哲學家曾經認為人類是自然界中唯一會使用『工具』的動物。雖說已知不是,不過能把『工具』當『武器』,『武器』作『工具』者其為人類乎?故而依今日名義, M♪o 當時所遇『駭黑』者
![]() 派︰聽聞學長說,實習機器故障,所以停課。也常常上課不實習。故不故障、上不上課、實不實習,豈關聯!事出必有因,費疑猜!!
派︰聽聞學長說,實習機器故障,所以停課。也常常上課不實習。故不故障、上不上課、實不實習,豈關聯!事出必有因,費疑猜!!
隨詠杜甫《奉先》五百字,準備考試。
<自京赴奉先詠懷五百字>
杜陵有布衣,老大意轉拙。許身一何愚,竊比稷與契。
居然成濩落,白首甘契闊。蓋棺事則已,此志常覬豁。
窮年憂黎元,嘆息腸內熱。取笑同學翁,浩歌彌激烈。
非無江海志,蕭灑送日月。生逢堯舜君,不忍便永訣。
當今廊廟具,構廈豈雲缺 ?葵藿傾太陽,物性固莫奪。
顧惟螻蟻輩,但自求其穴。胡為慕大鯨,輒擬偃溟渤 ?
以茲悟生理,獨恥事幹謁。兀兀遂至今,忍為塵埃沒。
終愧巢與由,未能易其節。沈飲聊自遣,放歌破愁絕。
歲暮百草零,疾風高岡裂。天衢陰崢嶸,客子中夜發。
霜嚴衣帶斷,指直不得結。淩晨過驪山,禦榻在嵽嵲。
蚩尤塞寒空,蹴踏崖谷滑。瑤池氣鬱律,羽林相摩戛。
君臣留歡娛,樂動殷膠葛。賜浴皆長纓,與宴非短褐。
彤庭所分帛,本自寒女出。鞭撻其夫家,聚斂貢城闕。
聖人筐篚恩,實欲邦國活。多士盈朝廷,仁者宜戰栗。
況聞內金盤,盡在衛霍室。中堂有神仙,煙霧蒙玉質。
煖客貂鼠裘,悲管逐清瑟。勸客駝蹄羹,霜橙壓香橘。
朱門酒肉臭,路有凍死骨。榮枯咫尺異,惆悵難再述。
北轅就涇渭,官渡又改轍。群冰從西下,極目高崒兀。
疑是崆峒來,恐觸天柱折。河梁幸未坼,枝撐聲窸窣。
行李相攀援,川廣不可越。老妻寄異縣,十口隔風雪。
誰能久不顧,庶往共飢渴。入門聞號咷,幼子餓已卒。
吾寧舍一哀,裏巷亦嗚咽。所愧為人父,無食致夭折。
豈知秋禾登,貧窶有倉卒。生常免租稅,名不隸征伐。
撫跡猶酸辛,平人固騷屑。默思失業徒,因念遠戍卒。
憂端齊終南,澒洞不可掇。
阡陌縱橫之網,匪夷所思,強迫而譯,難以釋懷。或想『阡』蓋為『發訊方』吧!苦於無處可考,特以為記。
因此再問學長,得知有人闖入機房,透過《通訊口》駭入,黑除了主機資料,正在搶救中。這事不可多言,以免引起驚慌。云云…
看來是要息事寧人,不了了之的了!?
── 摘自《M♪o 之學習筆記本《寅》井井︰【青木春】驚駭來黑》
,應稱之為『劊客』的吧!
直到現今,以其『精神』以及『目的』之不同,所謂『分類』
Classifications
Several subgroups of the computer underground with different attitudes use different terms to demarcate themselves from each other, or try to exclude some specific group with whom they do not agree.
Eric S. Raymond, author of The New Hacker’s Dictionary, advocates that members of the computer underground should be called crackers. Yet, those people see themselves as hackers and even try to include the views of Raymond in what they see as a wider hacker culture, a view that Raymond has harshly rejected. Instead of a hacker/cracker dichotomy, they emphasize a spectrum of different categories, such as white hat, grey hat, black hat and script kiddie. In contrast to Raymond, they usually reserve the term cracker for more malicious activity.
According to Ralph D. Clifford, a cracker or cracking is to “gain unauthorized access to a computer in order to commit another crime such as destroying information contained in that system”.[16] These subgroups may also be defined by the legal status of their activities.[17]
White hat
A white hat hacker breaks security for non-malicious reasons, either to test their own security system, perform penetration tests or vulnerability assessments for a client – or while working for a security company which makes security software. The term is generally synonymous with ethical hacker, and the EC-Council,[18] among others, have developed certifications, courseware, classes, and online training covering the diverse arena of ethical hacking.[17]
Black hat
A “black hat” hacker is a hacker who “violates computer security for little reason beyond maliciousness or for personal gain” (Moore, 2005).[19] The term was coined by Richard Stallman, to contrast the maliciousness of a criminal hacker versus the spirit of playfulness and exploration in hacker culture, or the ethos of the white hat hacker who performs hacking duties to identify places to repair or as a means of legitimate employment.[20] Black hat hackers form the stereotypical, illegal hacking groups often portrayed in popular culture, and are “the epitome of all that the public fears in a computer criminal”.[21]
Grey hat
A grey hat hacker lies between a black hat and a white hat hacker. A grey hat hacker may surf the Internet and hack into a computer system for the sole purpose of notifying the administrator that their system has a security defect, for example. They may then offer to correct the defect for a fee.[21] Grey hat hackers sometimes find the defect of a system and publish the facts to the world instead of a group of people. Even though grey hat hackers may not necessarily perform hacking for their personal gain, unauthorized access to a system can be considered illegal and unethical.
