run in a terminal session. Root privileges are needed to send the packets, so we’re using sudo here:
root@LEDE:~# python
Python 2.7.14 (default, Aug 17 2018, 14:24:19)
[GCC 5.4.0] on linux2
Type "help", "copyright", "credits" or "license" for more information.
>>> from scapy.all import *
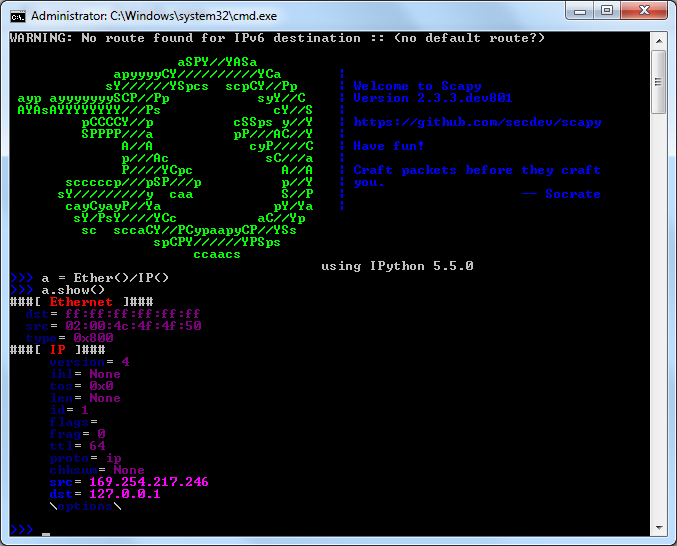
>>> a=IP(ttl=10)
>>> a
<IP ttl=10 |>
>>> a.src
'127.0.0.1'
>>> a.dst="192.168.1.1"
>>> a
<IP ttl=10 dst=192.168.1.1 |>
>>> a.src
'192.168.11.6'
>>> del(a.ttl)
>>> a
<IP dst=192.168.1.1 |>
>>> a.ttl
64
>>>
root@LEDE:~# ifconfig
br-lan Link encap:Ethernet HWaddr B8:27:EB:8C:82:7A
inet addr:5.168.166.88 Bcast:5.168.166.255 Mask:255.255.255.0
inet6 addr: fd42:80c5:b618::1/60 Scope:Global
inet6 addr: fe80::ba27:ebff:fe8c:827a/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:380 errors:0 dropped:0 overruns:0 frame:0
TX packets:997 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:73846 (72.1 KiB) TX bytes:339688 (331.7 KiB)
br-wan Link encap:Ethernet HWaddr B8:27:EB:D9:D7:2F
inet addr:5.168.168.20 Bcast:5.168.168.255 Mask:255.255.255.0
inet6 addr: fe80::ba27:ebff:fed9:d72f/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:10834179 errors:0 dropped:135684 overruns:0 frame:0
TX packets:10975069 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:955251837 (910.9 MiB) TX bytes:1078967781 (1.0 GiB)
eth0 Link encap:Ethernet HWaddr B8:27:EB:D9:D7:2F
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:10834440 errors:0 dropped:0 overruns:0 frame:0
TX packets:10975069 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:955271954 (911.0 MiB) TX bytes:1204429761 (1.1 GiB)
eth1 Link encap:Ethernet HWaddr 00:0E:C6:81:79:01
inet addr:5.168.128.66 Bcast:5.168.128.255 Mask:255.255.255.0
inet6 addr: fe80::20e:c6ff:fe81:7901/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:8 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:1224 (1.1 KiB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:128 errors:0 dropped:0 overruns:0 frame:0
TX packets:128 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1
RX bytes:14784 (14.4 KiB) TX bytes:14784 (14.4 KiB)
wlan0 Link encap:Ethernet HWaddr B8:27:EB:8C:82:7A
inet6 addr: fe80::ba27:ebff:fe8c:827a/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:380 errors:0 dropped:0 overruns:0 frame:0
TX packets:1195 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:73846 (72.1 KiB) TX bytes:398848 (389.5 KiB)
wlan1 Link encap:Ethernet HWaddr E8:4E:06:4F:C5:5C
inet addr:192.168.11.6 Bcast:192.168.11.255 Mask:255.255.255.0
inet6 addr: fe80::ea4e:6ff:fe4f:c55c/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:15841 errors:0 dropped:0 overruns:0 frame:0
TX packets:7172 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:7513885 (7.1 MiB) TX bytes:699124 (682.7 KiB)
root@LEDE:~#
 (dirname
(dirname 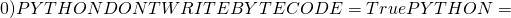 {PYTHON:-python}
PYTHONPATH=
{PYTHON:-python}
PYTHONPATH=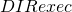 PYTHON -m scapy $@
PYTHON -m scapy $@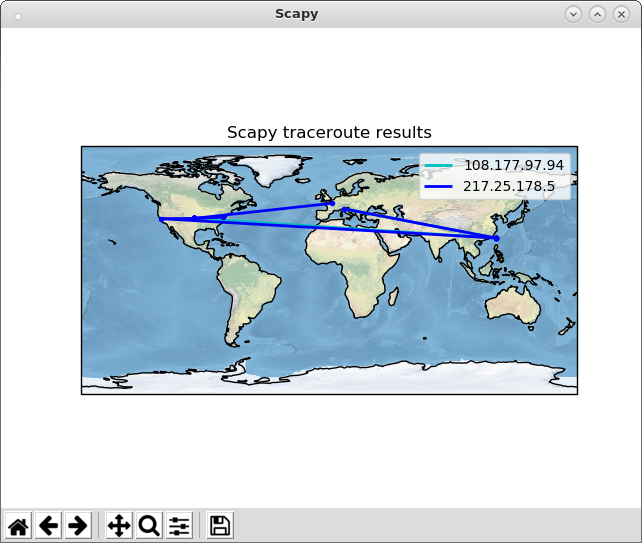











![[Security Power Tools cover]](http://www.secdev.org/images/security_power_tools-cover.gif)

_2.png)