Elite hacker
A social status among hackers, elite is used to describe the most skilled. Newly discovered exploits circulate among these hackers. Elite groups such as Masters of Deception conferred a kind of credibility on their members.[22]
Script kiddie
A script kiddie (also known as a skid or skiddie) is an unskilled hacker who breaks into computer systems by using automated tools written by others (usually by other black hat hackers), hence the term script (i.e. a prearranged plan or set of activities) kiddie (i.e. kid, child—an individual lacking knowledge and experience, immature),[23] usually with little understanding of the underlying concept.
Neophyte
A neophyte (“newbie“, or “noob”) is someone who is new to hacking or phreaking and has almost no knowledge or experience of the workings of technology and hacking.[21]
Blue hat
A blue hat hacker is someone outside computer security consulting firms who is used to bug-test a system prior to its launch, looking for exploits so they can be closed. Microsoft also uses the term BlueHat to represent a series of security briefing events.[24][25][26]
Hacktivist
A hacktivist is a hacker who utilizes technology to publicize a social, ideological, religious or political message.
Hacktivism can be divided into two main groups:
- Cyberterrorism — Activities involving website defacement or denial-of-service attacks; and,
- Freedom of information — Making information that is not public, or is public in non-machine-readable formats, accessible to the public.
Nation state
Intelligence agencies and cyberwarfare operatives of nation states.[27]
Organized criminal gangs
Groups of hackers that carry out organized criminal activities for profit.[27]
尚且在意耶!!??
見於樹莓派 0W 之省電、行動電源之方便、手機之普遍,與『果味 』之豐盛︰
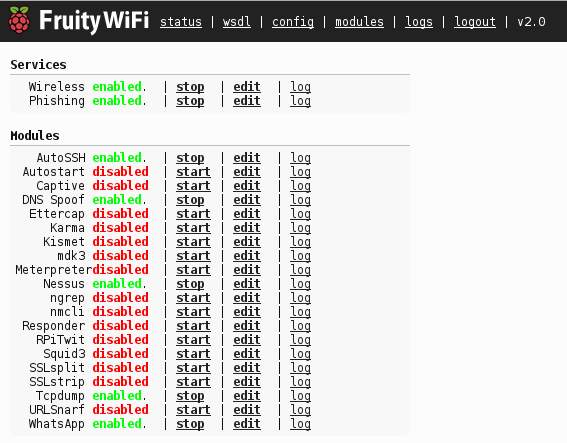
FruityWiFi
Wireless network auditing tool http://www.fruitywifi.com/
FruityWifi is an open source tool to audit wireless networks. It allows the user to deploy advanced attacks by directly using the web interface or by sending messages to it.
Initialy the application was created to be used with the Raspberry-Pi, but it can be installed on any Debian based system.
A more flexible control panel. Now it is possible to use FruityWifi combining multiple networks and setups:
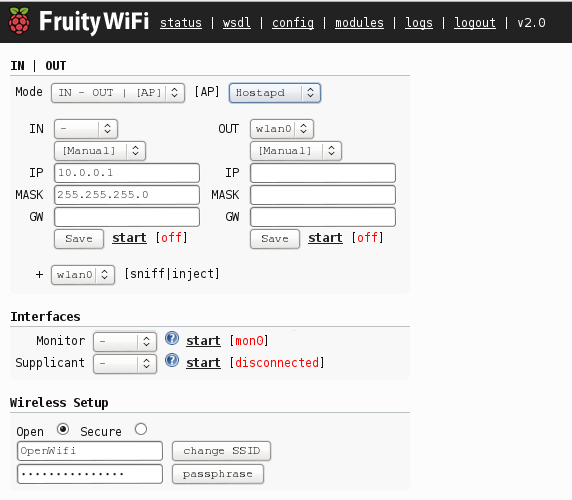
Within the new options on the control panel we can change the AP mode between Hostapd or Airmon-ng allowing to use more chipsets like Realtek.
It is possible customize each one of the network interfaces which allows the user to keep the current setup or change it completely.
FruityWifi is based on modules making it more flexible. These modules can be installed from the control panel to provide FruityWifi with new functionalities.
Within the available modules you can find URLsnarf, DNSspoof, Kismet, mdk3, ngrep, nmap, Squid3 y SSLstrip (code injection functionality), Captive Portal, AutoSSH, Meterpreter, Tcpdump and more.
Note: New modules are being developed continuously and can be installed from the modules page.
特此驗證之︰
ARM version (Raspberry Pi)
- You need a Raspbian, Pwnpi or Kali Linux version to use this script.
- Download the zip file from https://github.com/xtr4nge/FruityWifi/archive/master.zip
- Unzip the file and run install-FruityWifi.sh (This script will install all the dependencies and setups)
- Done.
Go to http://localhost:8000 (for http)
Go to https://localhost:8443 (for https)
user: admin
pass: admin
More information
.png)
以饗讀者。若問『功夫』和『修煉』之事,靠自己嘍☆